Copyright © 1996-2024 Balasys IT Zrt. (Private Limited Company)
Copyright © 2024 Balasys IT Zrt. All rights reserved. This document is protected by copyright and is distributed under licenses restricting its use, copying, distribution, and decompilation. No part of this document may be reproduced in any form by any means without prior written authorization of Balasys.
This documentation and the product it describes are considered protected by copyright according to the applicable laws.
This product includes software developed by the OpenSSL Project for use in the OpenSSL Toolkit (http://www.openssl.org/). This product includes cryptographic software written by Eric Young (eay@cryptsoft.com)
Linux™ is a registered trademark of Linus Torvalds.
Windows™ 10 is registered trademarks of Microsoft Corporation.
The Balasys™ name and the Balasys™ logo are registered trademarks of Balasys IT Zrt.
The Zorp™ name and the Zorp™ logo are registered trademarks of Balasys IT Zrt.
AMD Ryzen™ and AMD EPYC™ are registered trademarks of Advanced Micro Devices, Inc.
Intel® Core™ and Intel® Xeon™ are trademarks of Intel Corporation or its subsidiaries in the U.S. and/or other countries.
All other product names mentioned herein are the trademarks of their respective owners.
DISCLAIMER
Balasys is not responsible for any third-party websites mentioned in this document. Balasys does not endorse and is not responsible or liable for any content, advertising, products, or other material on or available from such sites or resources. Balasys will not be responsible or liable for any damage or loss caused or alleged to be caused by or in connection with use of or reliance on any such content, goods, or services that are available on or through any such sites or resources.
May 30, 2024
Table of Contents
- Preface
- Summary of changes
- 1. System requirements
- 2. Account requirements
- 3. Installing Zorp on Ubuntu
- 4. Configuring Zorp components
- 4.1. Configuring the Zorp modules
- 4.1.1. Configuring Postfix
- 4.1.2. ZCV — Configuring the zorp-utils package
- 4.1.3. ZCV — Configuring the NOD32 virus filtering modules
- 4.1.4. Configuring One Time Password for initial connection to ZMSs
- 4.1.5. Configuring Zorp Management Server (ZMS)
- 4.1.6. Selecting the role of the host
- 4.1.7. End-User License Agreement
- 4.1.8. Installing the electronic license keys
- 4.2. Upgrading Zorp hosts using apt
- 5. Installing the Zorp Management Console
- 6. Installing the Zorp Authentication Agent (ZAA)
- 7. Installing packages manually
- A. Further readings
- A.1. Zorp-related material
- A.2. General, Linux-related materials
- A.3. Postfix documentation
- A.4. BIND Documentation
- A.5. NTP references
- A.6. SSH resources
- A.7. TCP/IP Networking
- A.8. Netfilter/IPTables
- A.9. General security-related resources
- A.10. syslog-ng references
- A.11. Python references
- A.12. Public key infrastructure (PKI)
- A.13. Virtual Private Networks (VPN)
- B. Zorp Professional End-User License Agreement
- B.1. 1. SUBJECT OF THE LICENSE CONTRACT
- B.2. 2. DEFINITIONS
- B.3. 3. LICENSE GRANTS AND RESTRICTIONS
- B.4. 4. SUBSIDIARIES
- B.5. 5. INTELLECTUAL PROPERTY RIGHTS
- B.6. 6. TRADE MARKS
- B.7. 7. NEGLIGENT INFRINGEMENT
- B.8. 8. INTELLECTUAL PROPERTY INDEMNIFICATION
- B.9. 9. LICENSE FEE
- B.10. 10. WARRANTIES
- B.11. 11. DISCLAIMER OF WARRANTIES
- B.12. 12. LIMITATION OF LIABILITY
- B.13. 13.DURATION AND TERMINATION
- B.14. 14. AMENDMENTS
- B.15. 15. WAIVER
- B.16. 16. SEVERABILITY
- B.17. 17. NOTICES
- B.18. 18. MISCELLANEOUS
- C. Creative Commons Attribution Non-commercial No Derivatives (by-nc-nd) License
List of Procedures
- 3.1. Installing Ubuntu Server
- 3.2. Installing Zorp on a Ubuntu server
- 4.1.1. Configuring Postfix
- 4.1.2. ZCV — Configuring the zorp-utils package
- 4.1.3. ZCV — Configuring the NOD32 virus filtering modules
- 4.1.4. Configuring One Time Password for initial connection to ZMSs
- 4.1.5. Configuring Zorp Management Server (ZMS)
- 4.1.6. Selecting the role of the host
- 4.1.8.1. Installing the license keys from the network
- 4.2. Upgrading Zorp hosts using apt
- 5.1. Installing ZMC on Debian/GNU Linux
- 5.2. Installing ZMC on Microsoft Windows
- 6.1.1. Installing the Zorp Authentication Agent on Microsoft Windows
- 6.1.2. Installing Zorp Authentication Agent with Group Policy Object (GPO) deployment
- 6.2. Installing Zorp Authentication Agent on Linux platforms
This guide is intended for use by system administrators and consultants responsible for network security and whose task is the configuration and maintenance of Zorp firewalls. Zorp gives them a powerful and versatile tool to create full control over their network traffic and enables them to protect their clients against Internet-delinquency.
This guide is also useful for IT decision makers evaluating different firewall products because apart from the practical side of everyday Zorp administration, it introduces the philosophy behind Zorp without the marketing side of the issue.
The following skills and knowledge are necessary for a successful Zorp administrator.
| Skill | Level/Description |
|---|---|
| Linux | At least a power user's knowledge is required. |
| Experience in system administration | Experience in system administration is certainly an advantage, but not absolutely necessary. |
| Programming language knowledge | It is not an explicit requirement to know any programming languages though being familiar with the basics of Python may be an advantage, especially in evaluating advanced firewall configurations or in troubleshooting misconfigured firewalls. |
| General knowledge on firewalls | A general understanding of firewalls, their roles in the enterprise IT infrastructure and the main concepts and tasks associated with firewall administration is essential. To fulfill this requirement a significant part of Chapter 3, Architectural overview in the Zorp Administrator's Guide is devoted to the introduction to general firewall concepts. |
| Knowledge on Netfilter concepts and IPTables | In-depth knowledge is strongly recommended; while it is not strictly required definitely helps understanding the underlying operations and also helps in shortening the learning curve. |
| Knowledge on TCP/IP protocol | High level knowledge of the TCP/IP protocol suite is a must, no successful firewall administration is possible without this knowledge. |
Table 1. Prerequisites
The Zorp Distribution DVD-ROM contains the following software packages:
Current version of Zorp 7 packages.
Current version of Zorp Management Server (ZMS) 7.
Current version of Zorp Management Console (ZMC) 7 (GUI) for both Linux and Windows operating systems, and all the necessary software packages.
Current version of Zorp Authentication Server (ZAS) 7.
Current version of the Zorp Authentication Agent (ZAA) 7, the ZAS client for both Linux and Windows operating systems.
For a detailed description of hardware requirements of Zorp, see Chapter 1, System requirements.
For additional information on Zorp and its components visit the Zorp website containing white papers, tutorials, and online documentations on the above products.
This product is developed and maintained by Balasys IT Zrt..
Contact:
Balasys IT Zrt.
4 Alíz Street
H-1117 Budapest, Hungary
Tel: +36 1 646 4740
E-mail: <info@balasys.hu>
Web: http://balasys.hu/
You can directly contact us with sales related topics at the e-mail address
<sales@balasys.hu>, or leave us your contact information and we call you back.
To access the Balasys Support System, sign up for an account at the Balasys Support System page. Online support is available 24 hours a day.
Balasys Support System is available only for registered users with a valid support package.
Support e-mail address: <support@balasys.hu>.
Balasys IT Zrt. holds courses on using its products for new and experienced users. For dates, details, and application forms, visit the https://www.balasys.hu/en/services#training webpage.
This guide is a work-in-progress document with new versions appearing periodically.
The latest version of this document can be downloaded from https://docs.balasys.hu/.
Any feedback is greatly appreciated, especially on what else this document should cover, including protocols and network setups. General comments, errors found in the text, and any suggestions about how to improve the documentation is welcome at <support@balasys.hu>.
The following changes have been made to the document between releases Zorp 7.0.18 and Zorp 7.0.19:
| Description of the change | Place in the document |
|---|---|
The information on which platform ZAA and ZMC can be installed on has been updated. |
For the changes, see Chapter 5, Installing the Zorp Management Console and Chapter 6, Installing the Zorp Authentication Agent (ZAA). |
Table 2. Summary of Changes
The following changes have been made to the document between releases Zorp 7.0.14 and Zorp 7.0.15:
| Description of the change | Place in the document |
|---|---|
Step 3 for procedure Installing Zorp on Ubuntu server has been rephrased. |
For the changes, see Procedure 3.2, Installing Zorp on a Ubuntu server. |
Table 3. Summary of Changes
This section outlines hardware and software requirements for running Zorp on your firewall.
CPU: Zorp requires a 64-bit capable x86-64 processor (for example, Intel Core i series, Intel Xeon, AMD Ryzen, AMD EPYC, and so on).
Memory: At least 4 GB main memory is recommended, though 2 GB is acceptable on systems with low load.
Disk: Though Zorp itself requires less than 8 GB of disk space, 256 GB or larger disk space is recommended to have enough space for log files, for example.
Hardware compatibility: Zorp runs on Ubuntu, currently using version 4.15 of the Linux kernel. Most hardware supported by Linux is also supported by Zorp.
| Note |
|---|
Make sure to install Zorp on hardware that is Ubuntu Server certified. For a list of Ubuntu Server certified hardware, see Ubuntu Server certified hardware. |
| Tip |
|---|
Use disks designed for servers: other disks are not planned for 24/7 usage, and to participate in RAID sets. Use 2 or more redundant disks in a RAID array to prevent data loss and downtime (the Zorp installer supports software RAID mirroring). |
For details on sizing a Zorp host, see Section 1.1.1, Sizing Zorp hosts.
| Tip |
|---|
A modern 1- or 2-unit-high server with remote management port is usually an optimal solution. Its size depends on the number of required LAN ports. Use reliable or brand hardware for your firewall with dual power supply and UPS. |
Correctly sizing the hardware is a difficult task. Actual hardware requirements of a running system depend on several factors, and taking everything into account is rarely possible. The three most demanding aspects of transmitted traffic are: number of new/parallel sessions, bandwidth, and log subsystem settings.
