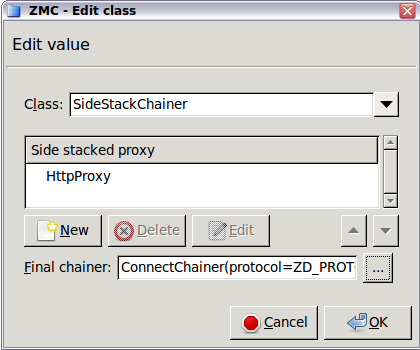
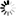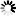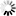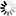Application-level Gateway firewall rules are managed on the page. The following information is displayed for every rule:
| Note |
|---|
Not every column is displayed by default. To show or hide a particular column, right-click on the header of the table and select the column from the menu. |
: Shows if the rule is enabled or disabled.
: The unique ID number of the firewall rule.
: The tags (labels) assigned to the firewall rule. For details on assigning tags to rules, see Procedure 6.5.5, Tagging firewall rules.
: The transport protocol used in the connection. This is the protocol used in the transport layer (Layer 4) of the OSI model. For example, TCP, UDP, ICMP, and so on.
: The rule permits traffic only from the listed VPN connections (or IPSec connections with the specified Request ID).
: The rule permits traffic only for the clients of the listed zones and subnets.
: The rule permits traffic only for connections targeting the listed ports of the firewall host.
: The rule permits traffic only for connections that target addresses of the listed zones and subnets.
: The rule permits traffic only for connections that target an existing IP address of the selected interface (or interface group) of the firewall host. This parameter can be used to provide nontransparent service on an interface that received its IP address dynamically.
: The rule permits traffic only for connections that target the listed ports of the destination address.
: The name of the service used to inspect the traffic.
: The service started by the rule belongs to the instance shown.
: The description of the rule.
Published on June 04, 2020
© 2007-2019 BalaSys
Send your comments to support@balasys.hu