Each module available in CF has its own parameters that can be set separately for each module instance. Some of modules have global options that apply to all instances of that module, these are also described at the particular module.
The clamav module uses the Clam AntiVirus engine to examine incoming files. It supports only file mode and only detects infected files; it does not attempt to disinfect them. Starting with PNS 3.4, the module automatically scans archived files as well.
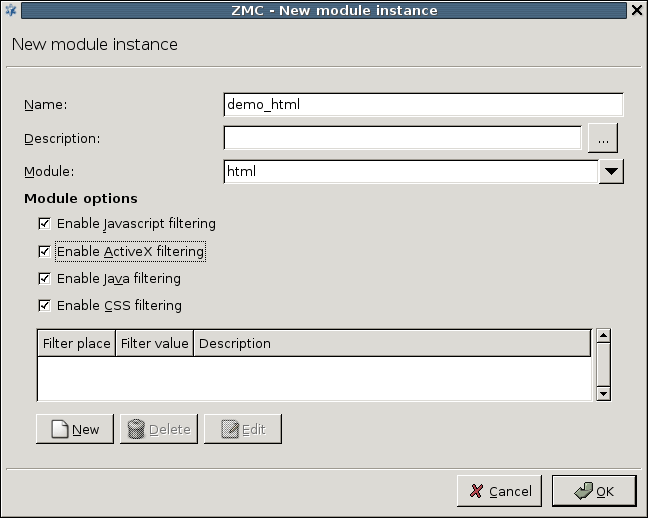
The HTML module can be used to filter various scripts and tags in HTML pages. It can operate both in file and stream mode. The HTML module has the following options:
: Remove all JavaScripts. Enabling this option removes all
javascriptandscripttags, and the conditional value prefixes (for example,onclick,onreset, and so on).: Remove all ActiveX components. Enabling this option removes the
applettags and theclassidvalue prefix.: Remove all Java code references. Enabling this option removes the
java:andapplication/java-archiveinclusions, as well as theapplettags.: Remove cascading stylesheet (CSS) elements. Enabling this option removes the single
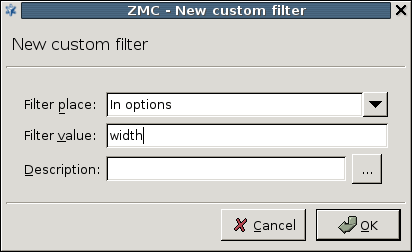
linktags, thestyletags and options, as well as theclassoptions.: Custom filters can be added to remove certain elements of the HTML code using the button. The filter can remove the specified values from HTML tags, single tags, options and prefixes (specified through the combobox). The specifies the name of the tag/header to be removed.
The options of the parameter have the following meanings:
In tags: Remove everything between the specified tag and its closing tag. Embedded structures are also handled.
In single tags: Remove all occurrences of the specified single tag. A single tag is a tag that does not have a closing element, for example,
img,hr, and so on).In options: Remove options and their values (for example,
width, and so on).In prefixes: Remove all options starting with the string set as . For example,
onwill remove all options likeonclick, and so on.
| Note |
|---|
The HTML module is designed to process only text data. It cannot handle binary data, thus directing binary files to the module should be avoided. |
The nod32 module uses the Nod32 virus filtering engine to examine incoming files. It supports only file mode. The module has the following parameters:
: Attempt to remove the virus from infected files.
: Perform virus scanning on archived files.
: Perform virus scanning on suspicious files (for example, suspicious files are often new variants of known viruses).
: Level of heuristic (non-database based) sensitivity. The available levels are
OFF, andNORMAL.
