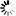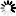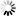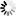When configured according to this tutorial, the policy.py file of Zorp should look something like this:
Configuring HTTPS proxying:
class HttpsProxy(HttpProxy):
def config(self):
HttpProxy.config(self)
self.ssl.client_keypair_files=\
("/etc/key.d/Certificate_for_SSL_proxying/cert.pem",\
"/etc/key.d/Certificate_for_SSL_proxying/key.pem")
self.ssl.client_verify_type=SSL_VERIFY_NONE
self.ssl.client_connection_security = SSL_FORCE_SSL
self.ssl.server_connection_security = SSL_FORCE_SSL
self.ssl.server_cagroup_directories= \
("/etc/ca.d/groups/ZMS_Trusted_CA/certs/",\
"/etc/ca.d/groups/ZMS_Trusted_CA/crls/")
self.ssl.server_disable_proto_sslv2=TRUENontransparent version:
class HttpSNonTransparent(HttpProxyNonTransparent):
def config(self):
HttpProxyNonTransparent.config(self)
self.connect_proxy= HttpsProxy
self.request["GET"]=HTTP_REQ_ACCEPT
self.request["POST"]=HTTP_REQ_ACCEPT
self.request["HEAD"]=HTTP_REQ_ACCEPT
self.request["CONNECT"]=HTTP_REQ_ACCEPTOne-sided HTTPS and Microsoft Outlook Web Access:
class OnesidedHttpsProxy(HttpsProxy):
def config(self):
HttpsProxy.config(self)
self.ssl.server_connection_security=SSL_NONE
self.ssl.server_keypair_files = \
("/etc/key.d/Sample Certificate/cert.pem",\
"/etc/key.d/Sample Certificate/key.pem")
self.stack_proxy=(Z_STACK_PROXY, OWAHttpProxy)
class OWAHttpProxy(HttpProxy):
def config(self):
HttpProxy.config(self)
self.request_header["Front-End-Https"]=(HTTP_HDR_INSERT, "on")HTTP Proxy using stream editor
class HttpSedProxy(OnesidedHttpsProxy):
def config(self):
OnesidedHttpsProxy.config(self)
self.response_stack["*"]=(HTTP_STK_DATA, (Z_STACK_PROGRAM, "sed -e 's|http://|https://|g'"))Transferring certificate information in an HTTP header
class HttpsCertProxy(OnesidedHttpsProxy):
def config(self):
OnesidedHttpsProxy.config(self)
self.request_header["X-User-Certificate"]=(HTTP_HDR_INSERT, self.tls.client_peer_certificate.subject)Name-based virtual hosting and sidestacking:
class HttpProxyTargetByHostHeader(HttpProxy):
def config(self):
HttpProxy.config(self)
self.request_header["Host"]=(HTTP_HDR_POLICY, self.TargetByHostHeader)
self.ssl.client_connection_security=SSL_FORCE_SSL
self.ssl.server_connection_security=SSL_NONE
self.ssl.server_keypair_files = \
("/etc/key.d/Sample Certificate/cert.pem",\
"/etc/key.d/Sample Certificate/key.pem")
def TargetByHostHeader(self, name, value):
if (value == "example.com"):
self.session.setServer(SockAddrInet("192.168.0.1", 80))
return HTTP_HDR_ACCEPT
elif (value == "example2.com"):
self.session.setServer(SockAddrInet("192.168.0.2", 80))
return HTTP_HDR_ACCEPT
return HTTP_HDR_ABORTPublished on May 30, 2024
© BalaSys IT Ltd.
Send your comments to support@balasys.hu