The following sections describe the options available for scanpaths. The options can be configured on the , , tabs of the scanpath dialog.
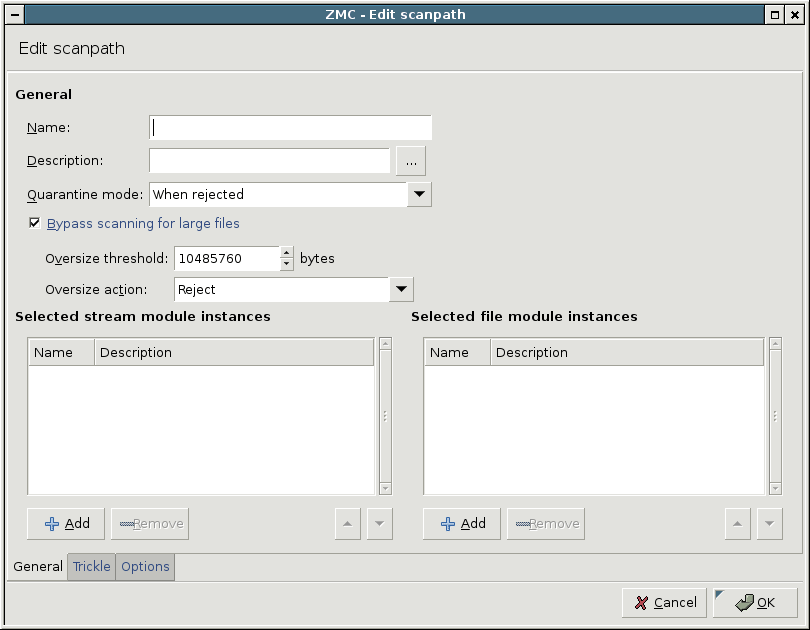
specifies when to store an infected in the quarantine. Always the original file is stored.
: Quarantine all objects rejected for any reason.
: Quarantine objects that could not be disinfected.
: Quarantine only the original version of the files which were successfully disinfected. For example, if an infected object is found but it is successfully disinfected, the original (infected) object is quarantined. That way, the object is retained even if the disinfection damages some important information.
: Disable quarantining; objects rejected for any reason are dropped.
: By default, all files arriving to the scanpath are scanned. However, because of performance resons this might not be optimal, particularly if large files (for example, ISO images) are often downloaded through the firewall. Therefore it is possible to specify an value and an . If the checkbox is selected, then objects larger than (in bytes) are not scanned, but accepted or rejected, as set in . It is also possible to return an error message for oversized files.
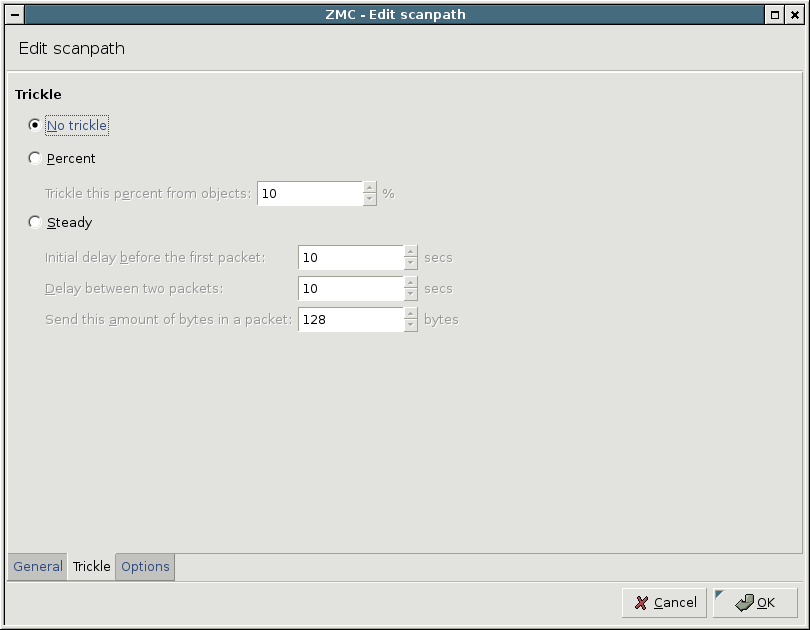
Content filtering cannot be performed on partial files — the entire file has to be available on the firewall. Sending of the file to the client is started only if no virus was found (or the file was successfully disinfected). Instead of receiving the data in a continuous stream, as when connecting to the server “regularly”, the client does not receive any data for a while, then “suddenly” it starts to flow. This phenomena is not a problem for small files, since these are transmitted and checked fast, probably without the user ever noticing the delay, but can be an issue for larger files when the client application might time out. Another source of annoyance can be when the bandwidth of the network on the client and server side of the firewall is significantly different. In order to avoid time outs, a solution called trickling is used. This means that the firewall starts to send small pieces of data to the client so it feels that it is receiving something and does not time out. For further information on trickling, see the Virus filtering and HTTP Technical White Paper available at the Documentation Page at https://docs.balasys.hu/. CF supports the following trickling modes. These can be set on the tab of the scanpath editor dialog.
: Trickling is completely disabled. This may result in many connection timeouts if the processing is slow, or large files are downloaded on a slow network.
: Determine the amount of data to be trickled based on the size of the object. Data is sent to the client only when CF receives new data; the size of the data trickled is the set percentage of the total data received so far.
: Trickle fixed amount of data in fixed time intervals. Trickling is started only after the period set in . If the whole file is downloaded and processed within this interval, no trickling is used.
| Tip |
|---|
It is recommended to use the percent-based trickling method, because the chance of an operable virus trickling through the system unnoticed is higher when steady trickling is used. |
CF can automatically decompress gzipped files and transmission and pass the uncompressed data to the modules. After the modules process the data, CF can recompress it and return it to PNS. To enable the automatic decompressing, select the checkbox. The compression level of the recompressed data can be set using the spinbutton.
| Note |
|---|
Compression level of 5 or higher can significantly increase the load on the CPU. |
The following actions can be set for the gzip headers through the combobox:
Leave all gzip headers intact: Do not modify the headers.
Leave filename headers intact: Retain the headers containing filenames, remove all other ones.
Remove all gzip headers: Strip all headers.
In some cases it is possible that a module or CF cannot check an object for some reason (for example the file is corrupted, or the license of the module has expired). In such situations CF rejects all objects by default. Exemptions can be set for the errors described below: check the errors for which all objects should be accepted.
Corrupted file: The file is corrupt and cannot be decompressed. Certain virus scanning module handle encrypted or password-protected files as corrupted files.
Encrypted file: The file is encrypted or password-protected and cannot be decompressed.
Unsupported archive: The file is compressed with an unknown/unsupported compression method and cannot be decompressed.
Engine warning: The file is suspicious, heuristic virus scanning detected the file as possibly infected.
OS error: A low level error occurred (the module ran out of memory, or could not access the file for some reason).
Engine error: An internal error occurred in the module while scanning the file.
License error: The license of the module has expired.
Published on June 04, 2020
© 2007-2019 BalaSys
Send your comments to support@balasys.hu