Number of new/parallel sessions:
The number of parallel sessions directly affects memory and CPU usage. In addition to standard operating system memory requirements, Zorp uses memory for each established session. Usually, the following factors have to be taken into account:
OS: 64-128 MB is sufficient for the OS to operate.
Per Zorp instance: For each and every running Zorp instance about 10-20 MB is required depending on the complexity of the configuration (zones, proxies, services, and so on).
Per session: For each additional session about 200 kB is needed (kernel socket buffers, thread-specific data, dynamic proxy state information, and so on).
On an average firewall handling 500 sessions in 10 instances approximately 256-768 MB RAM is required. The required memory really depends on the complexity of the policy (content filtering can really increase the needs due to the various data buffers).
The question now is how many sessions a given number of clients generate. It can be assumed that peak load is caused by HTTP traffic, which is the most demanding application on the Internet today. Each object on the World Wide Web is fetched by a separate session of HTTP if keep-alive connections are not allowed, and a single web page consists of many objects as each picture is an object on its own. If keep-alive is allowed then only a few sessions are used by a client, and a good estimate is that a single browser opens four sessions simultaneously to fetch a page and additional graphics. Therefore, if you had 100-120 clients browsing constantly, your firewall would have to handle 400-480 sessions at a time as a peak.
Bandwidth:
Bandwidth adds another aspect to hardware requirements. You might need a single session only, but that single session could require 155 Mbit/sec fully saturated. This defines CPU requirements, but this is much more difficult to estimate. The CPU power is required mainly by session startup and by complex policies (for example, lot of customizations). Of course the bandwidth is important too. An average 2-3 GHz CPU with enough memory can handle about 50-100-150 new sessions per second depending on the type of traffic.
For performance tests, contact your Zorp Support Partner.
Log subsystem settings:
Default log settings of Zorp generate about 3-400 bytes of log messages for a single session. On a firewall serving 100000 sessions a day, this means 30-40MB of log messages. Increasing the verbosity level adds to this amount. You should carefully fine-tune the logging subsystem by selecting the messages you are really interested in, thus decreasing both storage and runtime demands.
ZMS and ZAS do not require many resources — a virtual machine can be adequate.
Minimal hardware configuration:
Processor: At least a 64-bit capable x86-64 processor
Memory: 1 GB RAM
Hard disk: A minimum of 2 GB, but significant amount of additional space can be required for logging.
Content vectoring can consume significantly more resources then a simple Zorp host. The exact requirements depend heavily on the actual traffic and the type and extent of the content analysis. In general, use the hardware requirements of Zorp hosts.
Minimal hardware configuration:
Processor: x86 or a x86-64 CPU
OS: A graphical operating system. ZMC runs on Debian GNU/Linux with X Window System, and on Microsoft Windows 10.
Memory: At least 512 MB free RAM space
-
Hard disk: A minimum of 310 MB disk space is required.
If you plan to install ZMC on Microsoft Windows and do not want to install the documentation together with ZMC, 30 MB of free disk space will be enough.
This section describes the details on the account types that will be required at certain points of the installation or upgrade process.
You will need a personal account to access the following sites:
download.balasys.hu
upload.balasys.hu
support.balasys.hu
The personal account is also used to download files manually.
To register a personal account, send an email to <sales@balasys.hu> with the following personal data:
full name
phone number
company name
job title
| Note |
|---|
|
During a product evaluation period, the Sales Department grants time-limited access rights for the personal account. After closing a sales process, access is granted for the required number of employees of the organization and a technical account is created. For details on a technical account, see Section 2.2, Technical account |
You will need a Balasys Support System technical account to access the following sites:
apt.balasys.hu
The technical account is not used for manual access, but for machine access. For example, it is used to upgrade Zorp hosts using apt.
| Note |
|---|
|
During a product evaluation period, creating a technical account is not possible. After closing a sales process, a technical account is created automatically. |
This chapter describes how to turn an existing Ubuntu server into a Zorp host.
Before starting the installation, advance planning is necessary for a successful firewall implementation. All the critical network parameters, such as firewall IP addresses, routing topology, DNS hierarchy, and so on must be known in advance.
The following IP addresses are particularly important:
IP address of the Zorp host
IP address of the ZMS host
IP address of ZMC
In addition, you must prepare the following:
Define firewall administration roles with a corresponding password policy.
Define a number of passwords that protect various elements of the system.
Record these passwords (according to the security policy of your organization) and keep them safe for later use.
| Note |
|---|
Zorp must be installed on Ubuntu 18.04 LTS. |
3.1. Procedure – Installing Ubuntu Server
Purpose:
To install Ubuntu Server, complete the following steps.
Prerequisites:
Make sure to install Ubuntu Server on a supported hardware. For hardware requirements, see Section 1.1, Hardware requirements for a Zorp Firewall host.
Steps:
Download Ubuntu 18.04 LTS from the Ubuntu Server downloads page.
Write the installer to an installer media. This is typically an USB drive.
-
Boot the system from the installer media and select the following options:
.
.
.
3.2. Procedure – Installing Zorp on a Ubuntu server
Purpose:
If you want to install Zorp on an existing Ubuntu server, complete the following steps.
Prerequisites:
An already installed Ubuntu 18.04 LTS server. Install only services and applications that you absolutely need. For details on installing Ubuntu Server, see Procedure 3.1, Installing Ubuntu Server.
Ensure that you have a working Balasys Support System registration and that have downloaded the required Zorp license files.
Steps:
Login to the host as root from a local console or using SSH.
-
Update your system and upgrade the Zorp-related packages. This is important, because there might be newer packages available. To update your system, enter the following commands:
sudo apt update sudo apt dist-upgrade
Note that during this step, some packages may be downgraded. This is normal.
-
Create the following mount point for the Zorp install medium:
sudo mkdir -p /media/cdrom
-
Mount the Zorp install medium to the previous mount point.
sudo mount /dev/cdrom /media/cdrom -o ro
-
To allow checking of Zorp package signatures by APT, install the Balasys GPG keys:
sudo /media/cdrom/install-balasys-archive-key.sh
-
Add Zorp package repositories to APT's list of available sources.
sudo apt-cdrom add
-
Install the Zorp components that you want to use on the host. Issue the following command: sudo apt-get install <Zorp-components-to-install>, where replace the
<Zorp-components-to-install>part of the command with the package names of the Zorp components that you want to use on the host. The following packages are available:-
:
zorpproduct-zorp -
:
zorpproduct-zms -
:
zorpproduct-zas -
:
zorpproduct-zcv
: The Zorp Management Server (ZMS) and its corresponding packages. ZMS — depending on its product license — can be installed on the Zorp firewall host or on a separate machine.(Package name:
zorpproduct-zms): The packages required for a firewall host. (Package name:
zorpproduct-zorp)Zorp URL filter: The package is required for the url filter. (package name:
zorpproduct-urlfilter.: The Zorp Authentication Server (ZAS) enables the authentication of network traffic on the user level at the firewall using password, CryptoCard, S/key, or X.509 methods. Integrating with existing Microsoft Active Directory, LDAP, PAM, and Radius databases is also supported. The module can be installed either together with the Zorp and ZMS modules or separately at a later date. (Package name:
zorpproduct-zas)-
: The Zorp Content Vectoring System (ZCV) is a framework and a uniform interface to manage various built-in and third party content vectoring modules (that is, virus and spam filtering engines). The content vectoring modules to be installed (in addition to the ZCV framework) can be selected from the following list. (Package name:
zorpproduct-zcv)Warning The ZCV framework and the content vectoring modules must be installed on the same host.
: This module contains the libraries and virus signature databases needed for using the ClamAV antivirus engine. (Package name:
zorpproduct-clamav): This module contains the libraries and virus signature databases needed for using the Eset NOD32 antivirus engine. (Package name:
zorpproduct-nod32): This module contains the libraries and databases needed for using the SpamAssassin spam filtering engine. (Package name:
zorpproduct-spamassassin): This module contains the libraries needed for using ModSecurity web application firewall (WAF) engine. (Package name:
zorpproduct-modsecurity)
For further information on the different modules, see the Chapter 14, Virus and content filtering using ZCV in Zorp Professional 7 Administrator Guide.
Below are some guidelines about which modules should be installed on the different types of machines.
When installing a single firewall (or a node of a cluster) that will be managed from a separate ZMS host, select only the component.
The third-party modules that can be used by ZCV must be licensed separately from Zorp. Select them only if you have a valid license for them, and only when you are installing the host that will run ZCV.
When installing a ZMS host that will manage one or more Zorp firewalls, but the machine itself will not be used as a firewall, select the (ZMS) component.
If you will use a single host as the firewall and ZMS, select the and the components. Also select and its required modules, and the component if you have purchased licenses for them.
(ZAS) is an optional, central authentication service that can be installed on a Zorp machine. If you have license for ZAS select it together with the component. This service must be licensed separately.
Note The and the (also called Satyr) applications are client–side components that cannot be installed on Zorp hosts. Their installation is discussed in Chapter 5, Installing the Zorp Management Console and Chapter 6, Installing the Zorp Authentication Agent (ZAA), respectively.
After choosing the modules to install, select .
Note When you continue the installation, some steps may not appear for you, depending on the components you have selected to install.
-
:
-
Umount the Zorp install medium from the file system.
sudo umount /dev/cdrom
Configure network interface bootstrap by ZMS.
