6.7.5.1.1. Procedure – Configuring NAT
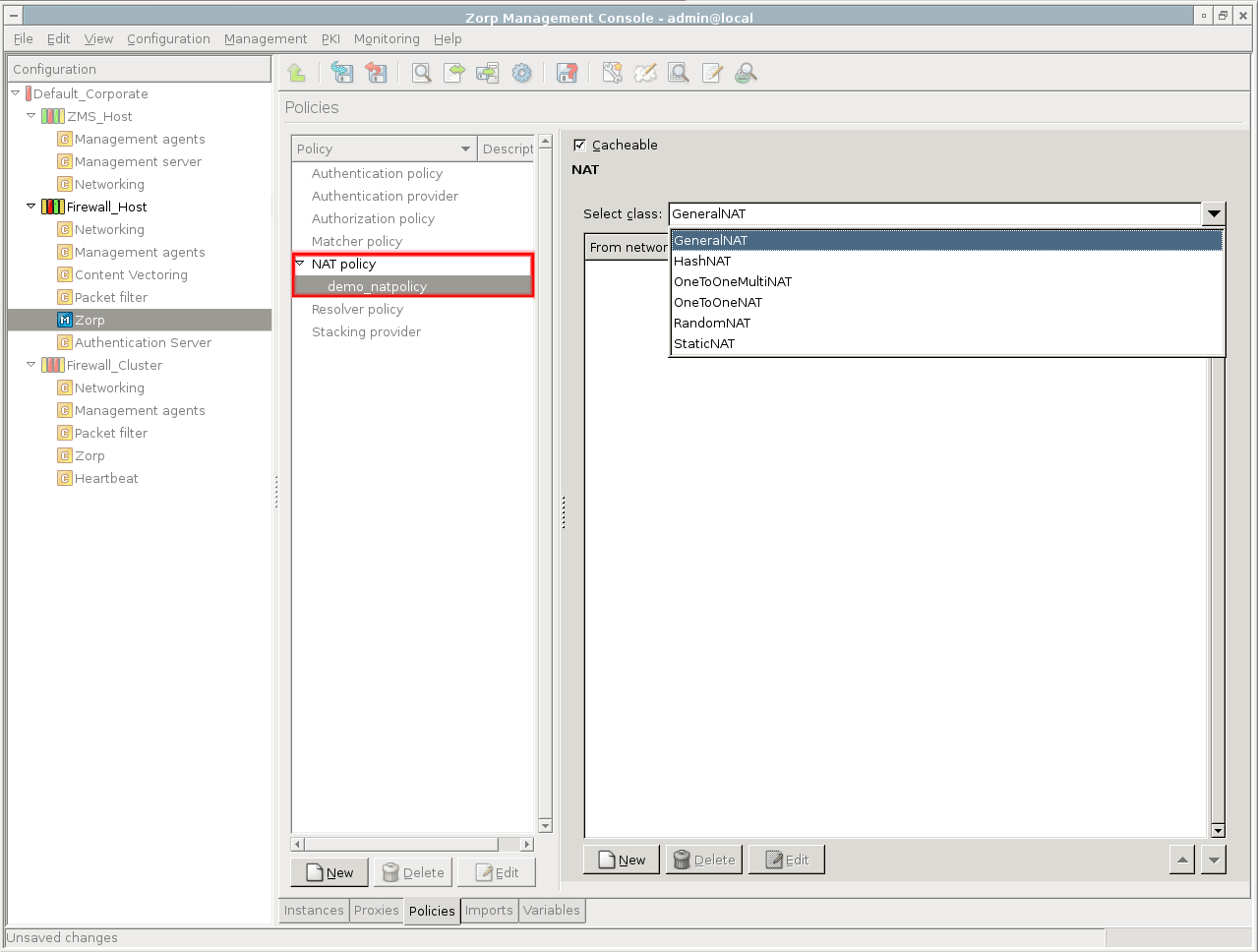
Create the required NAT policies on the tab of the MC component.
Click the button, select from the combobox and supply a name for the new policy.
Names should be descriptive and ideally contain information about the direction of NATing and/or about the type of traffic NATed.
In most network configurations NAT is typically not service-specific; a generic NAT policy may be adequate for most outgoing or incoming traffic. There are no compulsory rules for naming.
NAT policies can be renamed any time.
Tip Remove NAT policies from the configuration set if they are no longer needed.
NAT policies can be removed only if they are not used in any service definition.
Configure a NAT solution.
Application-level Gateway supports several different NAT solutions.