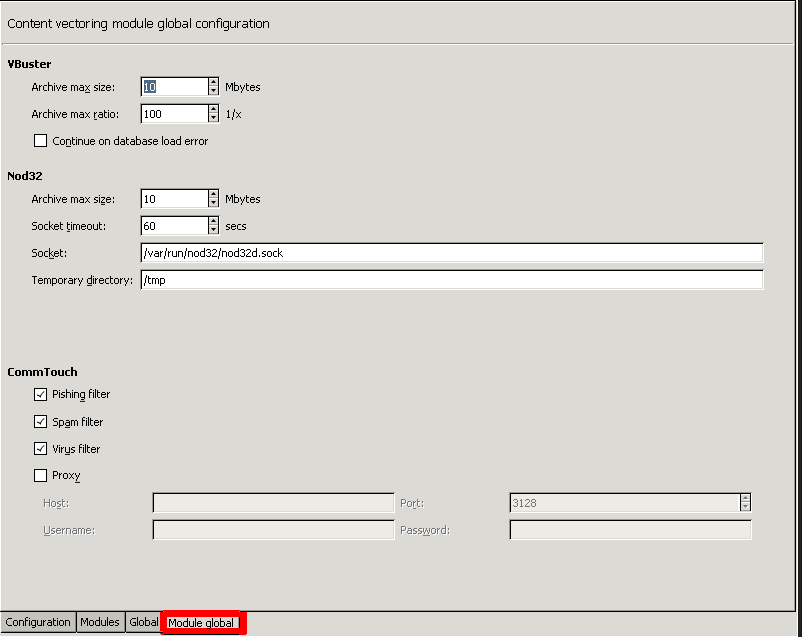
The nod32 module also has global options that apply to all instances of the module. These options can be set on the tab.
: Archived files larger than the specified value (in megabytes) are not scanned. For example, if a 2.5 MB .zip file contains a file that is 80 MB uncompressed, and the option is set to 10 MB, the file will not be scanned for viruses. However, if the option is set to 100 MB, CF will scan the file.
: Timeout value in secnds.
: The domain socket used to communicate with the nod32 engine. Default value: /var/run/nod32/nod32d.sock
: Path to the temporary directory used by the Nod32 engine.
The mail-hdr module can filter and maniputale e-mail headers in both stream and file mode. It scans the incoming e-mail (stream or file) using regular expressions and deletes or modifies the matching headers. New headers can also be inserted into the mails.
| Warning |
|---|
E-mail headers are processed and manipulated line-by-line. However, a header can span multiple lines. |
A single instance can include multiple filters; the order these filters are processed can be set using the arrow buttons. Each filter consists of a pattern, an action that is performed when the pattern is found, and an argument (for example, a replacement header). Note that not every action requires an argument.
A filter has the following parameters:
: The search string to be found in the headers. Regular expressions can be used. The following options are also available for regular expressions:
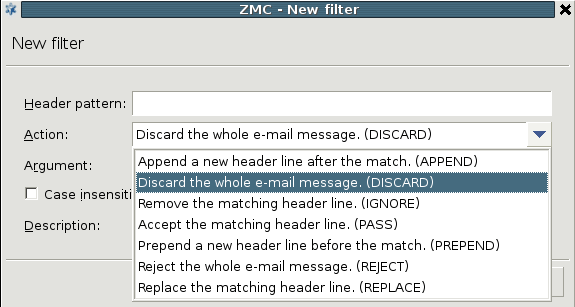
: The action to be performed on the header line or the whole message if the pattern is found in the message. The following actions are available:
Append: Add the argument of the filter as a new header line after the match.
Discard: Discard the entire e-mail message. The argument is returned to the mail server sending the message as an error message.
Ignore: Remove the matching header line from the message.
Pass: Accept the matching header line. This action can be used to create exceptions from other filter rules.
Prepend: Add the argument of the filter as a new header line before the match.
Reject: Reject the entire e-mail message. The argument is returned to the sender of the message as an error message.
Replace: Replace the mathing header line to the argument of the filter.
: The will be replaced with this string if found in the stream. The replacement can contain \n (n being a number from 1 to 9, inclusive) references, which refer to the portion of the match which is contained between the nth \( and its matching \). Also, the replacement can contain unescaped & characters which will reference the whole matched portion of the pattern space.
: The case sensitive mode can be disabled by selecting this checkbox.
