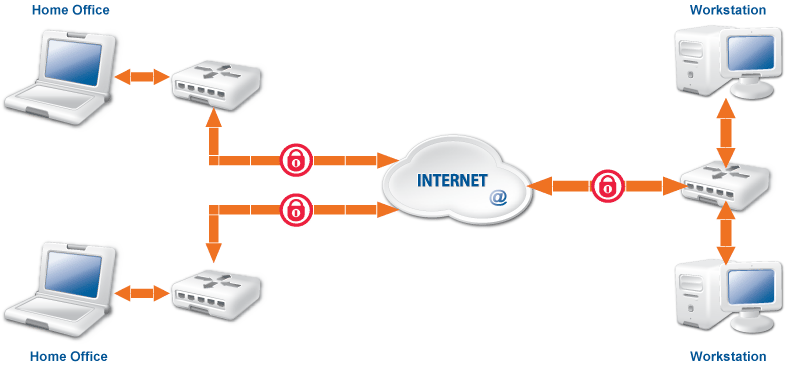
Computers and even complete networks often have to be connected across the Internet, like in the case of organizations having multiple offices or employees doing remote work. In such situations it is essential to encrypt the communication to prevent anyone unauthorized from obtaining sensitive data. Virtual Private Networks (VPNs) solve the problem of communicating confidentially over an untrusted, public network.
VPNs retain the privacy, authenticity, and integrity of the connection, and ensure that the communication is not eavesdropped or modified. VPN traffic is transferred on top of standard protocols over regular networks (for example, the Internet) by encapsulating data and protocol information of the private network within the protocol data of the public network. As a result, nobody can recover the tunneled data by examining the traffic between the two endpoints.
VPNs are commonly used in the following situations:
To connect the internal networks of different offices of an organization.
To allow remotely-working employees access to the internal network.
To transfer unencrypted protocols in a secure, encrypted channel — without having to modify the original protocol.
To secure Wi-Fi networks.
Published on June 04, 2020
© 2007-2019 BalaSys
Send your comments to support@balasys.hu