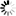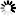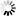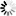The SSH proxy is able to enforce policies on the various elements of the encrypted SSH communication, such as the MAC, key-exchange, etc. algorithms that are permitted to be used. The parameters can be set separately for the client and for the server side. The attributes are represented as comma-separated strings listing the enabled methods/algorithms, in the order of preference.
Key exchange algorithms
The permitted key exchange algorithms can be specified via the
client_kex_algos and
server_kex_algos attributes. The SSH proxy supports
the diffie-hellman-group16-sha512 and
diffie-hellman-group18-sha512 and
diffie-hellman-group14-sha256 and
diffie-hellman-group14-sha1 and
diffie-hellman-group1-sha1 algorithms.
Host key algorithms
The permitted host key algorithms can be specified via the
client_hostkey_algos and
server_hostkey_algos attributes. The supported
algorithms are ssh-rsa, rsa-sha2-256, rsa-sha2-512 and
ssh-dss.
| Note |
|---|
For a hostkey algorithm to work for the clients the corresponding private
key has to be set in the |
Public key algorithms
The permitted public key algorithms can be specified via the
client_pubkey_algos and
server_pubkey_algos attributes. The supported
algorithms are ssh-rsa, rsa-sha2-256, rsa-sha2-512 and
ssh-dss.
Symmetric cipher algorithms
The permitted symmetric cipher algorithms can be specified via the
client_cipher_algos and
server_cipher_algos attributes. The following
algorithms are supported: aes128-cbc,
3des-cbc, blowfish-cbc,
cast128-cbc, arcfour,
aes192-cbc, aes256-cbc,
aes128-ctr, aes192-ctr,
aes256-ctr, aes128-gcm@openssh.com,
aes256-gcm@openssh.com.
MAC algorithms
The permitted MAC algorithms can be specified via the
client_mac_algos and
server_mac_algos attributes. The supported algorithms
are: hmac-sha2-256 and
hmac-sha2-512 and hmac-sha1 and
hmac-md5.
Published on May 30, 2024
© BalaSys IT Ltd.
Send your comments to support@balasys.hu