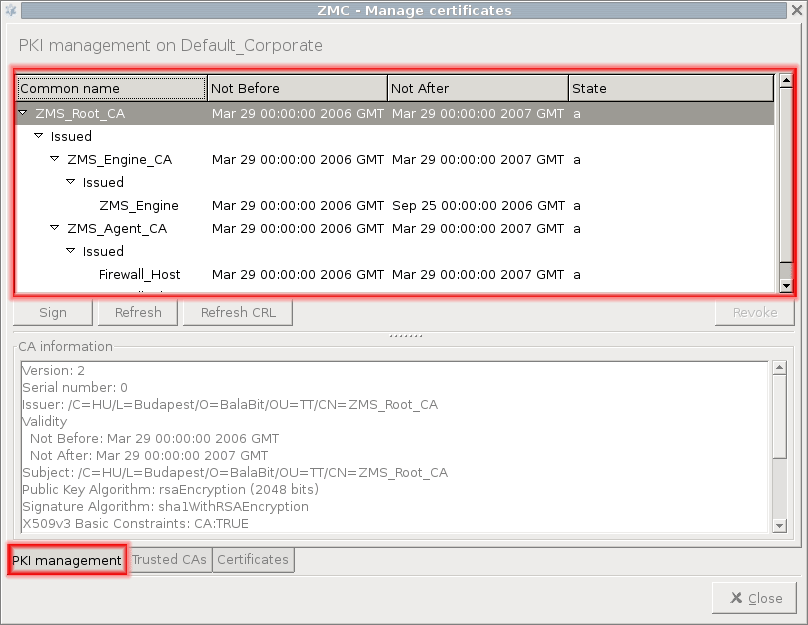
Navigation window: a tree-like navigation window displaying the managed internal CAs. On a newly installed system only local CAs created by default are available. Expired certificates are shown in red.
The internal CAs have small arrows that can be used to display the certificates issued and revoked by the CA.
For a given certificate, the following information is displayed:
Common name of the certificate
Validity (not before and not after)
State: active (a) or pending (p). A certificate becomes pending if the certificate of the CA issuing it (or the certificate of a CA higher in the CA chain) is refreshed. A certificate has to be refreshed if its validity period has expired, even if its private key has not changed. This is because the hash of the refreshed certificate is different from the old one.
Warning When the certificate of a CA is refreshed, all certificates issued by the CA has to be refreshed (re-issued) as well. If the CA has issued certificates for subCAs, then also the certificates issued by these subCAs have to be refreshed.
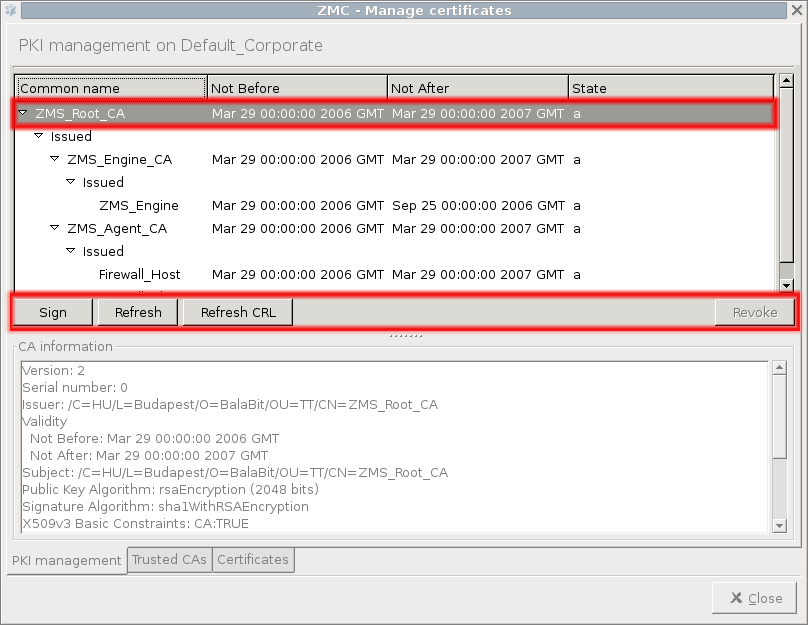
Command bar: contains the different commands that can be issued for the certificate or CA selected. The available commands are:
: available only for internal CAs, used to sign CSRs. After clicking on it, a list of unsigned CSRs is displayed. The list shows the distinguished names of the CSRs. Parameters for the certificate to be signed can be overridden here (period of validity, X.509 extensions, and so on).
: This command can be used to refresh certificates, that is, to renew them by extending their validity period if expired, or also to create new keys to the certificate. Key generation is only performed if the checkbox is selected.
Tip It is recommended to regenerate the keys as well when refreshing a certificate for any reason.
: available only for CAs. The CRL of the CA is valid until the time specified. The refreshed CRL will only be used on the managed hosts after distribution. MS distributes certificate entities, that is, when distributing certificates the corresponding CRLs are automatically distributed as well.
: available only for certificates signed by an internal CA. Marks the certificate as invalid and adds it to the CRL of the CA. CA certificates can also be revoked this way.
Note Self-signed certificates (that is, certificates of local root CAs) cannot be revoked.
The table below briefly summarizes the CAs created and used by default in PNS.
| Name of the CA | Purpose |
|---|---|
MS_Root_CA
| The Root CA of PNS, used to sign certificates of all other local CAs in PNS. |
MS_Engine_CA
| Signs the certificate of the MS engine. |
MS_Agent_CA
| Signs certificates of the transfer agents. |
Table 11.1. Default CAs and their purpose
For details on configuring agent and engine certificates, please refer to Chapter 13, Advanced MS and Agent configuration.
Published on June 04, 2020
© 2007-2019 BalaSys
Send your comments to support@balasys.hu