6. Procedure – Enabling virus filtering for uploads
Purpose:
In case your security policies require it, you can enable virus filtering for files that your users upload to external servers. This is also required when protecting a server to which files can be uploaded from outside. To achieve this, you have to modify the HttpVirusProxy created in Procedure 5, Enabling virus filtering in HTTP. Complete the following steps.
| Note |
|---|
|
If enabled in CF, then trickling is performed in this case as well, but this time towards the server in order to avoid server-side time outs. The HTTP proxy will pass not only the data, but the HTTP headers as well to the stacking provider, so it can use them for the MIME decapsulation. The virus-filtering modules are is able to decode MIME encoded content. |
Steps:
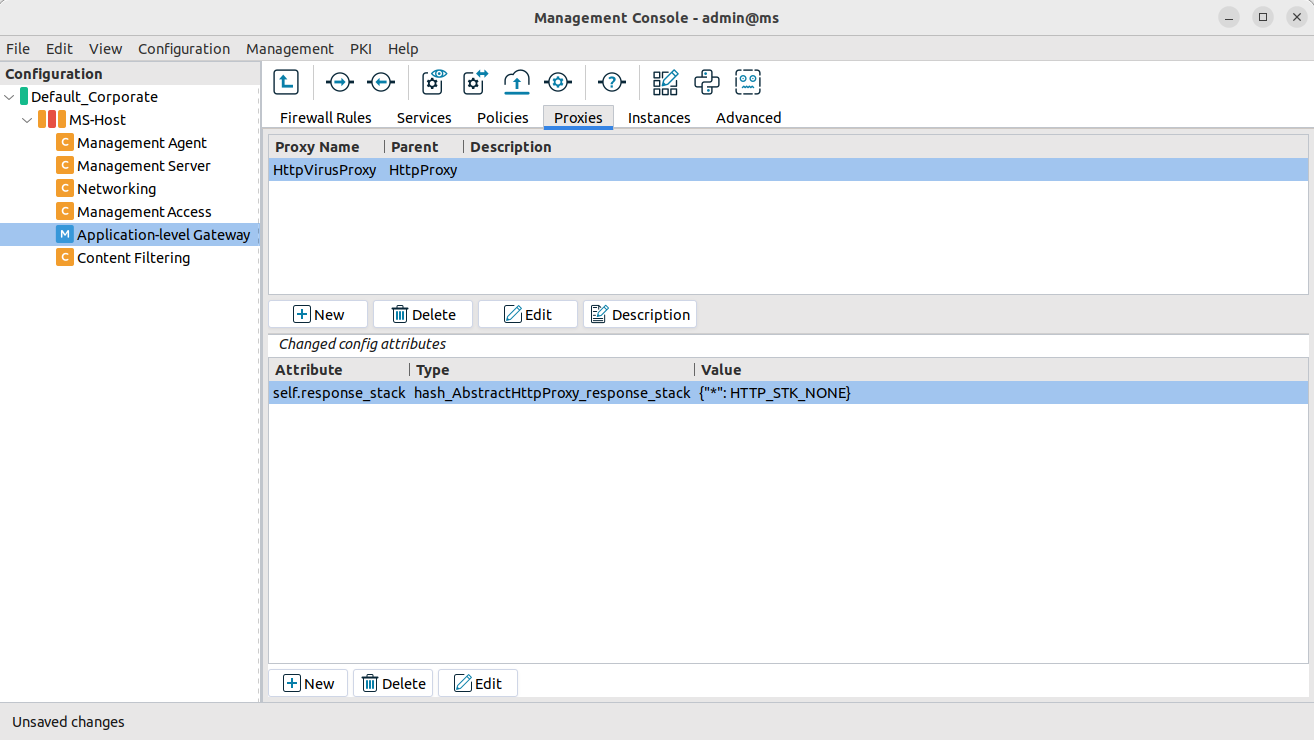
Select , then select the
HttpVirusProxyproxy class.Add the
self.request_stackattribute to the panel.Select this new attribute, then click .