-
Reboot the system:
sudo reboot
Repeat this procedure to install other hosts if needed for your environment.
If you have installed a Zorp Management Server (ZMS), install the Zorp Management Console (ZMC) application on the deskop of your Zorp administrators. For details, see Chapter 5, Installing the Zorp Management Console.
The installation process can be divided into three main parts:
Configuring native services and the Zorp modules: This phase installs and configures the components of Zorp (for example ZMS, ZAS, and so on). Numerous other services (like the mail transfer agent (Postfix), Secure Shell and IPSec access, and so on) are also configured in this phase. See Section 4.1, Configuring the Zorp modules for details.
Installing ZMC: In order to access the Zorp Management Server (ZMS) remotely using the Zorp Management Console (ZMC), ZMC has to be installed on the machine from which Zorp hosts will be administered. The IP address of this machine has to be known in advance, as during the installation ZMS has to be configured to accept connections from this machine. See Chapter 5, Installing the Zorp Management Console for details.
| Note |
|---|
Starting with version 3.4 the Zorp Installation DVD is only available in 64-bit (amd64). |
Zorp has an easy-to-use text-based installer requiring only a keyboard (mouse is not needed nor supported by the installer). Navigation between the different options of a screen is possible using the cursor buttons. Selected actions (for example or ) is highlighted in red. When multiple selection is possible use space to select/deselect a given item (for example when selecting the Zorp modules to be installed).
4.1.1. Procedure – Configuring Postfix
Purpose:
Zorp uses Postfix as a native service for handling emails. A mail transferring agent (MTA) must be installed on the machine at least for delivering the locally generated messages.
Steps:
-
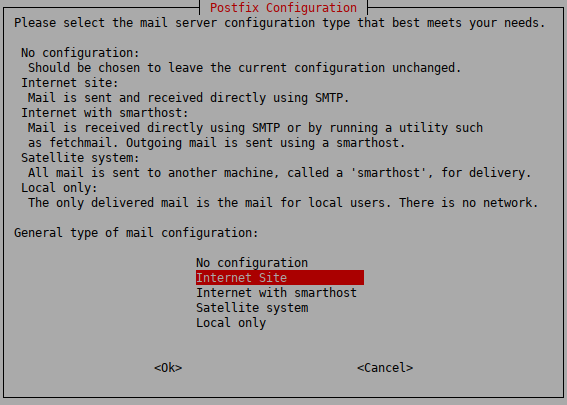
Select the mail server configuration that best meets your needs. The following options are available:
: No configuration changes will be done. Use this option if a working Postfix configuration is already available on the host, or if you wish to configure Postfix manually from ZMC.
: Sending and receiving mails is possible by using SMTP directly. This option is suitable in the most common scenarios.
: Mails are received either by using SMTP directly or by running a utility such as fetchmail. Outgoing messages are sent through another machine (a smarthost).
: No mail is received locally. Root and postmaster mails are handled according to
/etc/aliases. All messages are sent to another machine (a smarthost) for delivery.: Mails are only delivered locally on the machine for local users. There is no network.
-
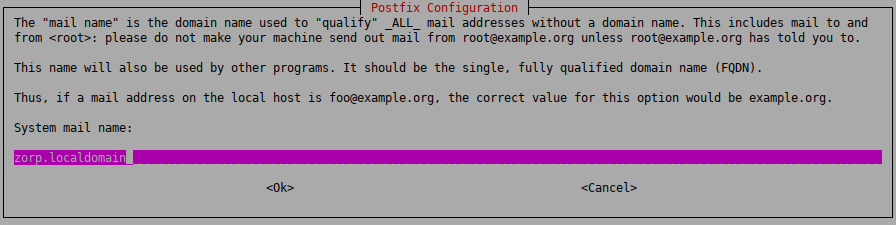
Enter the name that should appear in the domain part of the outgoing mail (that is, after the
@character). This name will also be used by other programs. It should be the fully qualified domain name (FQDN).
4.1.2. Procedure – ZCV — Configuring the zorp-utils package
Purpose:
If you are installing ZCV, then configure the zavupdate tool that updates the databases of the virus filtering engines:
Steps:
-
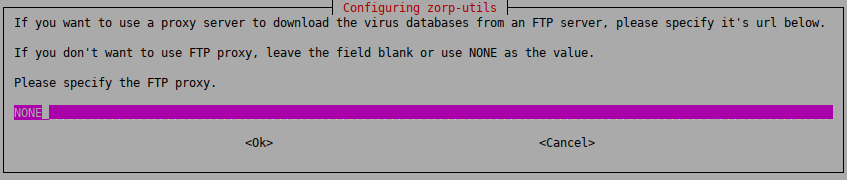
: The
zavupdateapplication can download database updates through FTP or HTTP. Enter the URL of the FTP proxy to be used (orNONEif the updates can be downloaded directly without using a proxy server).
-
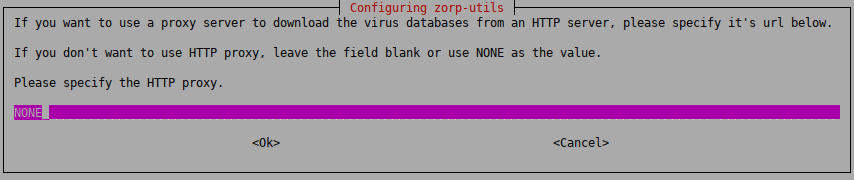
: The
zavupdateapplication can download database updates through FTP or HTTP. Type the URL of the HTTP proxy to be used (orNONEif the updates can be downloaded directly without using a proxy server).
-
:
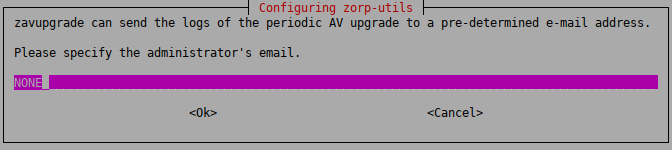
zavupdatecan send the logs of the periodic antivirus (AV) update to the administrator through email. Type the address of the administrator and the subject to be used in these emails. If you do not want email notifications, enterNONE.Note It is not advised to use a personal email address. Instead, use an address of a shared folder that can be accessible to whom it belongs. It can also be the address of a mailing list. In this way, more than one administrator can be notified at the same time, and the archive of the messages can be accessed by more than one administrator.
-
:
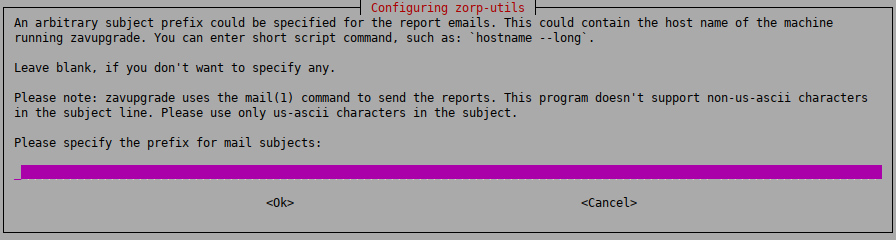
zavupdatecan add a prefix to the subject of the emails it sends to make sorting the messages easier for the administrator. Type a prefix (for example the name of the host in square brackets), or leave these fields blank. You can use command subtitution using backticks (`) to include the output of any Linux shell command in the subject. This command will be run before sending the email and the output of the command will be the prefix of the email.Note This setting can only be changed manually later. Therefore, make sure that you enter a value that you will not want to change.
As a best practice, use a command rather than a fixed name. A command will dynamically follow the changes to your infrastructure, however, a fixed name will not. For example, if you use the name of the host
myhost1and later you rename your hostmyhost2, you will still be receiving emails with themyhost1prefix and that can be confusing.In practice, it can be used in your mail client (or on the mail server) to move these mails (with the given prefix) automatically to a subfolder in the inbox. Also, it can be used to differentiate between emails originating from several firewalls. This can be especially useful if, for example, you have several firewalls and you want to easily identify the firewall that had an unsuccessful update.
Note If you want to change this setting later, you can reconfigure zorp-utils with the following terminal command:
dpkg-reconfigure zorp-utils
-
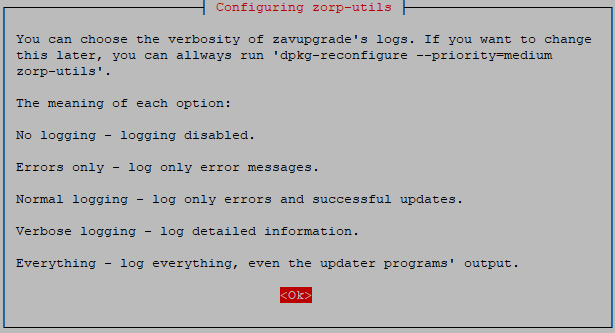
: Select the level of verbosity of
zavupdate.First the
zavupdateoptions are displayed:Each level includes the logs of the levels above, for example, will include all errors and successful update messages too.
: logging is disabled
: only error messages are logged
: error messages and successful updates are logged
: detailed logging
: everything is logged, including the output of the update programs of ClamAV and/or NOD32
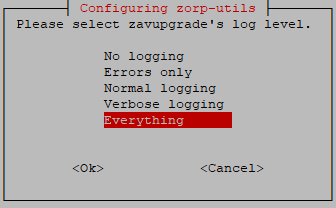
Then you can select the actual log level:
-
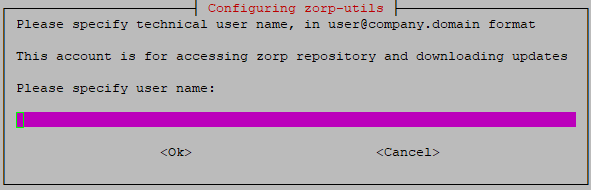
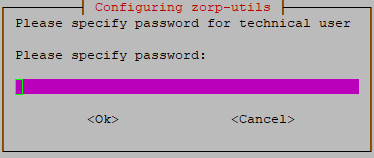
Specify the firewall's Balasys Support System technical account username and password to enable the firewall to access the Zorp repository and to download the updates.
