3. Procedure – Configuring CF
Purpose:
To filter HTTP traffic for viruses in PNS, first CF has to be configured. The following configuration will use mostly default options, but it will enable the trickling option (by default, trickling is disabled). A size limit for the files to be inspected will also be set, that is, an action will be set for files that are considered too large and will not be inspected for viruses. Complete the following steps.
The configurations, including the default configuration options can be set without using MC by editing the configuration files of CF. The exact configurations are shown at the end of this tutorial.
Steps:
If you have not already done, add the component to the host that will be used for Content Filtering. For details, see Procedure 3.2.1.3.1, Adding new configuration components to host in Proxedo Network Security Suite 2 Administrator Guide.
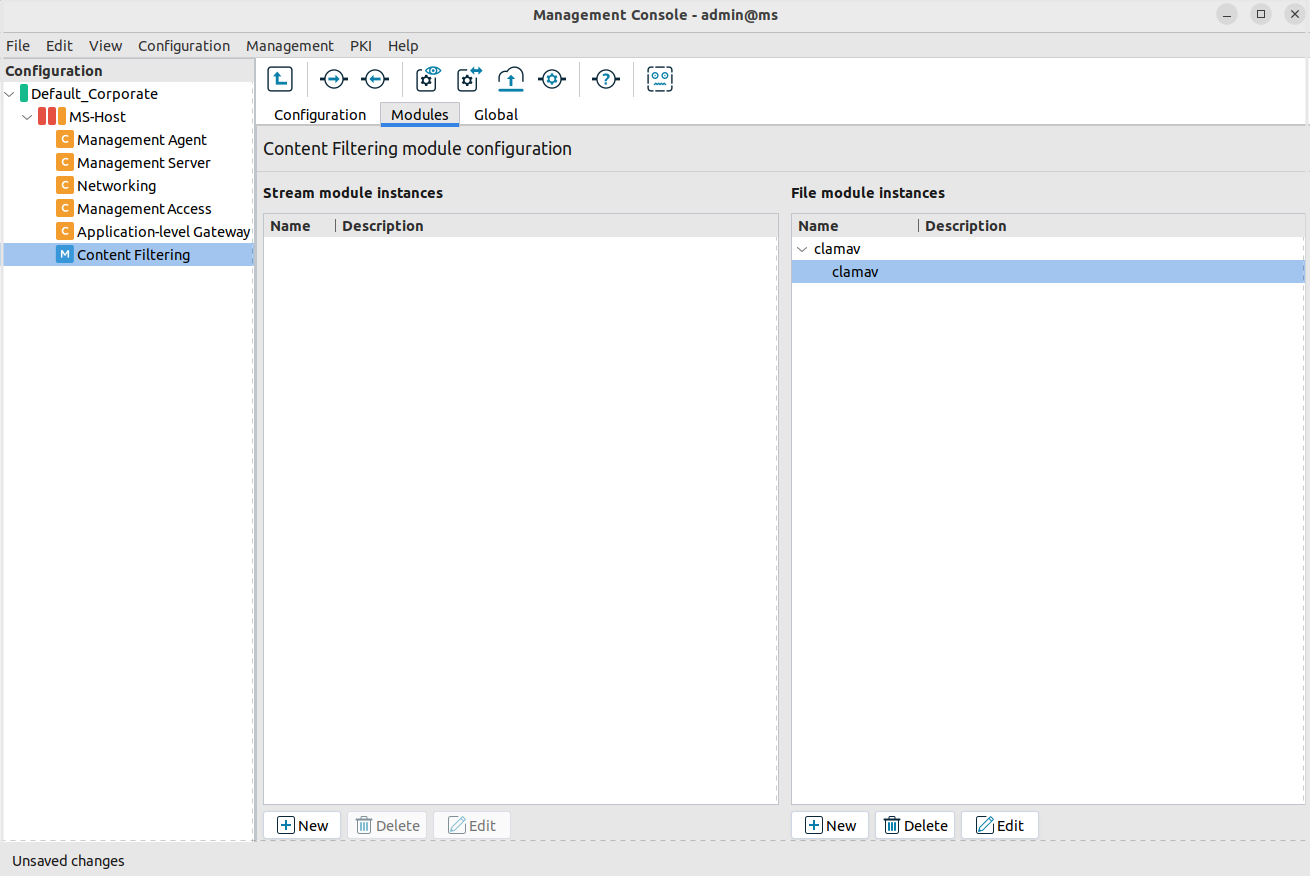
Create a new module instance of a virus-filtering module.
