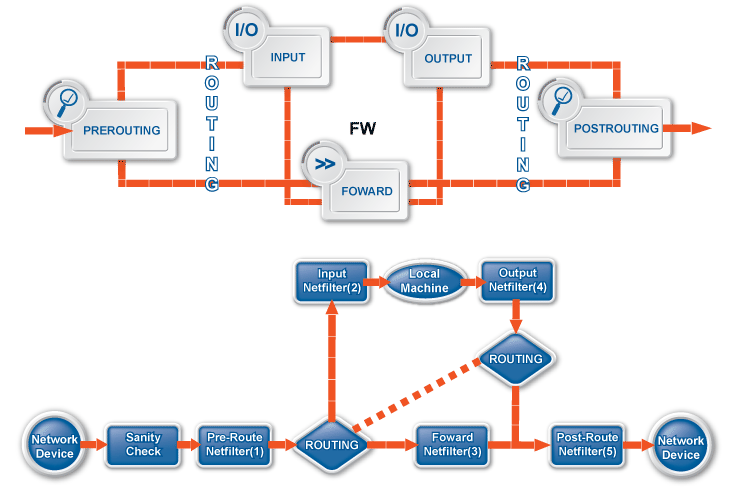
All incoming, outgoing and passing packets must go through the TCP/IP stack of the Linux kernel and as Netfilter works with packets, the best way to influence the packet flow is to cooperate with the protocol stack. At some point of the packet flow, the Netfilter framework hooks in to the Linux kernel. These points are called hooks where the stack passes the packet to the framework, which evaluates the policy on the given packet.
Based on the result of the policy evaluation, the framework can response in the following three ways:
gives back the packet to the stack to allow it to be processed further,
gives back a modified packet,
or drops the packet preventing it from further processing.
Currently, Netfilter defines five hooks in the kernel.
- PREROUTING
Right after the arrival of the packet from the network and a simple sanity check but before any routing decision is made the packet is sent to this hook.
- INPUT
If the destination of the packet (based on the routing decision) is the host itself, the packet is sent to this hook after the routing decision, but before the delivery of the packet to any application.
- FORWARD
If the destination of the packet (based on the routing decision) is not the host itself and if forwarding is enabled, the packet is sent to this hook after the routing decision, but before leaving the host.
- OUTPUT
If the packet is originating from the host and before any routing decision is made, the packet is sent to this hook.
- POSTROUTING
If the packet is leaving the host and the routing decision is made, the packet is sent to this hook, but before actually passing the packet to the network interface for transmission.
| Note |
|---|
The packet has to pass all of the hooks to get to its destination. It is not enough to pass one hook, all of the hooks must be passed. Obviously, if the packet is dropped on one hook it cannot get to any other hooks. Its processing is ended where it was dropped. |
For example, if the destination of the packet was the host, it has to successfully pass (be accepted) at the PREROUTING and the INPUT hooks. If the destination of the packet was not the host (so it is passing the host) it has to pass at the PREROUTING, FORWARD and the POSTROUTING hooks. The third case is when the packet leaves the box (originating from some application running on the host) it has to pass at the OUTPUT and the POSTROUTING hooks.
These hooks provide the Netfilter framework itself, but they are actually used by IPTables providing the heart of the Linux packet filter system this way.
Published on June 04, 2020
© 2007-2019 BalaSys
Send your comments to support@balasys.hu