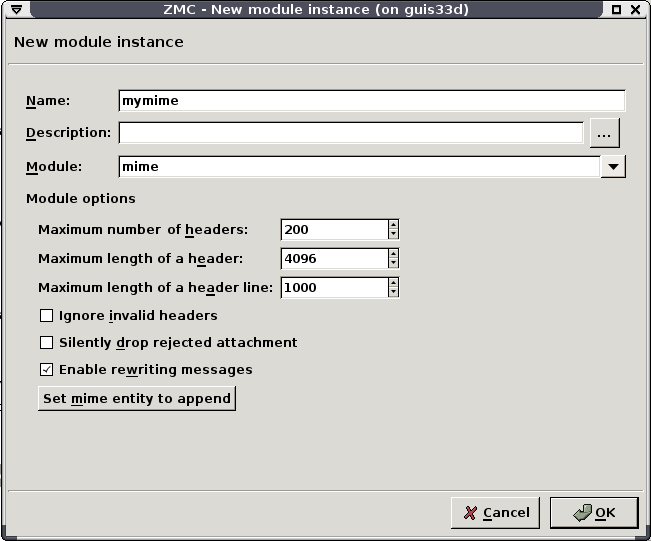
The mime module inspects and filters MIME objects (that is, mail attachments). It can check the MIME headers that describe the objects for validity, and also call a virus filtering CF module to scan the object for viruses. The mime module supports only file mode. The module has the following parameters:
: The maximal number of headers permitted in a MIME object. The object is removed if it exceeds this limit.
: The maximal length of a header in characters. Applies to the total length of the header. The header is removed if it exceeds this limit.
: The maximal length of a header line in characters. Applies to every single line of the header. The header is removed if it exceeds this limit.
: If enabled, headers not complying to the related RFCs or violating the limits set in the previous options are automatically removed (dropped).
Warning If is disabled and an invalid header is found, the entire object (for example, e-mail) is rejected.
: By default, the
mimeCF module replaces the removed objects (attachments) with the following note that informs the recipient of the message about the removed attachments: The original content of this attachment was rejected by local policy settings. If the option is enabled, no note is added to the e-mail.: If disabled, the
mimemodule does not modify the messages.: The
mimeCF module can automatically add a MIME object to the inspected messages. To use this feature, verify that the option is enabled, select , paste the MIME object into the appearing dialog box, and select .
To scan the actual MIME objects (for example, the attachments of an e-mail) for viruses, you have to create a special rule group called mime-data. Use this as the name of the rule group, and add a virus filtering module (for example, clamav) to this rule group. When the mime module is scanning an e-mail message, it will inspect the attachments, then pass the attachment to the mime-data rule group to scan for viruses. See Section 14.2.3, Routers and rule groups for details on creating rule groups.
The program module is general wrapper for third-party applications capable to work in stream or file mode. The stream or file is passed to the application set in the field.
A single instance can include multiple filters; the order these filters are processed can be set using the arrow buttons.
A program module has the following parameters:
: The application to be executed.
: If the application set in the field does not provide a return value within this interval, it is assumed to be frozen.
: The program may make changes to the data and return the modified version to CF.
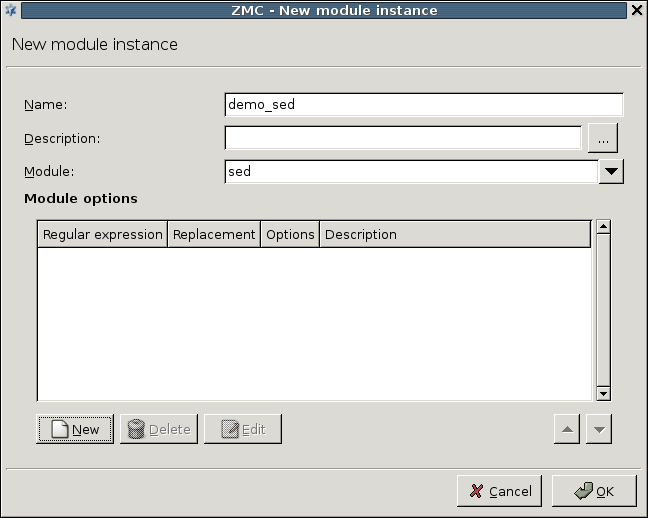
The sed module is a stream editor capable to work in both stream and file mode. It scans the target stream and replaces the string to be found (specified as a regular expression) with another string.
| Warning |
|---|
This module is similar to, but not identical with the common UNIX sed command. |
A single instance can include multiple filters; the order these filters are processed can be set using the arrow buttons.