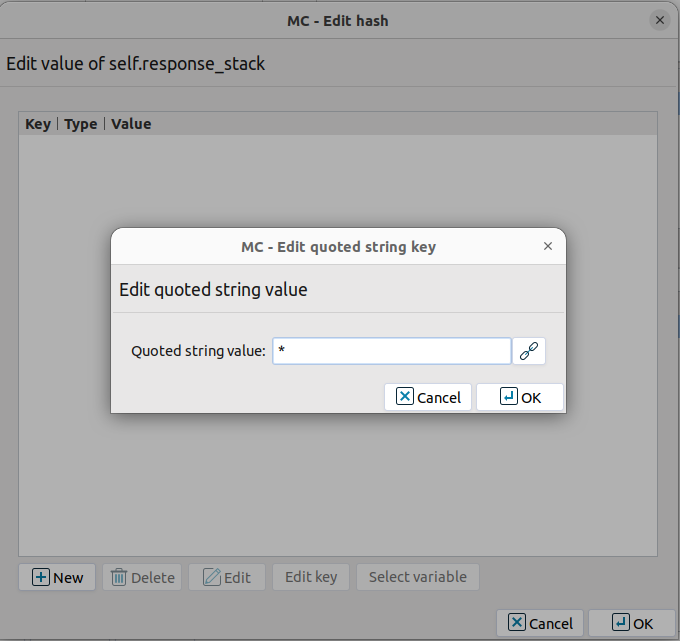
Enter the
*(asterisk) character, then click .Click on the text in the field, then select
type_http_stk_mime. (When uploading files via HTTP, the files have to be sent MIME-encoded, while this is not required for downloading. MIME encoding is important only when uploading multiple files. The headers are needed for the MIME decapsulation.)Click , then select the second row of the appearing panel (the one having
vela_stackin its field). Click .Configure the proxy to send the incoming data to CF.
Select .
In the field, select the stacking provider policy (for example,
CF) created in Procedure 4, Making CF available for Application-level Gateway services.In the field, select the rulegroup (for example,
http) created in Procedure 4, Making CF available for Application-level Gateway services.Click .
Python: Modify the HttpProxy class which stacks CF to inspect the uploaded data.
self.request_stack["*"]=(HTTP_STK_MIME, (V_STACK_PROVIDER, "CF", "http"))Optional Step: Note that with the configuration set in the previous steps, every HTTP response and request is scanned for viruses, if it contains data. (For example, according to the RFC, HEAD responses and GET requests do not have data parts.) To filter only the POST requests, complete the following steps.
On the tab, select
HttpVirusProxy, then select , and click .Select the
*key, then click . TypePOST, then click .Python:
self.request_stack["POST"]=(HTTP_STK_MIME, (V_STACK_PROVIDER, "CF", "http"))
Optional Step: It is even possible to specify different proxy classes for the different request/response types. To accomplish this, you will need to add two values to the
self.response_stackattribute. The first one will specify which virus filtering proxy to use for POST responses, the second one for GET responses. That way it is possible to use different scanpaths or different virus-filtering modules for the different response types. For example, you can examine the downloaded data with a rulegroup that uses the clamav and nod32 engines, but use only one module to examine the uploaded data. To accomplish this, complete the following steps.Navigate to the MC module, and create a new scanpath and a new rulegroup that will be used to examine HTTP GET requests (for example, name this rulegroup
http_get).Navigate to the MC module, select , then click .
Select the key, then click . Select the row containing , then click .
Select the rulegroup you want to use to filter POST requests (for example, ).
Python:
self.request_stack["POST"]=(HTTP_STK_MIME, (V_STACK_PROVIDER, "CF", "http"))Add a new key to the attribute. Enter
GETas the key value.Click on the text in the field, then select
type_http_stk_data. Select the rulegroup you want to use to filter GET requests (for example, ).Python:
self.response_stack["GET"]=(HTTP_STK_DATA, (V_STACK_PROVIDER, "CF", "http_get"))
Copyright: © 2021 Balasys IT Security
Send your comments to support@balasys.hu