4.1. Procedure – Bootstrap a new host
Purpose:
To bootsgrap a new host, complete the following steps.
Steps:
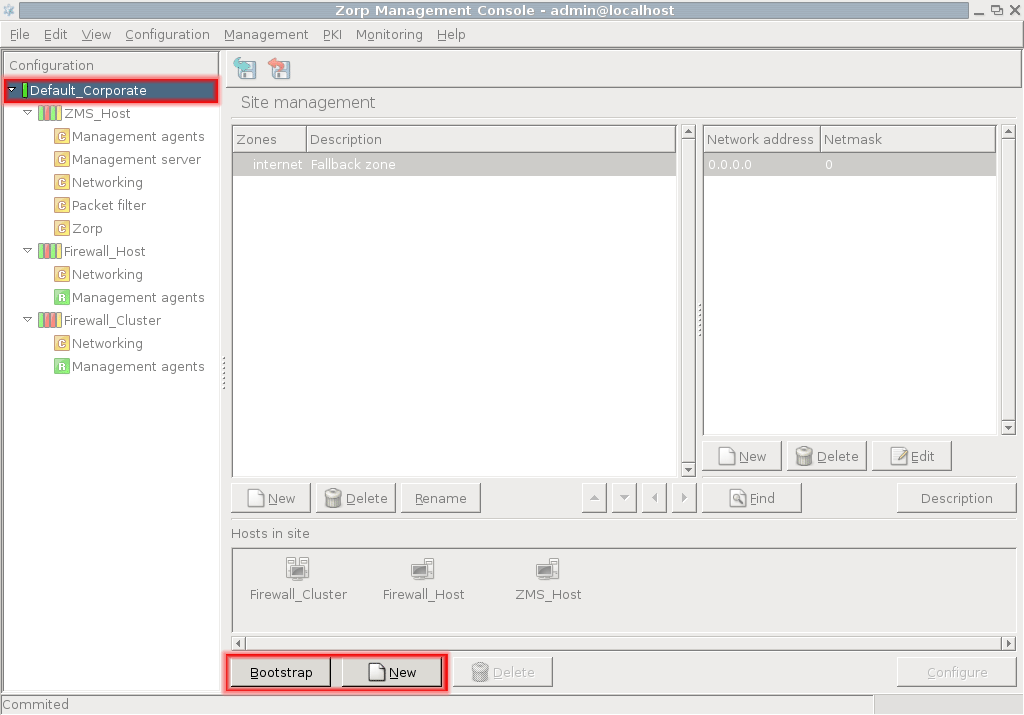
Select the desired site in the configuration tree.
Click at the bottom of the screen. This will start the wizard.
Note Alternatively, to register a host manually, click next to .
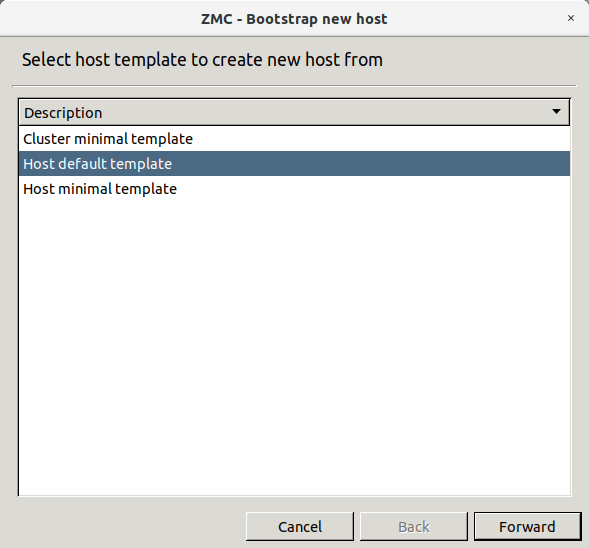
Select a host template.
The default templates are the following. New templates can be created later.
This tenplate can be used to configure clustered solutions.
This template can be used to add the , and components automatically to the tree under the name of the newly added host.
For details, see:
This template can be used to add only the two default components: and .
It is recommended to select the because it already has some components preconfigured.
Tip When working with several Zorp hosts it can be useful to create predefined templates, to save repetitive work. For details on creating templates manually, see Chapter 6, Managing network traffic with Zorp.
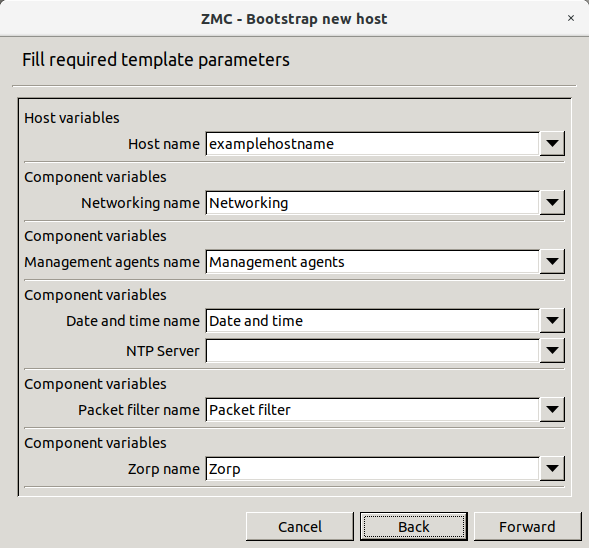
Enter the details of the new host.