A filter has the following parameters:
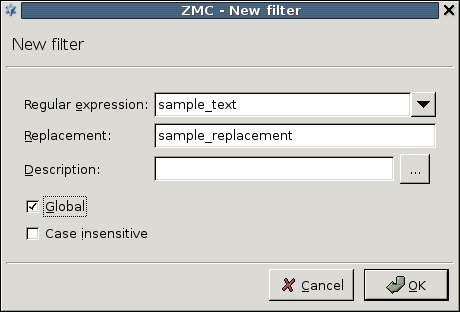
: The search string to be found in the stream. Regular expressions can be used. The following options are also available for regular expressions:
: The will be replaced with this string if found in the stream. The replacement can contain \n (n being a number from 1 to 9, inclusive) references, which refer to the portion of the match which is contained between the nth \( and its matching \). Also, the replacement can contain unescaped & characters which will reference the whole matched portion of the pattern space.
: Replace all occurrences of the search string. If not checked, the filter will replace only the first occurrence of the string.
: Disable case sensitive mode.
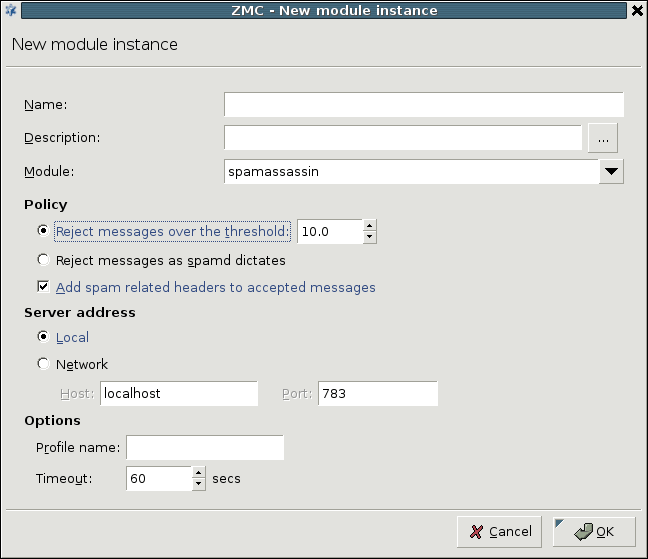
The spamassassin module uses the Spamassassin spam filtering engine to examine incoming e-mails. It supports only file mode. The module has the following parameters:
Policy related options
Reject messages over the threshold: Reject the message only if its spam status By default, SpamAssassin rejects all e-mails with a spam status (called
required_scorein SpamAssassin terminology) higher than 5 as spam. However, to minimize the impact of false positive alarms, if the spam status of an email (as calculated by SpamAssassin) is over therequired_score, but below the value set in threshold, CF only marks the e-mail as spam, but does reject it. If the spam status of an e-mail is above the threshold, it is automatically rejected.Reject messages as spamd dictates: Reject all e-mails detected as spam by SpamAssassin.
Add spam related headers to accepted messages: Append headers to the e-mail containig information about SpamAssassin, the spam status of the e-mail, and so on. Sample headers are presented below.
X-Spam-Checker-Version: SpamAssassin 3.0.3 (2005-04-27) on mailserver.example.com X-Spam-Level: X-Spam-Status: No, score=-1.7 required=5.0 tests=BAYES_00 autolearn=ham version=3.0.3
Server address
Local: SpamAssassin is running on the same host as CF. In this case, communication is performed through a UNIX domain socket.
Network: SpamAssassin is running on a remote machine. Specify its address and the port SpamAssassin is accepting connections in the and fields, respectively.
Other options
Profile name: The user under which SpamAssassin should filter e-mails. Default value: not set, the user running SpamAssassin is used (usually
nobody).Timeout: Timeout value for SpamAssassin.
Published on June 04, 2020
© 2007-2019 BalaSys
Send your comments to support@balasys.hu