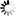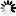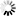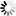5.1.5.1. Procedure – Configuring spoof protection
Steps:
Select the interface and next to the field, click
 .
.Select the zones the configured interface is connected to either directly or indirectly through routers.
Note The Zone tree in the dialog window displays organized IP addresses, starting from the most generic (
0.0.0.0/0) to the most specific. There is an implicit inheritance in the specification: if the10.0.0.0/8address range is specified to connect toeth1, all more specific subnets of this address range (10.0.0.0/9,/10, .../32) connect toeth1also, unless a more specific binding is explicitly specified.Select .
Note The ruleset must be regenerated after modifying any interface settings. It is not done automatically.
© 2021 BalaSys IT Security.
Send your comments to support@balasys.hu