Select .
Enter a name for the instance.
Select the virus-filtering module (for example,
clamav) you want to use to scan the traffic in the field.Click .
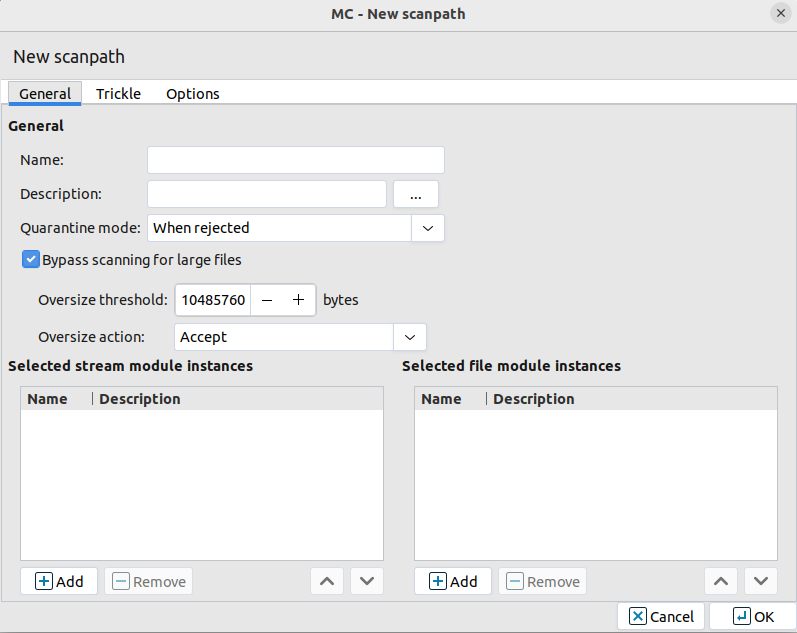
Configure a new scanpath.
Select , and enter a name for the new scanpath (for example,
http).Select the .
Set the option to
Accept.Optional Step: Adjust the option.
The size of the largest object to scan is specified in bytes in the parameter (the default value is
10485760, that is, 10MB). It might be useful to set it to a lower value: remaining by the above bandwidth example, downloading a 10MB file takes ~5 minutes. However, from a security point of view, there is only slight difference between filtering files up to 10MB, 5MB or 2MB. The vast majority of viruses spreads in files under 1MB. Naturally, if the threshold is higher, less data is allowed to pass without scanning, but viruses and other malicious contents are typically only 50-200KB. If the size limit is only 2 MB, large files are trickled only for ~1 minute, so the user has to wait much less. Set to either 2097152 (2MB) or 5242880 (5MB).
Select , and select the module created in Step Step 2 (for example,
clamav), then click .Select the option to enable trickling, then click .
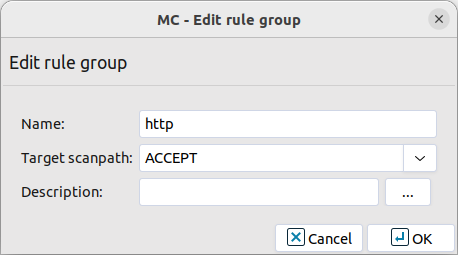
Select , and enter a name for the new rulegroup (for example,
http).Select the scanpath created in Step Step 3 in the field.
