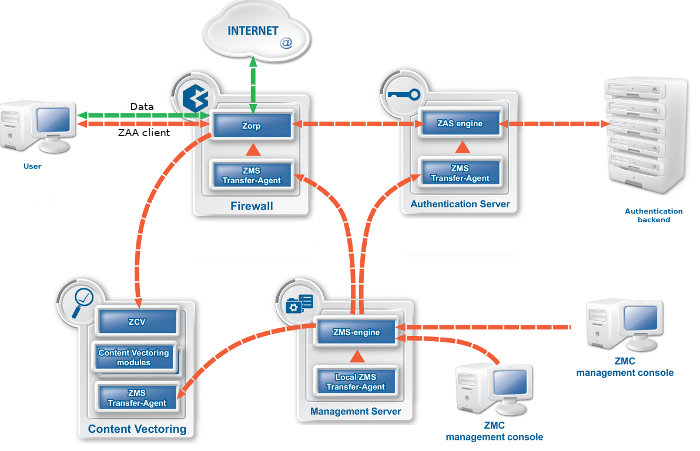
A typical PNS Gateway solution consists of the following components:
One or more PNS firewall hosts. Application-level Gateway is inspecting and analyzing all connections.
A Management Server (MS). MS is the central managing server of the PNS Gateway solution. MS stores the settings of every component, and generates the configuration files needed by the other components. A single MS can manage the configuration of several PNS firewalls — for example, if an organization has several separate facilities with their own firewalls, each of them can be managed from a central Management Server.
One or more desktop computers running the Management Console (MC), the graphical user interface of MS. The PNS administrators use this application to manage the entire system.
Transfer agents. These applications perform the communication between MS and the other components.
One or more Content Filtering (CF) servers. CF servers can inspect and filter the content of the network traffic, for example, using different virus- and spamfiltering modules. CF can inspect over 10 network protocols, including encrypted ones as well. For example, SMTP, HTTP, HTTPS, and so on.
One or more Authentication Server (AS). AS can authenticate every network connection of the clients to a variety of databases, including LDAP, RADIUS, or TACACS. Clients can also authenticate out-of-band using a separate authentication agent.
| Note |
|---|
| The name of the application effectively serving as the Application-level Gateway component of Proxedo Network Security Suite is Zorp, commands, paths and internal references will relate to that naming. |
The following figure shows how these components operate:
Published on June 04, 2020
© 2007-2019 BalaSys
Send your comments to support@balasys.hu