: It is the name of the Zorp firewall.
: It is the name of the component.
: It is the name of the component.
: It is the name of the component.
: Specify a time server that Zorp synchronizes its system time with. Usually, but not necessarily it is an external time source. For the up-to-date list of publicly available time servers, see http://support.ntp.org/bin/view/Servers/WebHome. For more information on NTP, see Chapter 9, Native services.
: It is the name of the component.
: It is the name of the component.
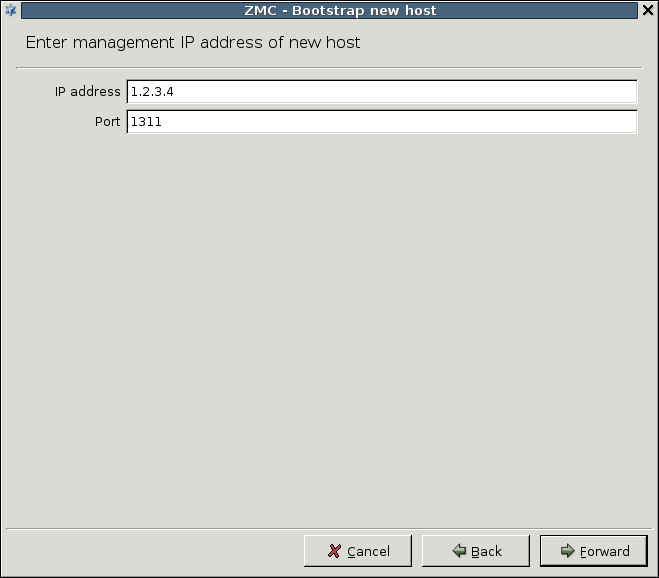
Enter the IP address and configuration port number of the Transfer agent.
Before starting, discover which network interface and IP address is reachable from the network location. Firewalls almost always have more than one of these. Ensure that the IP address typed in is reachable from the current location and that the packets will find their ways back from the firewall. In other words, make sure that all routing information is correctly configured.
YConfigure other interfaces of Zorp to be reachable for configuration purposes later.
Enter the .
Refer to the Firewall's installation documentation for the IP address information.
Leave the field default (
1311).
Create a certificate for SSL communication establishment.
Firewalls are administered from a protected, inside interface and while this method is highly recommended, it is not necessarily required. All the configuration traffic is encrypted, using SSL.
The administrative connection is encrypted using SSL, which requires a certificate, especially the public key it contains. This certificate and the private key used for encryption/decryption are sent to the Management agent on the firewall node that uses it to encrypt the session key it generates. For more information on SSL communication establishment, see Chapter 11, Key and certificate management in Zorp.
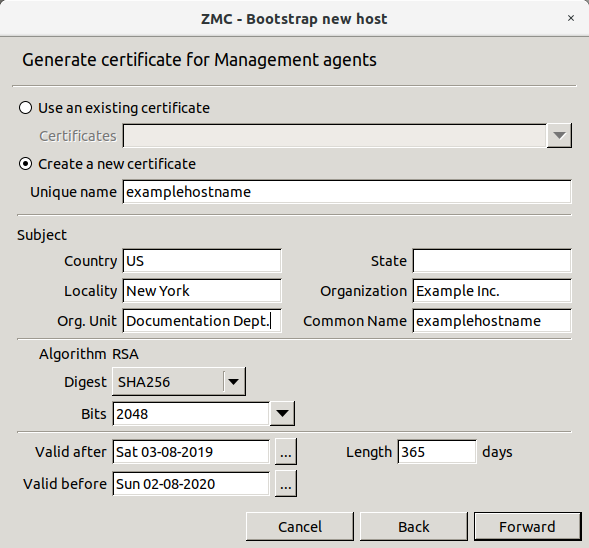
Enter the parameters of the certificate and it will be generated automatically.
To , enter a name for the certificate in the field. Alternatively, to , browse for a certificate from . The following steps describe the details of creating a new certificate.
Tip There are no particular requirements for the and fields other than trivial string length and restricted character issues. However, it is recommended to enter a name that will later — when there are more certificates in use in the system — uniquely and easily identify this certificate as the one used for establishing agent communication.
In the field, enter the two-character country code of the country where Zorp is located. For example, to refer to the United States, enter
US.Optional step: In the field, enter the state where Zorp is located, if applicable. For example,
California.In the field, enter the name of the city where Zorp is located. For example,
New York.In the field, enter the name of the company that owns Zorp. For example,
Example Inc..In the field, enter the department of the company that administers Zorp. For example,
IT Security.Enter a that describes you or your subdivision.
