Global parameters that apply to every IPSec VPN connection of the PNS host can be set on the tab.
Set special options of a particular IPSec VPN connection on the tab and the and submenu tabs.
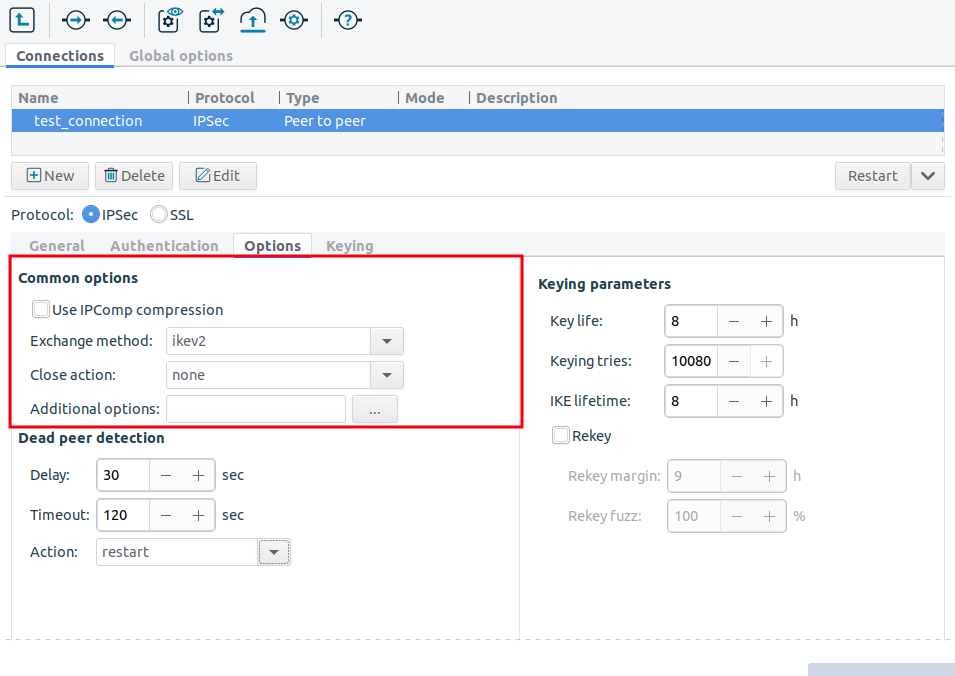
Besides the Dead Peer detection parameters, as introduced in Section 16.3, Configuring IPSec connections, there are additional parameters that can be configured Under the Options tab.
Common options
Use IPComp compression
If this parameter is enabled, that is the parameter is checked in, the daemon accepts compressed and uncompressed data as well. If the parameter is not enabled, that is, the parameter is not checked in, the daemon accepts only uncompressed data.
Exchange method
The available values are: ikev1, ikev2.
The key exchange method can be selected here for initializing the connection, that is ikev1 or ikev2.
Close action
The available values are: none, clear, hold and restart.
This parameter defines the action to take if the remote peer unexpectedly closes. This parameter is not supported for ikev1 connections.
Fragmentation
The available values are: yes, accept, force and no.
This parameter enables Internet Key Excahnge (IKE) fragmentation. Note that fragmented messages arriving from a peer are always processed, regardless of this parameter option.
If this parameter is set to yes, that is, checked in, and the peer supports it, any oversized IKE message will be fragmented.
If the parameter is set to accept fragmented content is supported arriving from the peer, yet the daemon does not send fragmented messages.
If the parameter is set to force the initial IKE message will be fragmented.
Additional options
This parameter enables the user to provide any additional StrongSwan parameter manually that is not available in the GUI. Also, if the configuration of a parameter is available though in the GUI, but the required setting is not, it can be manually defined here. Even already defined parameter configuration settings can be overwritten at , as the configuration will use the latest definition of the parameter. The parameters have to be provided in the format described on the StrongSwan documentation site, available at:
https://wiki.strongswan.org/projects/strongswan/wiki/ConnSection.
The section of the tab specifies key-handling and key-exchange parameters. Modify these parameters only if it is necessary for compatibility with the remote endpoint.
| Note |
|---|
Do not modify these options unless it is required and it is perfectly clear how these parameter settings affect the configuration. |
The options of the tab specify the encryption used in the connection.
Keying parameters
Key life
This parameter defines how long the key connection shall last, from the negotiation until expiry.
Key tries
This parameter defines the number of attempts for negotiating or renegotiating the connection.
IKE lifetime
This parameter defines the length of the keying channel connection before it is renegotiated.
Rekey
Enabling this parameter requires the connection to be renegotiated when it is about to expire.
Disabling this parameter will result in the daemon not requesting renegotiation, nevertheless, it does not prevent from responding to renegotiation requested from the other end.
Copyright: © 2021 Balasys IT Security
Send your comments to support@balasys.hu