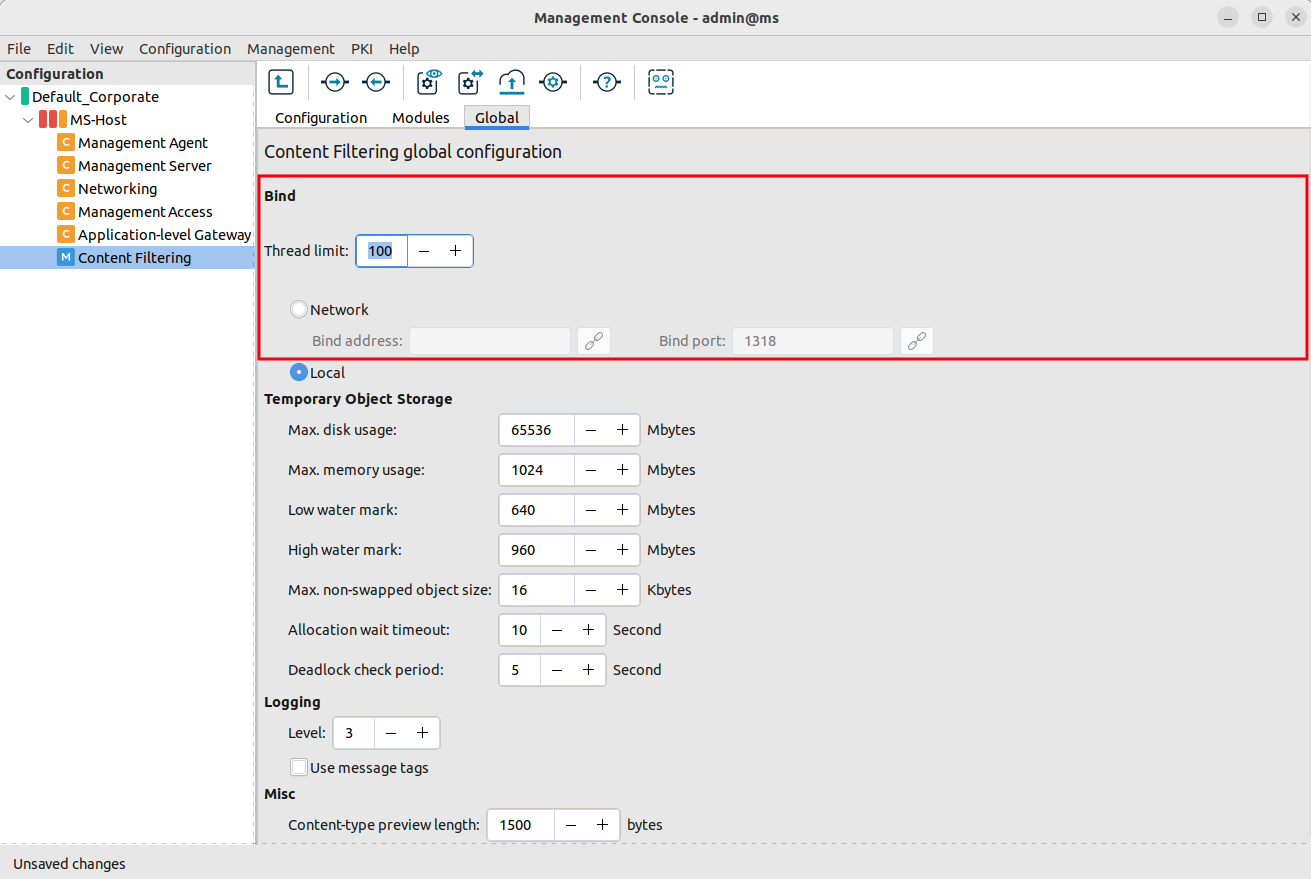
Select the tab, and configure how CF accepts connections from PNS.
If Application-level Gateway and CF are running on the same host, select the option.
Otherwise specify the IP address where CF should bind to.
Copyright: © 2021 Balasys IT Security
Send your comments to support@balasys.hu