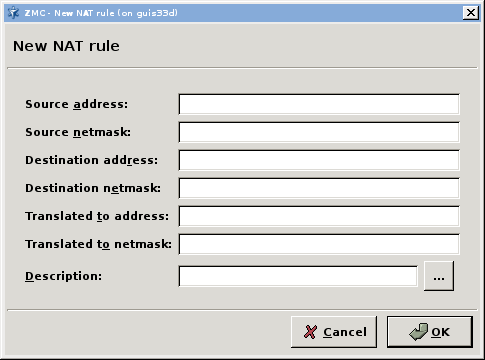
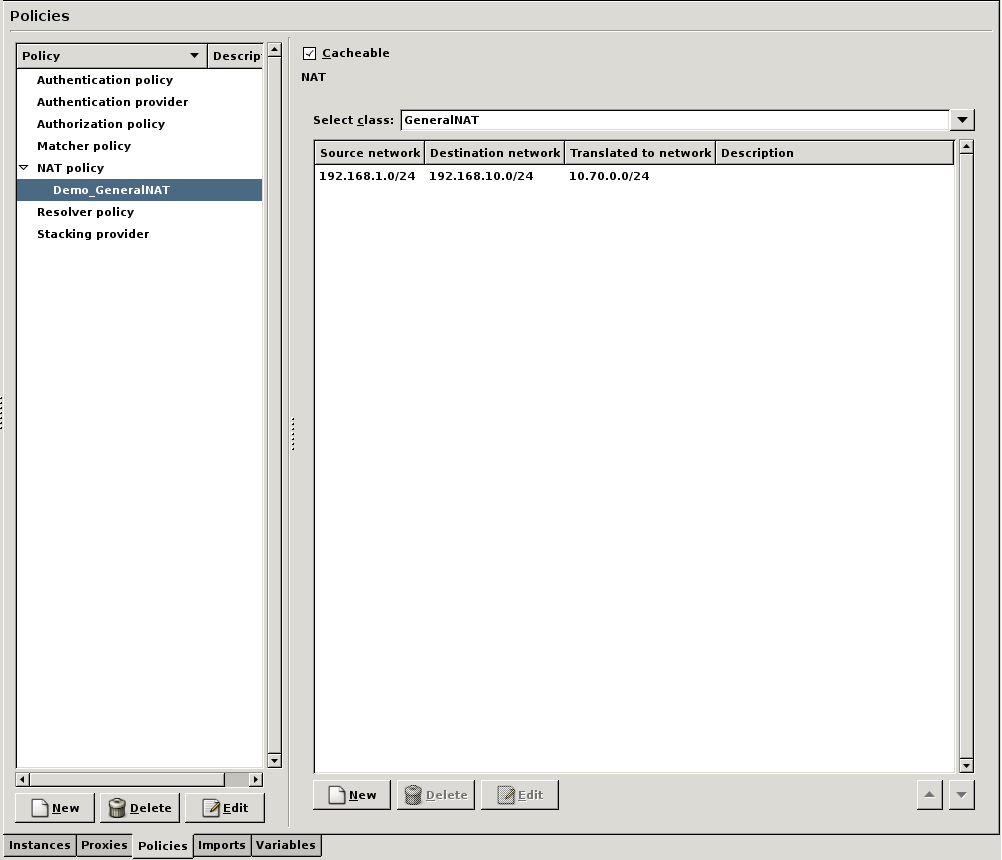
GeneralNAT has three parameters: source address, destination address, and the translated address. Connections arriving from the source address that target the destination address are modified to use the translated address. If the NAT policy is used as Source-NAT (SNAT), the source address is translated to the translated address, if the policy is used as Destination NAT (DNAT), the target address is translated.
Note The original and translated netmasks do not need to be the same: it is possible to map an entire /24 network onto a single IP address (/32 mask). However, the order of the pairs is important because the Application-level Gateway processes the list from top to bottom.
Depending on the NAT type (SNAT, DNAT), Application-level Gateway evaluates the NAT rules one after the other. If a row containing the address to be NATed as the source network, the iteration stops and Application-level Gateway modifies the IP address as specified in that row. If no match is found, the original IP address is used.
When modifying the address, it calculates the host ID of the address using the target netmask and the source network address and adds it to the target network.
Example 6.14. Address translation examples using The following two tables show a number of simple and special cases. The Destination Address in these cases is set to
0.0.0.0/0Source network Target network Source IP address Translated IP address 10.0.1.0/24
192.168.1.0/24
10.0.1.5
192.168.1.5
10.0.1.0/24
192.168.1.0/25
10.0.1.130
192.168.1.2
10.0.1.0/25
192.168.1.0/24
10.0.1.42
192.168.1.42
Source network Target network Original IP address New IP address 0.0.0.0/0
192.168.2.2/32
172.17.3.5
192.168.2.2
0.0.0.0/0
192.168.3.0/31
172.18.1.1
192.168.3.1
0.0.0.0/0
192.168.3.0/31
172.18.1.2
192.168.3.0
192.168.3.1/32
172.19.2.0/24
192.168.3.1
172.19.2.0
Configure caching.
Since the NAT decision may take a long time in some cases (for example, if there are many mappings in the list), the decisions can be stored in a cache. Storing the decisons in a cache accelerates future decisions. Caching can be enabled/disabled using the checkbox in the configuration window of the NAT policy.
Tip It is recommended to enable caching for complex NAT decisions.
Note Enabling caching can have interesting, but sometimes unwanted effects on some NAT types, for example on
RandomNAT. UsingRandomNATand theCachableoption together would result in LoadBalancing, but with sticky IP addresses, the cache would remember which source IP address was used before for a specific client's IP address and would use the same address again. This can be very useful, but can also cause a lot of headache and troubleshooting.
Published on June 04, 2020
© 2007-2019 BalaSys
Send your comments to support@balasys.hu