-
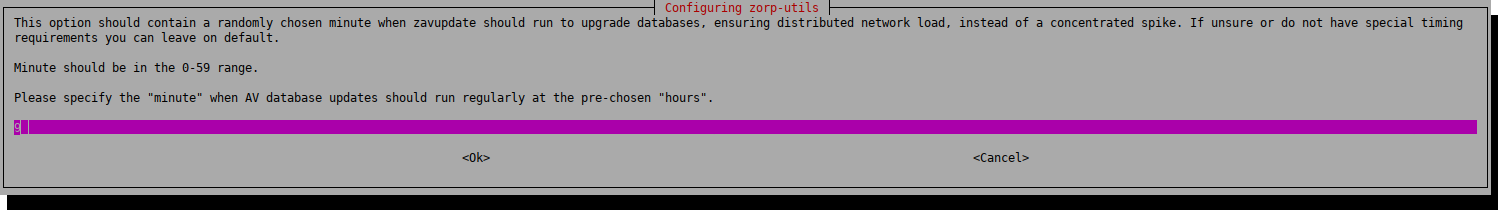
Specify the actual minutes when the zavupdate process shall start in every hour. In case the necessary licenses are also purchased for the URL filter database, the upgrade for the URL database will also be performed as part of the zavupgade process. The upgrade for the URL filter database though will be performed only in the hours being specified in the next step.
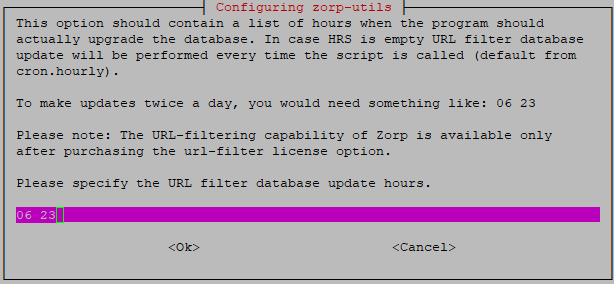
-
Specify the timing for the URL filter database: Specify the actual hours when the upgrade of the URL filter database shall take place. Provide the actual hours for the time of the upgrade.
-
Fill in this field only if it is required. (optional step)
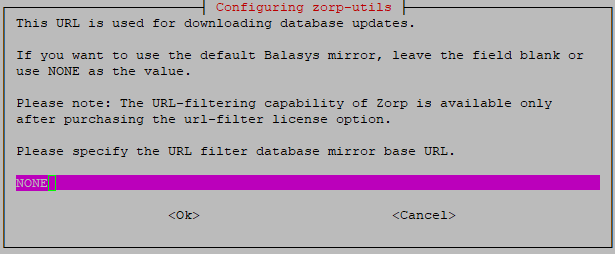
In specific cases, based on an agreement between Balasys and the customer, the customer has a mirror URL filtering database. The location of this mirror database can be specified here.
In any other cases, please leave this field empty or add the value NONE.
-
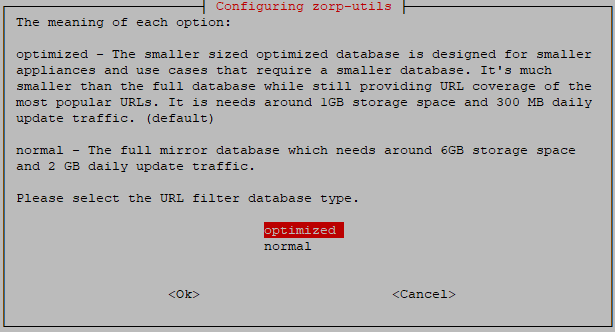
Choose the size of the URL filter database.
At this stage, the administrator can choose the size of the URL filtering database. The database can be a smaller-sized, optimized database (the recommended version) for usual scenarios, which requires 1 GB storage space and 300 MB daily update traffic, or a normal database for more extensive scenarios, which requires 6 GB storage space and 2 GB daily update traffic. If there are no specific needs, we recommend to choose the optimized database.
4.1.3. Procedure – ZCV — Configuring the NOD32 virus filtering modules
Purpose:
If you are installing ZCV with the NOD32 module, complete the following steps:
Steps:
-
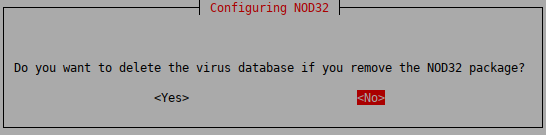
To delete the virus database if you remove the NOD32 package, select .
-
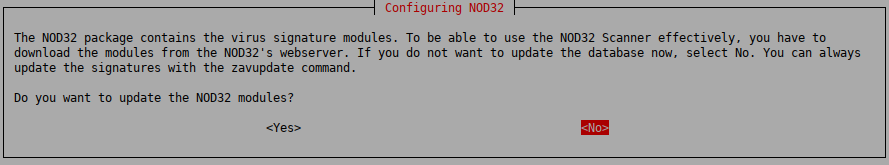
To be able to use the NOD32 Scanner effectively, you have to update the NOD32 virus database. The databases of the NOD32 module can be instantly updated from the official NOD32 webserver if the machine you are installing Zorp on has network access.
To update the NOD32 module, select .
Otherwise, you can start an update using the zavupdate command later.
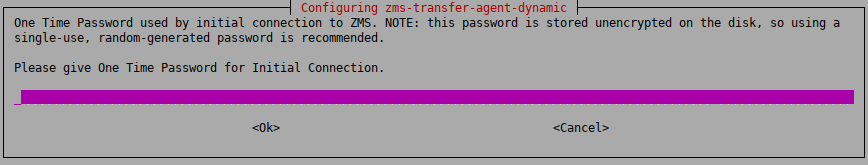
4.1.4. Procedure – Configuring One Time Password for initial connection to ZMSs
Purpose:
If the host you are installing will be managed from ZMS, you have to configure a One Time Password (OTP) for connecting to ZMS the first time. To configure the initial OTP, complete the following steps.
Steps:
-
Type a One Time Password that will be used to connect to ZMS for the first time. Subsequent connections will be mutually authenticated using X.509 certificates.
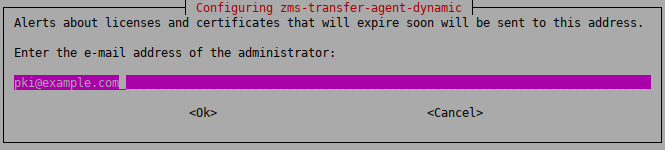
-
To receive email alerts from ZMS before a certificate or license used in Zorp expires, type the email address of the administrator who will receive these alerts.
4.1.5. Procedure – Configuring Zorp Management Server (ZMS)
Purpose:
To configure Zorp Management Server, complete the following steps.
Steps:
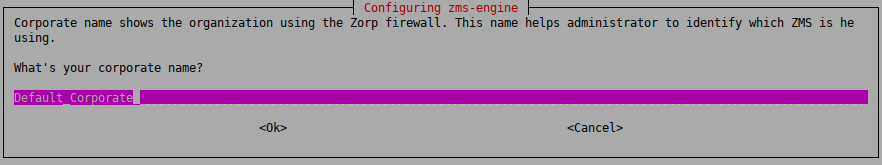
-
Configure the site name.
The hosts managed by ZMS are organized into sites. Use a descriptive name for the site, for example, the name of the company. This will help the administrator distinguish ZMSs from each other. Enter the site name.
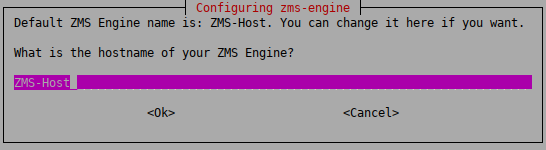
-
Configure the hostname of the ZMS Engine.
It is recommended to enter the normal hostname, but do not use FQDN. The default value is
ZMS-Host.Warning Make sure to enter the correct hostname, because it is stored in the ZMS database and is complicated to modify later.
-
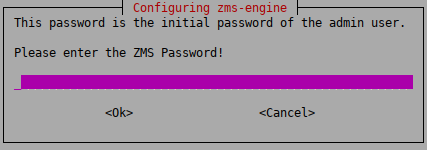
Configure the initial password of the administrator user on ZMS.
Enter the ZMS administrator password. This password is used to login to ZMS from the Zorp Management Console as an administrator, and configure the Zorp firewalls. The username of the administrator by default is
admin, which can be modified later. The password can be changed later at any time.Note Make sure to create a password that conforms to the secure password generation standards of your organization.
Store the password in a secure way.
-
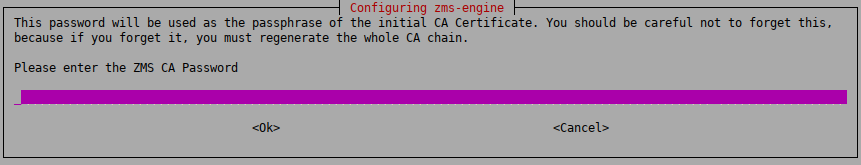
Configure the Certificate Authority of ZMS.
Enter a secure password for the Certificate Authority (CA) of ZMS. This password will be used as the passphrase of the initial CA certificate.
Note Make sure to create a password that conforms to the secure password generation standards of your organization.
Store the password in a secure way.
Warning Make sure to enter the correct CA password. It is difficult to change the CA password later and requires regenerating the whole CA chain.
-
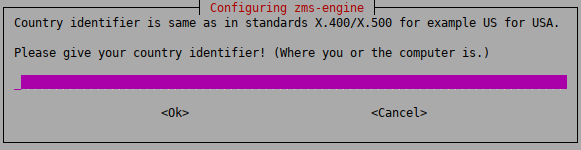
Create the root Certificate Authority.
