The command bar contains various operations that can be performed with the CAs. Some of them require a CA to be selected from the information window, in this case the given operation will be performed on the CA selected. Note, that for some of the activities multi-select option is available for performing mass activity. These possibilities are described in details at each activity.
: Create a new local Certificate Authority. For details, see Procedure 11.3.7.2, Creating a new CA. As CAs require unique names, they can only be created one by one.
: Import a CA certificate from a PEM, DER, or PKCS12 formatted file. It is possible to import only one CA at once. The Import into selected object can only be selected if at the time of the only one line is selected in the Trusted CA list.
: Export the certificate of the selected CA into a file in PEM, DER, or PKCS12 format. The PKCS12 format is only available for internal CAs.
: A CA available on a site, can be made available on all sites managed by MS, by clicking this button and checking in the checkbox. Making a CA certificate available on all sites cannot be reversed, that is, once a CA has been made available on all sites, later it cannot be limited to a single site. This has the same effect as checking in the corresponding checkbox when creating a new CA.
Warning This operation cannot be reversed or undone.
: Self-sign the certificate signing request (CSR) of the selected local CA. Only certificates not yet signed by a CA can be self-signed. This activity can be implemented one by one on the items, no multi-selection is possible.
Note Local root CAs can be created by self-singing a so far unsigned CSR of a Trusted CA.
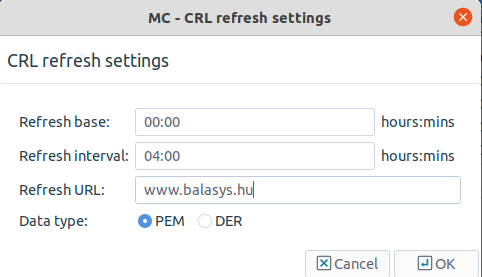
: Set the parameters for refreshing the CRL of the selected external CA. Note, that only single-selection is possible.
The following parameters can be set:
: It defines at what time the retrieval of the CRL shall be started.
: It defines how often the CRL shall be retrieved.
By setting the to 00:00 and the to 04:00, the CRL will be downloaded every four hours, starting from midnight.
: The location of the CRL can be retrieved with this parameter setting. The CRL can be downloaded through HTTP.
Note It is very important to set the refresh URL option, otherwise the validity of the certificates issued by the CA cannot be reliably verified. The CRL shall be downloaded and automatically distributed regularly.
: It defines the format of the CRL to be downloaded (PEM or DER).
: Change the password of the selected local CA or it is possible to define a password here if it has not been configured yet.
: Revoke the certificate of the selected local CA that was signed by another local CA. Self-signed CA certificates cannot be revoked this way. For details, see Procedure 11.3.8.3, Revoking a certificate.
Note It is possible to multi-select a number of certificates for the Revoke activity. However, if the Issuer of the selected certificates is not the same, the Revoke button will not be active.
Note If the certificate(s) selected for Revoke is in use in the current configuration, a warning will be displayed to inform the administrator. It is important that in case a certificate is in use, it cannot be revoked. If the certificate in use is part of a multiple selection of certificates for the Revoke activity, none of the selected certificates will be revoked.
: Delete the selected certificate. For details, see Procedure 11.3.8.4, Deleting certificates.
Note It is possible to multi-select a number of certificates for the Delete activity. If the certificate(s) selected for Delete is in use in the current configuration, a warning will be displayed to inform the administrator. It is important that in case a certificate is in use, it cannot be deleted. If the certificate in use is part of a multiple selection of certificates for the Delete activity, none of the selected certificates will be deleted.
Copyright: © 2021 Balasys IT Security
Send your comments to support@balasys.hu