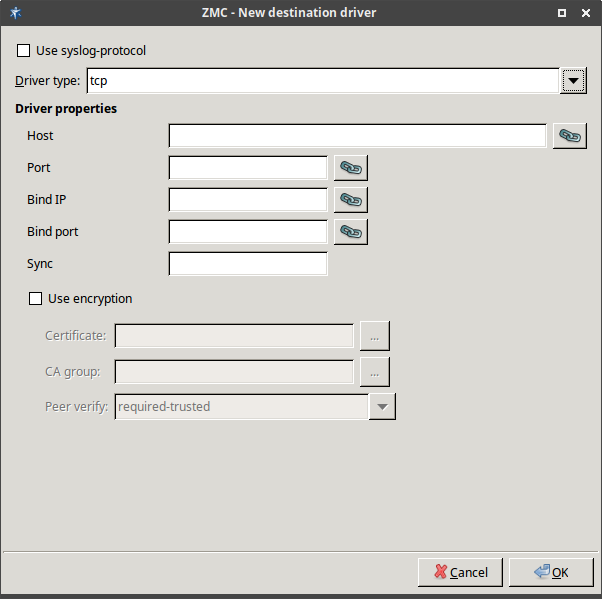
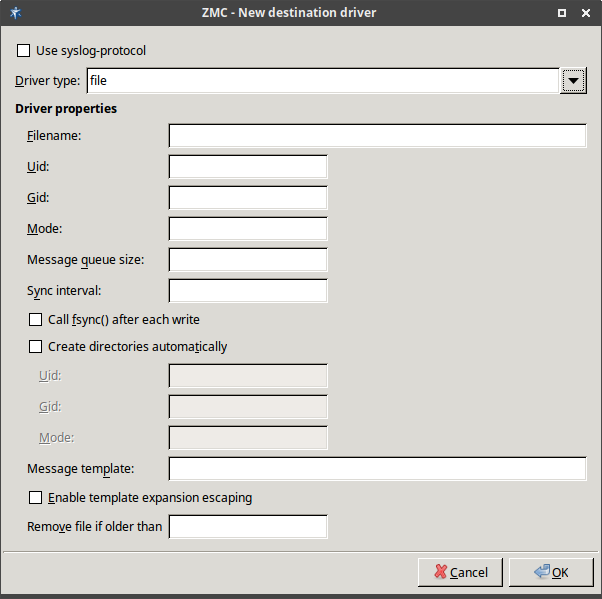
The logic behind destination configuration is the same as with sources' configuration. You can create one or more destination directives and fill them with drivers specifying the actual channels on which log messages are recorded.
The available destinations are the following:
file
syslog: TCP, UDP, or TLS-encrypted TCP through the RFC5424 (IETF-syslog) protocol
TCP through the RFC3164 (BSD-syslog or legacy-syslog) protocol, including TLS-encrypted TCP
UDP through the RFC3164 (BSD-syslog or legacy-syslog) protocol
pipe
program
Program specifies the input of a software, typically a script, that can perform an action based on the input log message it receives.
Tip This may be a good solution to set up an alerting mechanism.
Unix_dgram
Unix_stream
Usertty
Usertty is a terminal to which log messages can be displayed; it is meaningful as a destination if there is someone actually monitoring that terminal, or the named terminal is routed to some other, special destination.
and define the destination of log messages on the network, while and specify where (in which direction) the log messages are sent out from the host. This is especially important for firewalls which almost always have two or more interfaces and a number of IP addresses.
Additional parameter configuration options are as follows:
Use ancryption: If this option is enabled, a TLS-encrypted channel is used.
Certificate: It specifies the certificate used to authenticate the syslog-ng client on the destination server.
CA group: It specifies the CA group to verify peer certificates.
Peer verify: This option defines the verification method of the peer.
File destination also has some important properties that need some explanation:
Most properties are present also on the tab: many of the global options can be overridden in file destination setup. For the descriptions of the properties, see section Section 7.1.1, Global options.
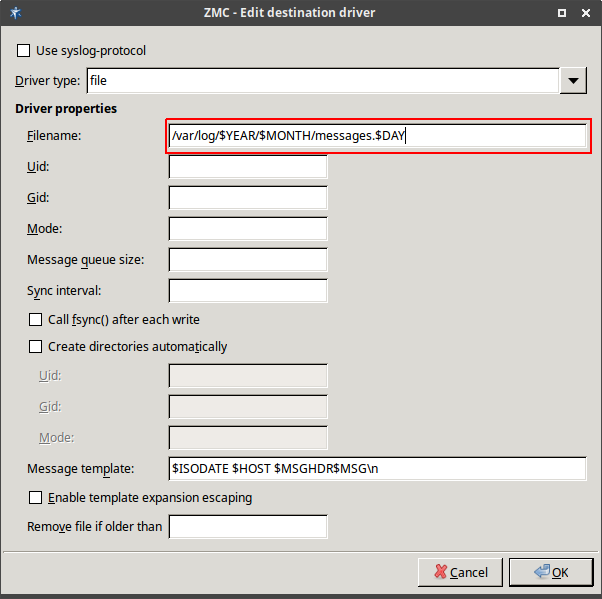
A special property is the . This property can be used to apply some basic formatting on log messages: according to the example given in Figure 7.11, Macro substitution in file naming, all log messages that end up in /var/log/syslog have a timestamp ($ISODATE) and a hostname ($HOST) inserted before the actual log message ($MSG). This is the default behavior in Zorp.
| Note |
|---|
The property is not to be confused with macro substitution in filename creation. Message templates can format actual log messages, while macro substitution can format log file names. |
For example, if you want to create a new logfile every day, modify the filename property in Figure 7.11, Macro substitution in file naming the following way.
Published on May 30, 2024
© BalaSys IT Ltd.
Send your comments to support@balasys.hu