ZMS includes public key infrastructure (PKI) management to ensure that each element of the firewall system (ZMS module, VPNs, users) can be authenticated with X.509 certificates. During this stage of the installation the root CA is created and configured. Provide the following parameters.
Warning Do not use accented characters. They are not supported in the X400/X500 standard.
: two characters only. For example,
US,DE,HU.: Optional. United States (
US) only. For example,Nevada.: Optional. For example,
Las Vegas.: Optional. For example,
Example Ltd..: Optional. For example,
IT department.
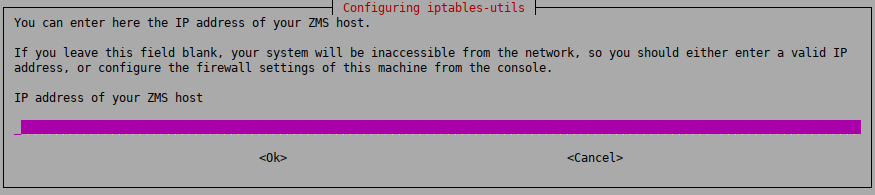
4.1.6. Procedure – Selecting the role of the host
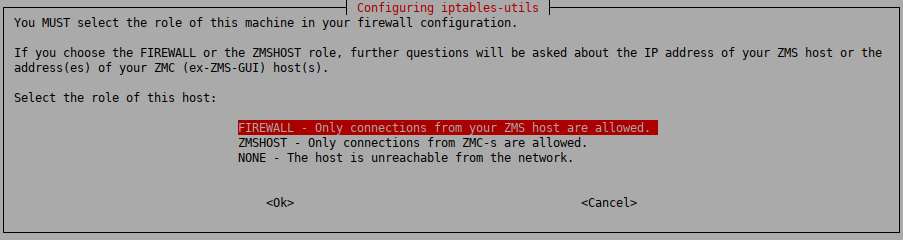
Purpose:
By default, the iptables utility denies any traffic going through or to the machine. The installer configures the iptables utility according to the role of the host. This selection affects only the first installation of the host, it will not modify an existing iptables configuration.
Steps:
-
Select the role of this machine in your firewall configuration. The following roles are available:
-
: Only connections from the ZMS host are allowed.
Select this role when you are installing a firewall host, or any other standalone host that will be managed from ZMS.
ZMS agent and remote shell (SSH) communication will be enabled. This technically means ports TCP/1311 and TCP/22.
-
: Only connections from ZMCs are allowed.
Select this role if you are installing the Zorp firewall and the Zorp Management Server on the same host.
ZMC to engine communication and remote shell communication will be allowed on ports TCP/1314 and TCP/22, respectively.
-
: The host is unreachable from the network.
All IP traffic will be dropped by default, therefore all remote administration attempts will fail. All allowed traffic has to be enabled manually from a local terminal.
-
-
If you have selected the or the role, enter its IP addresses:
FIREWALL: The IP address of the ZMS host used to manage the firewall.
ZMSHOST: The IP address of the ZMC used to manage the ZMS host (that is, the machines from where the firewall administrators will connect to ZMS). If managing ZMS is allowed from multiple hosts, separate the IP addresses of these hosts with spaces.
Warning Make sure that you type the IP adresses of the ZMS/ZMC hosts correctly.
Otherwise, the machine will not be accessible from ZMS/ZMC. In this case, you must manually correct the configuration of
iptables. For details, see man iptables-utils.
You must accept the End-User License Agreement before starting the actual installation. After reading and understanding the End-User License Agreement, select to accept it.
The complete text of the EULA is also available in Appendix B, Zorp Professional End-User License Agreement.
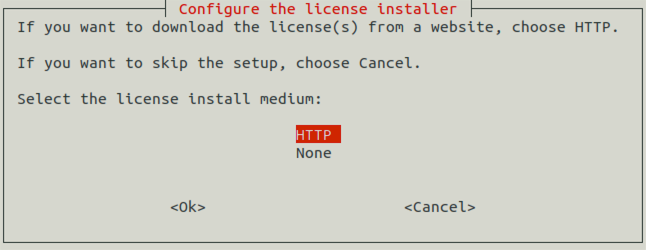
You can download the license keys from Balasys Support System using a Balasys account. The installer can download them from a webserver using HTTP if network connection for the machine is available during the installation. Besides the license file(s), no online activation or similar activity is required.
| Warning |
|---|
|
Zorp and its components will not operate without the new license files. If you fail to install the new licenses during the upgrade, you must copy the license files to the host manually to the following locations:
|
| Note |
|---|
|
When accessing the licenses, the directory structure is important: for each Zorp component licensed, there is a separate subdirectory named after the component (for example, Zorp, ZMS, ZAS) containing a license file named The license files of 3rd-party engines are not necessary called |
4.1.8.1. Procedure – Installing the license keys from the network
Steps:
-
You can install the licenses through HTTP from your local webserver, Balasys does not provide online access to license keys. Select and enter the URL where the license is accessible. The URL can use the domain name or IP address of the server. If the installation of the licenses fails for any reason, they can also be installed manually at a later date.
If you want to use a proxy server to download the licenses from an HTTP server, select . Then specify the HTTP proxy in the next window. If you do not want to use a proxy server, leave the field blank or enter NONE.
If the installation was finished successfully, delete the electronic license(s) from the web server to prevent unauthorized downloads.
4.2. Procedure – Upgrading Zorp hosts using apt
Purpose:
All the components of Zorp can be upgraded using the standard apt tools. When used on Debian GNU/Ubuntu Linux systems, the Zorp Management Console (ZMC) and Zorp Authentication Agent (ZAA) client-side applications can be upgraded using apt as well. On Microsoft Windows and other Linux platforms, upgrades to these applications must be downloaded manually from Balasys downloads. To perform an upgrade, complete the following steps.
Prerequisites:
You will need a Balasys Support System technical account to perform the upgrade. You can register a technical account by sending an email to <sales@balasys.hu> with the following personal data:
full name
phone number
company name
job title
Make sure to remember your technical account credentials, because you will be asked to enter them during the installation of any Zorp component. Later, the APT configuration file /etc/apt/auth.conf is generated automatically using these credentials.
After registering an account, send an email with the subject REQUESTING ACCESS TO ZORP UPGRADES to <sales@balasys.hu> so that you receive the user rights required for downloading software updates.
Steps:
Login to the host locally, or remotely using SSH.
-
Before the first upgrade, complete the following steps:
Select .
-
To download always the latest Zorp release and security fixes, replace the contents of the file with the following (replace the USERNAME:PASSWORD part with your actual Balasys Support System technical account username and password)
deb [arch=amd64] https://USERNAME:PASSWORD@apt.balasys.hu/zorp-os ubuntu-bionic/zorp-7.0latest main zorp zas zcv zms
The
USERNAMEis the email address of your Balasys Support System technical account, but replace the@character with the-at-string. For example, if your email address is email@example.com, use:deb https://email-at-example.com:PASSWORD@apt.balasys.hu ...
Tip If for some reason you do not want to upgrade your Zorp components to the latest version (for example, your organization requires extensive testing before every upgrade), it is possible to use a selected Zorp release, and download only the security fixes of the operating system. To accomplish this, replace
7latestwith the version number of your selected release. For example, for the Zorp 7.0.1 release write7.0.1:deb [arch=amd64] https://USERNAME:PASSWORD@apt.balasys.hu/zorp-os ubuntu-bionic/zorp-7.0.1 main zorp zas zcv zms
-
Issue the following commands: apt update; apt -u dist-upgrade. The host will download and install the new and updated packages.
Note If for any reason you do not want to install new packages, use the apt update; apt -u upgrade command. That way packages are only upgraded, new packages are not installed. Dependencies that are not installed are listed in the output of the command as kept back packages. (Such packages can be installed by issuing the apt -u dist-update command).
After successfully installing the server–side components, you have to install the management console on the client. The Zorp Management Console (ZMC) is available for Windows and Linux platforms. The Windows version is a single .exe install file. The Linux version is a generic installer (a .run package). Both versions are available on the Zorp Installation DVD. Downloads and updates for ZMC can be downloaded from Balasys downloads.
The Windows and Linux versions are identical in look-and-feel, they are both built with the GTK Toolkit. Therefore, choosing a platform is only a matter of preference.
There are no license restrictions on the number of ZMCs you can install. Therefore, multiple management locations are possible.
| Note |
|---|
It is important to remember that the ZMC machine must always connect to the ZMS host and not the Zorp Firewall itself. The ZMS host must be reachable. The ZMS host, in turn, must be able to communicate with the management agents installed on the Zorp machine. |
The following platforms are supported:
Windows 10 or later (x86, x64)
Ubuntu 18.04 Bionic Beaver (64-bit only)
5.1. Procedure – Installing ZMC on Debian/GNU Linux
Prerequisites:
Before you start installing ZMC, the X graphical tool must already be configured and running on the machine on which you install ZMC.
ZMC requires about 310 MB of free disk space.
Steps:
-
Start the installer for your platform:
zmc-<version_number>-linux-amd64.runfor 64-bit systems
To install ZMC from the command line, navigate to the directory where the installation package is located, and issue the ./zmc-<version_number>-linux-i386.run command.
Make sure that you read and understand the End-User License Agreement. If you have finished reading, click . To accept the End-User License Agreement, click .
Specify the installation directory, then click . The HTML versions of the Zorp Professional 7 Administrator Guide and Zorp Professional 7 Reference Guide documents are also installed automatically.
After the installation is finished, click .
-
To start ZMC, do one of the following:
Desktop: Navigate to the or menu of your desktop environment and start ZMC.
Terminal: In the terminal, enter the following command: ./<installation-directory>/bin/zmc.
5.2. Procedure – Installing ZMC on Microsoft Windows
Purpose:
To install ZMC on Microsoft Windows, complete the following steps.
Prerequisites:
ZMC requires about 30 MB of free disk space. If you also decide to install the documentation, ZMC requires about 300 MB of free disk space.
Make sure you have the necessary rights to perform the installation.
