The following sections describe and show examples to common protocol-level TLS settings.
The cipher algorithms used for key exchange and mass symmetric encryption are specified by the cipher attribute of the class referred in the client_tls_options or server_tls_options of the Encryption policy. These attributes contain a cipher specification as specified by the OpenSSL manuals. For more information on cipher suite names and their meanings, refer to the OpenSSL documentation openssl-ciphers(1) manual page.
The default set of ciphers can be set by using the following predefined variables.
| Name | Value |
|---|---|
| TLS_CIPHERS_DEFAULT | Secure cipher suites with acceptable client compatibility. |
| TLS_CIPHERS_OLD | Ciphers suites with support for very old clients through TLSv1 and TLSv1.1. |
| TLS_CIPHERS_CUSTOM | Permit only the use of ciphers which defined in value. |
Table 3.3. Constants for cipher selection
Cipher specifications as defined above are sorted by key length. The cipher providing the best key length will be the most preferred.
The Proxedo Network Security Suite uses two sets of configured cipher list. The TLS_CIPHERS_DEFAULT is recommended for general use. The TLS_CIPHERS_OLD contains additional cipher suites for compatibility with clients that do not support newer cipher suites.
The following table shows the ordered list of predefined cipher suites used in PNS.
| Cipher suite | TLS_CIPHERS_DEFAULT | TLS_CIPHERS_OLD |
|---|---|---|
| ECDHE-ECDSA-AES128-GCM-SHA256 | yes | yes |
| ECDHE-RSA-AES128-GCM-SHA256 | yes | yes |
| ECDHE-ECDSA-AES256-GCM-SHA384 | yes | yes |
| ECDHE-RSA-AES256-GCM-SHA384 | yes | yes |
| ECDHE-ECDSA-CHACHA20-POLY1305 | yes | yes |
| ECDHE-RSA-CHACHA20-POLY1305 | yes | yes |
| DHE-RSA-AES128-GCM-SHA256 | yes | yes |
| DHE-RSA-AES256-GCM-SHA384 | yes | yes |
| DHE-RSA-CHACHA20-POLY1305 | no | yes |
| ECDHE-ECDSA-AES128-SHA256 | no | yes |
| ECDHE-RSA-AES128-SHA256 | no | yes |
| ECDHE-ECDSA-AES128-SHA | no | yes |
| ECDHE-RSA-AES128-SHA | no | yes |
| ECDHE-ECDSA-AES256-SHA384 | no | yes |
| ECDHE-RSA-AES256-SHA384 | no | yes |
| ECDHE-ECDSA-AES256-SHA | no | yes |
| ECDHE-RSA-AES256-SHA | no | yes |
| DHE-RSA-AES128-SHA256 | no | yes |
| DHE-RSA-AES256-SHA256 | no | yes |
| AES128-GCM-SHA256 | no | yes |
| AES256-GCM-SHA384 | no | yes |
| AES128-SHA256 | no | yes |
| AES256-SHA256 | no | yes |
| AES128-SHA | no | yes |
| AES256-SHA | no | yes |
| DES-CBC3-SHA | no | yes |
Table 3.4. Configured cipher lists in PNS
| Warning |
|---|
Using |
If a custom list of ciphers is required, the TLS_CIPHERS_CUSTOM variable can be used along with a custom cipher string. The custom cipher string should be a colon-separated list of cipher suites, specified in the syntax recognized by OpenSSL.
| Note |
|---|
The order of the ciphers in the list matters. It will be selected the first cipher from the list that is supported by both the client and the server, allowing control over which ciphers are preferred. |
The custom cipher string should be formatted as follows:
<Cipher1>:<Cipher2>:<Cipher3>:...:<CipherN>[:!<Exclusion1>[:!<Exclusion2>:...]]
