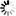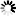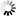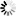2.2. Procedure – Outband authentication with Zorp
Purpose:
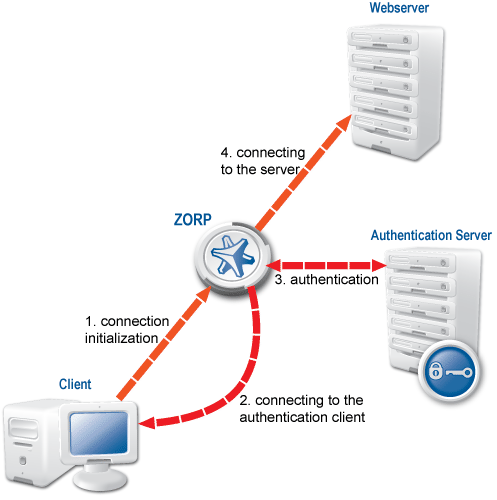
Zorp implements outband authentication according to the following procedure:
Steps:
The client initiates a connection towards the server.
Zorp determines the service to be accessed based on the IP address of the client and the server. If authentication is required for the connection (an authentication policy is assigned to the service), Zorp initiates a connection towards the client using the Zorp Authentication Agent protocol.
Depending on the authentication methods available (for example, for password-based authentication), the dialog of the Zorp Authentication Agent is displayed on the client machine. The user enters the username that the Zorp Authentication Agent forwards to Zorp.
The Zorp firewall connects to Zorp Authentication Server (ZAS) and retrieves the list of authentication methods enabled for the particular user. Multiple authentication methods can be enabled for a single user (for example, x509, Kerberos, password, and so on). The authorization of the user is also performed in this step, for example, the verification of the LDAP group membership.
Zorp returns the list of available methods to the client. The user selects a method and provides the information (for example, the password) required for the method.
The Zorp Authentication Agent sends the data (for example, the password) to Zorp that forwards it to ZAS.
ZAS performs the authentication and notifies Zorp about the result (success/failure).
Zorp returns the result to the client and — if the authentication was successful, builds a connection towards the server. In case of a failed authentication it terminates the connection to the client.
Published on May 30, 2024
© BalaSys IT Ltd.
Send your comments to support@balasys.hu