Steps:
Run
zmc-setup-<version-number>.exe.ZMC requires the Microsoft Visual C++ 2010 Redistributable Package to be installed. The ZMC installer automatically installs this package.
Make sure that you read and understand the End-User License Agreement. To accept the End-User License Agreement, click .
The following step is to define the installation path. By default the installer offers
"C:\Program Files\ZMC 7".Optionally, select to install the HTML version of the Zorp Professional 7 Administrator Guide and Zorp Professional 7 Reference Guide documents. Click .
After the installer has completed the above steps, click . You can
To start Zorp Management Console, navigate to the Windows Start menu and start Zorp Management Console from there.
To download the latest Windows version of ZMC, log on to the Balasys website with your personal account (instead of your technical account).
ZMC can be downloaded from Balasys downloads.
| Note |
|---|
Version numbers can differ according to the product development cycle. |
This section describes the installation and configuration of the Zorp Authentication Agent on Microsoft Windows and Linux platforms. The Zorp Authentication Agent has to be installed on every computer having access to authenticated services. The following platforms are supported:
Windows 10 or later (x86, x64)
Ubuntu 18.04 Bionic Beaver (64-bit only)
The agent has two components:
Zorp Authentication Agent Multiplexer: It is a daemon running in the background, accepting the connections coming from Zorp and verifying the SSL certificates of Zorp (if the communication is encrypted). In a multi-user environment the Multiplexer displays the dialog of the Zorp Authentication Agent on the desktop of the user initiating a connection requiring authentication.
Zorp Authentication Agent: This application collects the information required for the authentication, for example, the username, authentication method, password, and so on.
The installers automatically install both components. The components require approximately 10 MB of free hard disk space.
6.1.1. Procedure – Installing the Zorp Authentication Agent on Microsoft Windows
Purpose:
The Zorp Authentication Agent (ZAA) installer is located in the \windows\satyr\ folder of the Zorp CD-ROM, its latest version is also available from the Balasys website.
The following Zorp Authentication Agent installer options are available:
/S Silent mode /D=[path] Set target path /NO_VCREDIST Do not check/install Visual Studio Redistributable /log-mpxd=[yes|no] Enable debug logging of AA multiplexer daemon /log-client=[yes|no] Enable debig logging of AA client
Steps:
-
Place the Zorp CD-ROM into the CD drive and start the
satyr-setup.exefile located in the\windows\satyr\folder.Warning Administrator privileges are required to install the application.
-
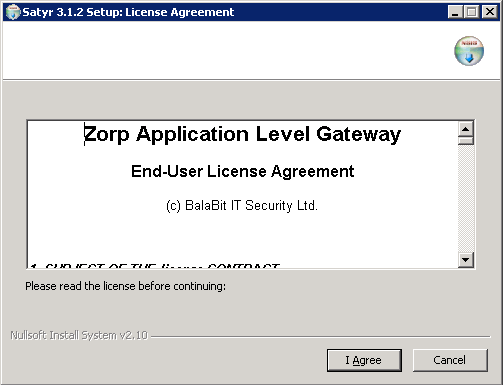
Click to accept the End-User License Agreement, which is displayed after the installer starts. To cancel the installation at any time during the process, click .
-
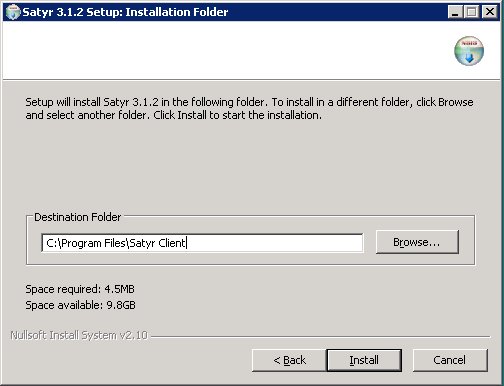
Select the destination folder for the application and click . The default folder in the 64-bit version of Windows is
C:\Program Files (x86)\Satyr Client(in the 32-bit version of Windows, it isC:\Program Files\Satyr Client).
-
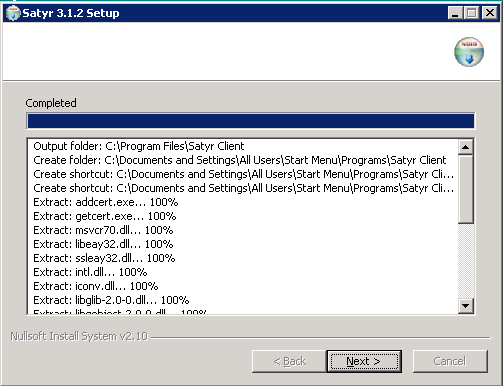
Click to display details about the copied files. The installer copies the required files and registers the service called , which is started after the registration.
-
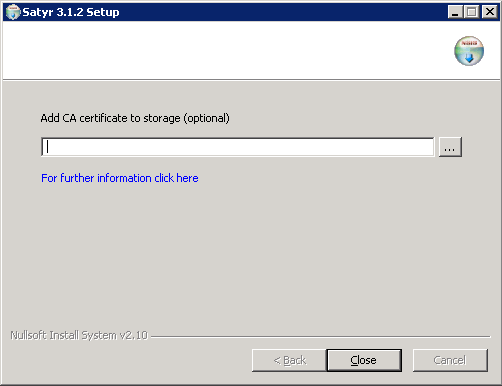
Optional step: Click , select the CA certificate to import, then click to import the CA certificate.
Note For authentication purposes, when Zorp communicates with ZAA, ZAA expects TLS-encrypted communication. For details, see section Section 4.1.1, Registry entries on Microsoft Windows platforms in Zorp Authentication Agent Manual and section Section 4.1, Configuring Zorp Authentication Agent on Microsoft Windows platforms in Zorp Authentication Agent Manual.
If the Zorp Authentication Agent and Zorp communicate through an SSL-encrypted channel (recommended), the certificate of the Certificate Authority (CA) signing the certificates of the Zorp firewalls can be imported to the Zorp Authentication Agent.
Note The CA certificate has to be in
DERformat. It is not necessary to import the certificate during the installation, it can also be done later. For details about encrypting the agent-Zorp authentication, see Section 4.1.3, Configuring SSL connections on Microsoft Windows platforms in Zorp Authentication Agent Manual.
After the installer has completed the above steps, click .
The Zorp Authentication Agent (ZAA) logo is displayed on the system tray, indicating that the application is running. It is also started automatically after each Windows startup.
6.1.2. Procedure – Installing Zorp Authentication Agent with Group Policy Object (GPO) deployment
Prerequisites:
Create the necessary certificates as instructed in the Zorp Professional Administrator Guide in section Procedure 11.3.8.2, Creating certificates in Zorp Professional 7 Administrator Guide.
Set the parameters for the ZAS certificate.
Export the CA certificate signed by ZAS in .der format for the Windows client.
Steps:
Download the .exe format installer. The browser application or the Windows Defender Cloud might send a notification or a warning due to the new and unknown installer program, this can be disregarded.
Install the Windows Client and import the CA certificate during the installation. Reboot the system, if it is necessary.
Define the preferences with the help of the GUI or via the registry.
Test the expected behaviour by initiating traffic.
-
Export the following registries:
-
Export the
HKEY_CURRENT_USER\Software\BalaBit\Satyrregistry to the hlcuzaa.reg file, which contains the user settings for ZAA. The result shall be as follows:Windows Registry Editor Version 5.00 [HKEY_CURRENT_USER\Software\BalaBit] [HKEY_CURRENT_USER\Software\BalaBit\Satyr] "Has preferences"=dword:00000000 "SSL"=dword:00000001 "Automatic"=dword:00000001 "Details"=dword:00000000 "Can Remember"=dword:00000001 "Forget Password"=dword:00000000 "Forget Password Interval"=dword:00000001
-
As ZAA Client is 32 bit executable, and runs on both 32 and 64 bit systems, if the target system is a 32 bit system, as Windows, for example, the following solution is required:
Export the
HKEY_LOCAL_MACHINE\SOFTWARE\BalaBit\Satyr, which contains the ZAA Multiplexer settings, into the hklmzaa32.reg file. The result shall be as follows:Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SOFTWARE\BalaBit] [HKEY_LOCAL_MACHINE\SOFTWARE\BalaBit\Satyr] "InstallLang"="1033"
-
If the target system is a 64 bit system, export the
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\BalaBit\Satyrregistry to the hklmzaa64.reg file, which contains the multiplexer settings. The result shall be as follows:Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\BalaBit] [HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\BalaBit\Satyr] "InstallLang"="1033"
Note If the ZAA Client will be used on both 32 and 64 bit systems, create both registries, adding or removing the WOW6432NODE string to the paths. ZAA will use the corresponding one.
For more details, see 32-bit and 64-bit Application Data in the Registry.
Later at the deployment, the registries can be distributed as duplicated keys on the target system safely, as detailed at the following site: Registry key WOW6432Node may be listed in system registry in 32 bit (x86) version of Windows 7.
The service private certificate store, used by the ZAA Multiplexer, can also be deployed as a registry key.
-
Export the
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\ Cryptography\Services\satyr-mpxdregistry to the hklmzaacert.reg file. The result shall be as follows:Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\Services\satyr-mpxd] [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\Services\satyr-mpxd\ SystemCertificates] [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\Services\satyr-mpxd\ SystemCertificates\MY] [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\Services\satyr-mpxd\ SystemCertificates\MY\Certificates] [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\Services\satyr-mpxd\ SystemCertificates\MY\Certificates\6421DCB8501C2E1F15DB8BD3A94F435C01DB7CD3] "Blob"=hex:03,00,00,00,01,00,00,00,14,00,00,00,64,21,dc,b8,50,1c,2e,1f,15,db,\ ... ... ... ... ... 64,0a,87,e9,45,99,04,9e,28,cb,c0,6c,2a,e5,c7,cb,ce,29,d8,b1,e1
Note Note that there can be several empty paths created by the system automatically, which can be included safely.