Each cipher suite is separated by a colon (:). Exclusion rules are specified by prefixing the cipher name with an exclamation mark (!) and can be included at the end of the list to disable specific ciphers.
| Example 3.11. Configuring an Encryption Policy with Custom cipher suites |
|---|
|
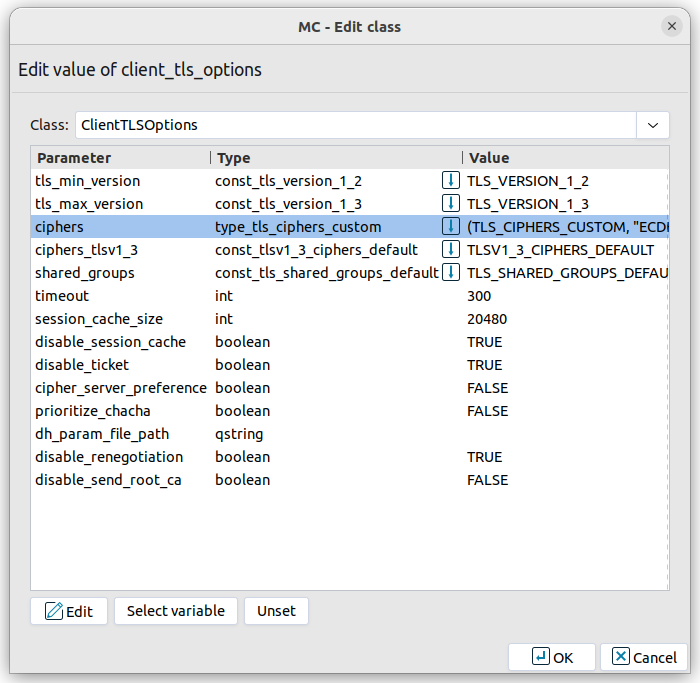
The following example configures an Encryption Policy that prioritizes security over compatibility by using custom cipher suites for client TLS options. EncryptionPolicy(
name="MyTLSEncryption",
encryption=TwoSidedEncryption(
client_verify=ClientNoneVerifier(),
client_tls_options=ClientTLSOptions(
ciphers=(
TLS_CIPHERS_CUSTOM,
(
"ECDHE-ECDSA-CHACHA20-POLY1305:"
"ECDHE-ECDSA-AES256-GCM-SHA384:"
"ECDHE-ECDSA-AES128-GCM-SHA256:"
"ECDHE-ECDSA-AES256-CCM:"
"ECDHE-ECDSA-AES128-CCM:"
"ECDHE-RSA-CHACHA20-POLY1305:"
"ECDHE-RSA-AES256-GCM-SHA384:"
"ECDHE-RSA-AES128-GCM-SHA256"
)
),
ciphers_tlsv1_3=TLSV1_3_CIPHERS_DEFAULT,
shared_groups=(TLS_SHARED_GROUPS_CUSTOM, "X25519:X448:P-256"),
cipher_server_preference=FALSE,
timeout=300,
session_cache_size=20480,
disable_session_cache=TRUE,
disable_ticket=TRUE,
disable_compression=TRUE,
dh_params=DHParam.fromFile(file_path="/etc/vela/dh.pem"),
disable_renegotiation=TRUE,
disable_send_root_ca=FALSE
),
server_verify=ServerNoneVerifier(),
server_tls_options=ServerTLSOptions(
ciphers=TLS_CIPHERS_DEFAULT,
ciphers_tlsv1_3=TLSV1_3_CIPHERS_DEFAULT,
shared_groups=TLS_SHARED_GROUPS_DEFAULT,
timeout=300,
session_cache_size=20480,
disable_session_cache=FALSE,
disable_ticket=FALSE,
disable_compression=FALSE
),
client_certificate_generator=StaticCertificate(
certificates=(
Certificate.fromFile(
certificate_file_path="/etc/key.d/certs/cert.chain.pem",
private_key=PrivateKey.fromFile(
"/etc/key.d/certs/key.pem",
passphrase=""
)
),
Certificate.fromFile(
certificate_file_path="/etc/key.d/ecdsa/cert.chain.pem",
private_key=PrivateKey.fromFile(
"/etc/key.d/ecdsa/key.pem",
passphrase=""
)
)
)
)
)
)
|
Copyright: © 2021 Balasys IT Security
Send your comments to support@balasys.hu