Alternatively, a default value can be used: the name of the Zorp firewall node.
Configure the RSA algorithm. Select whether to use
SHA-256orSHA-512. Select the asymmetric key length from the list.Note The U.S. National Institute for Standards and Technology (NIST) recommends
2048-bit keys for RSA.Configure the validity range of the certificate.
To select the start date from the field, click
 .
.To configure the validity range, either select the end date from the field by clicking
 or enter the validity in days and press Enter.
or enter the validity in days and press Enter.
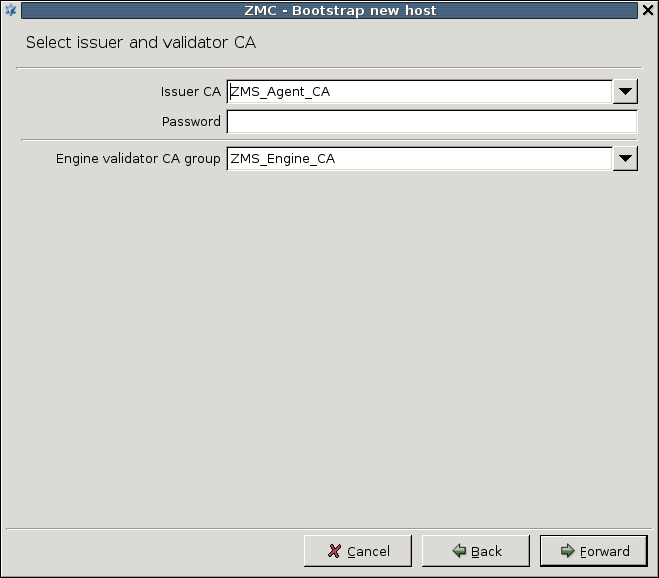
Enter the ZMS Agent CA password.
Manually entered passwords protect private keys against possible unauthorized accesses. Even if an attacker has read access to the hosts, the private keys cannot be stolen (read). These passwords are used to encrypt the private keys and therefore they are never stored in unencrypted format at all. Certificates are issued by Certificate Authorities (CA) and it is actually the CA's private key that requires this protection. The certificate used by the Management agents are issued by the ZMS_Agent_CA. Enter the password for this CA that was defined for this purpose when the ZMS service was installed. See also Chapter 11, Key and certificate management in Zorp.
Note To generate a strong password, it is recommended to use a password generator.
Tip Take detailed logs of the installation process, including the bootstraps where all these passwords are recorded.
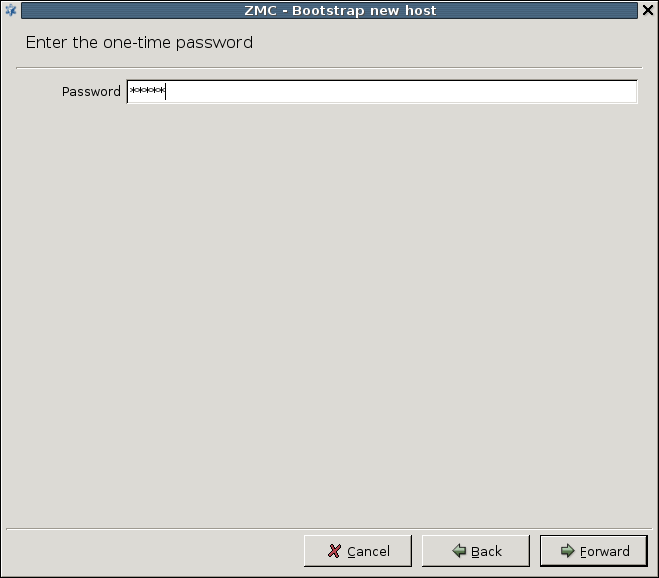
Enter the One-Time Password.
The is the one that has been entered during the installation of ZMS-transfer-agent on the Zorp host. It is a one-time operation: to establish an SSL channel between the Management agents of Zorp and the ZMS host, certificates are required. There are no certificates to use, therefore a certificate has to be provided for the ZMS-transfer-agent on Zorp, which can be used for communication channel buildup purposes. This password is used to establish a preliminary encrypted communication channel between Zorp and the ZMS host, where the certificate can be sent. All communication among the parties is performed using SSL.
Click the final button if all password phases have been successful to build up the connection.
The displayed logs provide information about the steps the wizard takes in the background. To save the output for later analysis, if needed, (either by the administrator or a support personnel), click .
Note If anything goes wrong, the wizard returns to the window where the mistake was made, so that it can be corrected.
After the bootstrap process has finished successfully, the new host is ready to be configured.
Published on May 30, 2024
© BalaSys IT Ltd.
Send your comments to support@balasys.hu