For further details on registries, see Section 4.1.1, Registry entries on Microsoft Windows platforms in Zorp Authentication Agent Manual.
As a result, there will be four registries exported.
-
Switch to the GPO administrator system and download the ZAA
msi flavorinstaller and place it in the Windows share where the other remotely installled applications are stored.Continue with the procedures detailed in section Procedure 4.1.5, Configuring Group Policy Object (GPO) deployment in Zorp Authentication Agent Manual
6.2. Procedure – Installing Zorp Authentication Agent on Linux platforms
Purpose:
This section describes the installation of the Zorp Authentication Agent on Ubuntu Linux operating systems.
Steps:
-
Create a mount point for the Zorp installation medium:
sudo mkdir -p /media/cdrom
-
Mount the Zorp installation medium to the previous mount point.
sudo mount /dev/cdrom /media/cdrom -o ro
-
Install the Balasys Gnu Privacy Guard (GPG) keys to allow the checking of Zorp package signatures by APT.
sudo /media/cdrom/install-balasys-archive-key.sh
-
Make sure the following details are added as follows:
-
Add the following lines to the
/etc/apt/auth.conf.d/satyr.conffile:machine apt.balasys.hu login {your username} password {your password} -
Also limit the permissions:
chmod 600 /etc/apt/auth.conf.d/satyr.conf
-
Add the following lines to
/etc/apt/sources.list.d/zorp.listdeb https://apt.balasys.hu/zorp-os ubuntu-bionic/zorp-7.0latest satyr
-
-
Install the Zorp Authentication Agent. Issue the following commands as root:
apt update apt install satyr
The above commands install the
satyr(Zorp Authentication Agent) and thesatyr-mpxd(Zorp Authentication Agent Multiplexer) packages. Zorp Authentication Agent Multiplexer is automatically started after the installation. It can be stopped or started by issuing the
systemctl stop satyr-mpxdorsystemctl start satyr-mpxdcommands, respectively.Zorp Authentication Agent is launched on desktop environment startup. It can be started manually by running
satyr-gtk.
The installation instructions above followed a typical installation cycle. It is a largely automatic process requiring as few user interaction as possible but at the same time allowing the control of installation details. In some cases, however, it may be necessary to manually install components of the system individually by using the standard apt tools.
In particular, apt install can be used to install the following components.
: The Zorp Management Server (ZMS) and its corresponding packages. ZMS — depending on its product license — can be installed on the Zorp firewall host or on a separate machine.(Package name:
zorpproduct-zms): The packages required for a firewall host. (Package name:
zorpproduct-zorp)Zorp URL filter: The package is required for the url filter. (package name:
zorpproduct-urlfilter.: The Zorp Authentication Server (ZAS) enables the authentication of network traffic on the user level at the firewall using password, CryptoCard, S/key, or X.509 methods. Integrating with existing Microsoft Active Directory, LDAP, PAM, and Radius databases is also supported. The module can be installed either together with the Zorp and ZMS modules or separately at a later date. (Package name:
zorpproduct-zas)-
: The Zorp Content Vectoring System (ZCV) is a framework and a uniform interface to manage various built-in and third party content vectoring modules (that is, virus and spam filtering engines). The content vectoring modules to be installed (in addition to the ZCV framework) can be selected from the following list. (Package name:
zorpproduct-zcv)Warning The ZCV framework and the content vectoring modules must be installed on the same host.
: This module contains the libraries and virus signature databases needed for using the ClamAV antivirus engine. (Package name:
zorpproduct-clamav): This module contains the libraries and virus signature databases needed for using the Eset NOD32 antivirus engine. (Package name:
zorpproduct-nod32): This module contains the libraries and databases needed for using the SpamAssassin spam filtering engine. (Package name:
zorpproduct-spamassassin): This module contains the libraries needed for using ModSecurity web application firewall (WAF) engine. (Package name:
zorpproduct-modsecurity)
For example, to install Zorp on a host, use the sudo apt install zorpproduct-zorp command.
If certain packages have been configured or installed incorrectly, you can repeat the configuration of installed packages by running the tasksel ––new-install command from a command prompt. If you want to correct only a single package, use the dpkg-reconfigure <package-name> command (for example, dpkg-reconfigure strongswan).
The following is a list of recommended readings concerning various parts of Zorp administration.
| Note |
|---|
Note that URLs can change over time. The URLs of the online references were valid at the time of writing. |
Guides, manuals, and tutorials for Zorp are available at https://docs.balasys.hu/
Author's name. Title. Place of publication: publisher, year. The Postfix Home Page
Blum, Richard. Postfix. SAMS Publishing, 2001. ISBN: 0672321149
Dent, Kyle D. Postfix: The Definitive Guide. O'Reilly Associates, 2004. ISBN: 0596002122
Albitz, Paul, and Liu, Cricket. DNS and BIND. O'Reilly Associates, 2001. ISBN: 0596001584
NTP Documentation RFC 1305, Network Time Protocol Specification, Implementation and Analysis
Barrett, Daniel J. Ph.D., and Silverman, Richard E. SSH: The Secure Shell The Definitive Guide. O'Reilly Associates, 2001. ISBN: 0596000111
Stevens, W., and Wright, Gary. TCP/IP Illustrated: Volumes 1-3. Addison-Wesley, 2001. ISBN: 0201776316
Mann, Scott. Linux TCP/IP Network Administration. Prentice Hall, 2002. ISBN: 0130322202
Garfinkel, Simson, et al. Practical UNIX and Internet Security, 3/E. O'Reilly Associates, 2003. ISBN: 0596003234
-
The syslog-ng Administrator Guide
(c) Balasys IT Security Ltd.
1.1 This License Contract is entered into by and between Balasys and Licensee and sets out the terms and conditions under which Licensee and/or Licensee's Authorized Subsidiaries may use the Zorp Professional under this License Contract.
In this License Contract, the following words shall have the following meanings:
2.1 Balasys
Company name: Balasys IT Ltd.
Registered office: H-1117 Budapest, Alíz Str. 4.
Company registration number: 01-09-687127
Tax number: HU11996468-2-43
2.2. Words and expressions
Annexed Software
Any third party software that is a not a Balasys Product contained in the install media of the Balasys Product.
Authorized Subsidiary
Any subsidiary organization: (i) in which Licensee possesses more than fifty percent (50%) of the voting power and (ii) which is located within the Territory.
Balasys Product
Any software, hardware or service licensed, sold, or provided by Balasys including any installation, education, support and warranty services, with the exception of the Annexed Software.
License Contract
The present Zorp Professional License Contract.
Product Documentation
Any documentation referring to the Zorp Professional or any module thereof, with special regard to the reference guide, the administration guide, the product description, the installation guide, user guides and manuals.
Protected Hosts
Host computers located in the zones protected by Zorp Professional, that means any computer bounded to network and capable to establish IP connections through the firewall.
Protected Objects
The entire Zorp Professional including all of its modules, all the related Product Documentation; the source code, the structure of the databases, all registered information reflecting the structure of the Zorp Professional and all the adaptation and copies of the Protected Objects that presently exist or that are to be developed in the future, or any product falling under the copyright of Balasys.
Zorp Professional
Application software Balasys Product designed for securing computer networks as defined by the Product Description.
Warranty Period
The period of twelve (12) months from the date of delivery of the Zorp Professional to Licensee.
Territory
The countries or areas specified above in respect of which Licensee shall be entitled to install and/or use Zorp Professional.
Take Over Protocol
The document signed by the parties which contains
a) identification data of Licensee;
b) ordered options of Zorp Professional, number of Protected Hosts and designation of licensed modules thereof;
c) designation of the Territory;
d) declaration of the parties on accepting the terms and conditions of this License Contract; and
e) declaration of Licensee that is in receipt of the install media.
3.1. For the Zorp Professional licensed under this License Contract, Balasys grants to Licensee a non-exclusive,
non-transferable, perpetual license to use such Balasys Product under the terms and conditions of this License Contract and the applicable Take Over Protocol.
3.2. Licensee shall use the Zorp Professional in the in the configuration and in the quantities specified in the Take Over Protocol within the Territory.
3.3. On the install media all modules of the Zorp Professional will be presented, however, Licensee shall not be entitled to use any module which was not licensed to it. Access rights to modules and IP connections are controlled by an "electronic key" accompanying the Zorp Professional.
3.4. Licensee shall be entitled to make one back-up copy of the install media containing the Zorp Professional.
3.5. Licensee shall make available the Protected Objects at its disposal solely to its own employees and those of the Authorized Subsidiaries.
3.6. Licensee shall take all reasonable steps to protect Balasys's rights with respect to the Protected Objects with special regard and care to protecting it from any unauthorized access.
3.7. Licensee shall, in 5 working days, properly answer the queries of Balasys referring to the actual usage conditions of the
Zorp Professional, that may differ or allegedly differs from the license conditions.
3.8. Licensee shall not modify the Zorp Professional in any way, with special regard to the functions inspecting the usage of the software. Licensee shall install the code permitting the usage of the Zorp Professional according to the provisions defined for it by Balasys. Licensee may not modify or cancel such codes. Configuration settings of the Zorp Professional in accordance with the possibilities offered by the system shall not be construed as modification of the software.
3.9. Licensee shall only be entitled to analize the structure of the Balasys Products (decompilation or reverse- engineering) if concurrent operation with a software developed by a third party is necessary, and upon request to supply the information required for concurrent operation Balasys does not provide such information within 60 days from the receipt of such a request. These user actions are limited to parts of the Balasys Product which are necessary for concurrent operation.
3.10. Any information obtained as a result of applying the previous Section
(i) cannot be used for purposes other than concurrent operation with the Balasys Product;
(ii) cannot be disclosed to third parties unless it is necessary for concurrent operation with the Balasys Product;
(iii) cannot be used for the development, production or distribution of a different software which is similar to the BalaSys Product
in its form of expression, or for any other act violating copyright.
