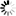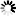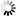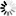4.1.6. Procedure – Enabling Kerberos authentication in AS
Complete the following steps to enable Kerberos authentication in Authentication Server using Windows Active Directory (AD) environment.
Steps:
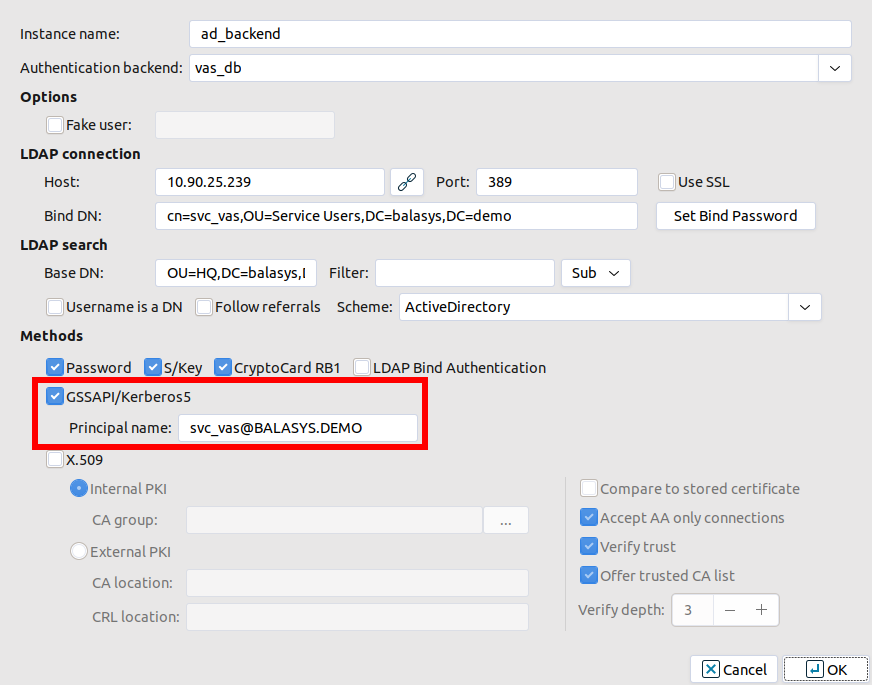
In MC select .
Select the checkbox at section and provide the realm at field.
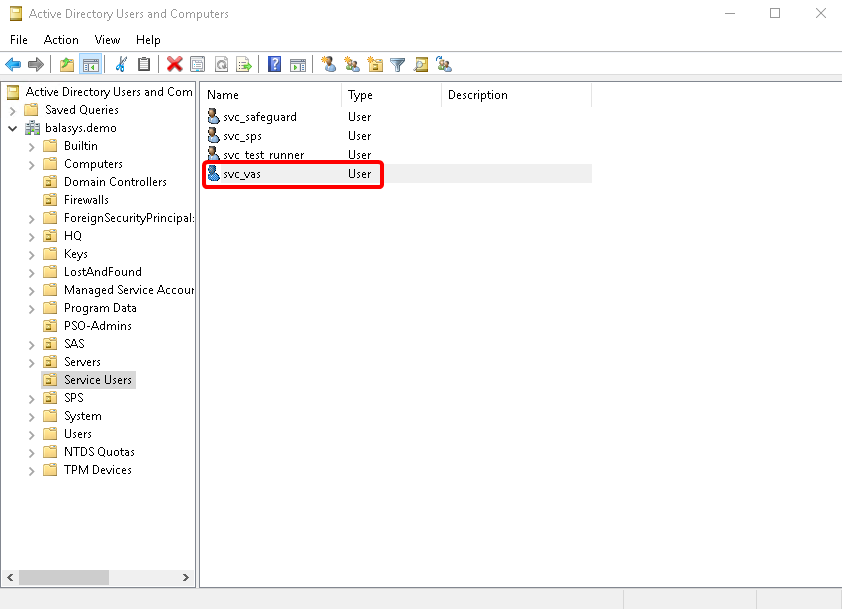
Create the domain user in the . Use the provided in the previous step.
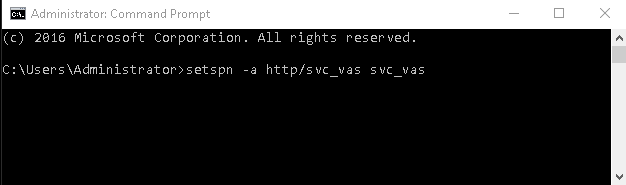
Start the Command Prompt in the Domain Controller with Administrator privileges.
Run the following command:
setspn -a http/ <username> <username>
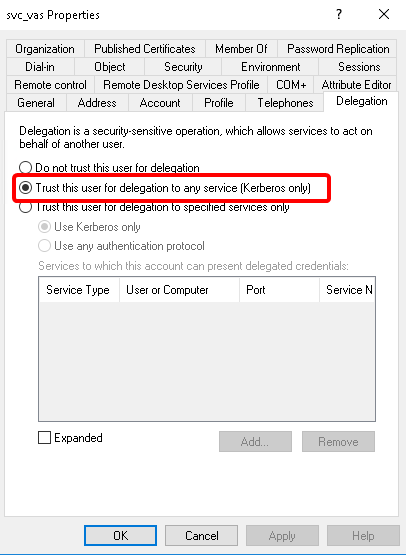
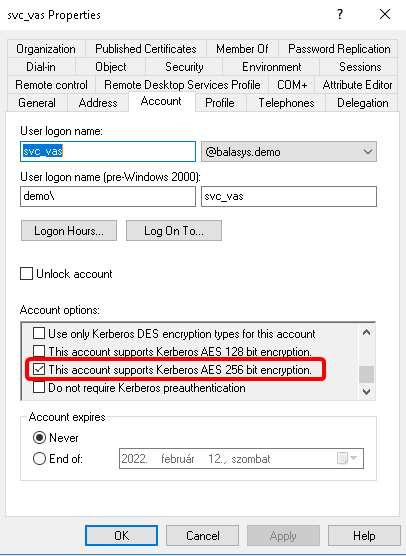
In the window, select the user created in Step 3. and open the user’s .
A new tab is available now. Select the option. Click .
Switch to the tab in the menu item. Select the option and click to apply the setting.
Install the Kerberos packages on the required server, for example on Authentication Agent.
#:apt-get install krb5-user
Provide the FQDN of the default realm during the installation process.
Test Kerberos with the following commands. In the example the FQDN is BALASYS.DEMO.
#:kinit svc_vas@BALASYS.DEMO #:klist -e #:kdestroy
Set Kerberos with the following commands:
#:ktutil ktutil:addent -password -p svc_vas@BALASYS.DEMO -k 1 -e aes256-cts-hmac-sha1-96 ktutil:addent -password -p svc_vas@BALASYS.DEMO -k 2 -e aes256-cts-hmac-sha1-96 ktutil:addent -password -p svc_vas@BALASYS.DEMO -k 3 -e aes256-cts-hmac-sha1-96 ktutil:addent -password -p svc_vas@BALASYS.DEMO -k 4 -e aes256-cts-hmac-sha1-96 ktutil:addent -password -p svc_vas@BALASYS.DEMO -k 5 -e aes256-cts-hmac-sha1-96 ktutil:addent -password -p svc_vas@BALASYS.DEMO -k 6 -e aes256-cts-hmac-sha1-96 ktutil:wkt /etc/krb5.keytab ktutil:exit #:chown vas /etc/krb5.keytab
Copyright: © 2021 Balasys IT Security
Send your comments to support@balasys.hu