3.11. For any Annexed Software contained by the same install media as the Balasys Product, the terms and conditions defined by its copyright owner shall be properly applied. Balasys does not grant any license rights to any Annexed Software.
3.12. Any usage of the Zorp Professional exceeding the limits and restrictions defined in this License Contract shall qualify as material breach of the License Contract.
3.13. The Number of Protected Hosts shall not exceed the amount defined in the Take Over Protocol.
3.14. Licensee shall have the right to obtain and use content updates only if Licensee concludes a maintenance contract that includes such content updates, or if Licensee has otherwise separately acquired the right to obtain and use such content updates. This License Contract does not otherwise permit Licensee to obtain and use content updates.
4.1 Authorized Subsidiaries may also utilize the services of the Zorp Professional under the terms and conditions of this License Contract. Any Authorized Subsidiary utilising any service of the Zorp Professional will be deemed to have accepted the terms and conditions of this License Contract.
5.1. Licensee agrees that Balasys owns all rights, titles, and interests related to the Zorp Professional and all of Balasys's patents, trademarks, trade names, inventions, copyrights, know-how, and trade secrets relating to the design, manufacture, operation or service of the Balasys Products.
5.2. The use by Licensee of any of these intellectual property rights is authorized only for the purposes set forth herein, and upon termination of this License Contract for any reason, such authorization shall cease.
5.3. The Balasys Products are licensed only for internal business purposes in every case, under the condition that such license does not convey any license, expressly or by implication, to manufacture, duplicate or otherwise copy or reproduce any of the Balasys Products.
No other rights than expressly stated herein are granted to Licensee.
5.4. Licensee will take appropriate steps with its Authorized Subsidiaries, as Balasys may request, to inform them of and assure compliance with the restrictions contained in the License Contract.
6.1. Balasys hereby grants to Licensee the non-exclusive right to use the trade marks of the Balasys Products in the Territory in accordance with the terms and for the duration of this License Contract.
6.2. Balasys makes no representation or warranty as to the validity or enforceability of the trade marks, nor as to whether these infringe any intellectual property rights of third parties in the Territory.
7.1. In case of negligent infringement of Balasys's rights with respect to the Zorp Professional, committed by violating the restrictions and limitations defined by this License Contract, Licensee shall pay liquidated damages to Balasys. The amount of the liquidated damages shall be twice as much as the price of the Balasys Product concerned, on Balasys's current Price List.
8.1. Balasys shall pay all damages, costs and reasonable attorney's fees awarded against Licensee in connection with any claim brought against Licensee to the extent that such claim is based on a claim that Licensee's authorized use of the Balasys Product infringes a patent, copyright, trademark or trade secret. Licensee shall notify Balasys in writing of any such claim as soon as Licensee learns of it and shall cooperate fully with Balasys in connection with the defense of that claim. Balasys shall have sole control of that defense (including without limitation the right to settle the claim).
8.2. If Licensee is prohibited from using any Balasys Product due to an infringement claim, or if Balasys believes that any Balasys Product is likely to become the subject of an infringement claim, Balasys shall at its sole option, either: (i) obtain the right for Licensee to continue to use such Balasys Product, (ii) replace or modify the Balasys Product so as to make such Balasys Product non-infringing and substantially comparable in functionality or (iii) refund to Licensee the amount paid for such infringing Balasys Product and provide a pro-rated refund of any unused, prepaid maintenance fees paid by Licensee, in exchange for Licensee's return of such Balasys Product to Balasys.
8.3. Notwithstanding the above, Balasys will have no liability for any infringement claim to the extent that it is based upon:
(i) modification of the Balasys Product other than by Balasys,
(ii) use of the Balasys Product in combination with any product not specifically authorized by Balasys to be combined with the Balasys Product or
(iii) use of the Balasys Product in an unauthorized manner for which it was not designed.
9.1. The number of the Protected Hosts (including the server as one host), the configuration and the modules licensed shall serve as the calculation base of the license fee.
9.2. Licensee acknowlegdes that payment of the license fees is a condition of lawful usage.
9.3. License fees do not contain any installation or post charges.
10.1. Balasys warrants that during the Warranty Period, the optical media upon which the Balasys Product is recorded will not be defective under normal use. Balasys will replace any defective media returned to it, accompanied by a dated proof of purchase, within the Warranty Period at no charge to Licensee. Upon receipt of the allegedly defective Balasys Product, Balasys will at its option, deliver a replacement Balasys Product or Balasys's current equivalent to Licensee at no additional cost. Balasys will bear the delivery charges to Licensee for the replacement Product.
10.2. In case of installation by Balasys, Balasys warrants that during the Warranty Period, the Zorp Professional, under normal use in the operating environment defined by Balasys, and without unauthorized modification, will perform in substantial compliance with the Product Documentation accompanying the Balasys Product, when used on that hardware for which it was installed, in compliance with the provisions of the user manuals and the recommendations of Balasys. The date of the notification sent to Balasys shall qualify as the date of the failure. Licensee shall do its best to mitigate the consequences of that failure. If, during the Warranty Period, the Balasys Product fails to comply with this warranty, and such failure is reported by Licensee to Balasys within the Warranty Period, Balasys's sole obligation and liability for breach of this warranty is, at Balasys's sole option, either:
(i) to correct such failure,
(ii) to replace the defective Balasys Product or
(iii) to refund the license fees paid by Licensee for the applicable Balasys Product.
11.1. EXCEPT AS SET OUT IN THIS LICENSE CONTRACT, BALASYS MAKES NO WARRANTIES OF ANY KIND WITH RESPECT TO THE Zorp Professional. TO THE MAXIMUM EXTENT PERMITTED BY APPLICABLE LAW, BALASYS EXCLUDES ANY OTHER WARRANTIES, INCLUDING BUT NOT LIMITED TO ANY IMPLIED WARRANTIES OF SATISFACTORY QUALITY, MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NON-INFRINGEMENT OF INTELLECTUAL PROPERTY RIGHTS.
12.1. SOME STATES AND COUNTRIES, INCLUDING MEMBER COUNTRIES OF THE EUROPEAN UNION, DO NOT ALLOW THE LIMITATION OR EXCLUSION OF LIABILITY FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES AND, THEREFORE, THE FOLLOWING LIMITATION OR EXCLUSION MAY NOT APPLY TO THIS LICENSE CONTRACT IN THOSE STATES AND COUNTRIES. TO THE MAXIMUM EXTENT PERMITTED BY APPLICABLE LAW AND REGARDLESS OF WHETHER ANY REMEDY SET OUT IN THIS LICENSE CONTRACT FAILS OF ITS ESSENTIAL PURPOSE, IN NO EVENT SHALL BALASYS BE LIABLE TO LICENSEE FOR ANY SPECIAL, CONSEQUENTIAL, INDIRECT OR SIMILAR DAMAGES OR LOST PROFITS OR LOST DATA ARISING OUT OF THE USE OR INABILITY TO USE THE Zorp Professional EVEN IF BALASYS HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
12.2. IN NO CASE SHALL BALASYS'S TOTAL LIABILITY UNDER THIS LICENSE CONTRACT EXCEED THE FEES PAID BY LICENSEE FOR THE Zorp Professional LICENSED UNDER THIS LICENSE CONTRACT.
13.1. This License Contract shall come into effect on the date of signature of the Take Over Protocol by the duly authorized
representatives of the parties.
13.2. Licensee may terminate the License Contract at any time by written notice sent to Balasys and by simultaneously destroying all copies of the Zorp Professional licensed under this License Contract.
13.3. Balasys may terminate this License Contract with immediate effect by written notice to Licensee, if Licensee is in material or persistent breach of the License Contract and either that breach is incapable of remedy or Licensee shall have failed to remedy that breach within 30 days after receiving written notice requiring it to remedy that breach.
14.1. Save as expressly provided in this License Contract, no amendment or variation of this License Contract shall be effective unless in writing and signed by a duly authorised representative of the parties to it.
15.1. The failure of a party to exercise or enforce any right under this License Contract shall not be deemed to be a waiver of that right nor operate to bar the exercise or enforcement of it at any time or times thereafter.
16.1. If any part of this License Contract becomes invalid, illegal or unenforceable, the parties shall in such an event negotiate in good faith in order to agree on the terms of a mutually satisfactory provision to be substituted for the invalid, illegal or unenforceable
provision which as nearly as possible validly gives effect to their intentions as expressed in this License Contract.
17.1. Any notice required to be given pursuant to this License Contract shall be in writing and shall be given by delivering the notice by hand, or by sending the same by prepaid first class post (airmail if to an address outside the country of posting) to the address of the relevant party set out in this License Contract or such other address as either party notifies to the other from time to time. Any notice given according to the above procedure shall be deemed to have been given at the time of delivery (if delivered by hand) and when received (if sent by post).
18.1. Headings are for convenience only and shall be ignored in interpreting this License Contract.
18.2. This License Contract and the rights granted in this License Contract may not be assigned, sublicensed or otherwise transferred in whole or in part by Licensee without Balasys's prior written consent. This consent shall not be unreasonably withheld or delayed.
18.3. An independent third party auditor, reasonably acceptable to Balasys and Licensee, may upon reasonable notice to Licensee and during normal business hours, but not more often than once each year, inspect Licensee's relevant records in order to confirm that usage of the Zorp Professional complies with the terms and conditions of this License Contract. Balasys shall bear the costs of such audit. All audits shall be subject to the reasonable safety and security policies and procedures of Licensee.
18.4. This License Contract constitutes the entire agreement between the parties with regard to the subject matter hereof. Any modification of this License Contract must be in writing and signed by both parties.
THE WORK (AS DEFINED BELOW) IS PROVIDED UNDER THE TERMS OF THIS CREATIVE COMMONS PUBLIC LICENSE ("CCPL" OR "LICENSE"). THE WORK IS PROTECTED BY COPYRIGHT AND/OR OTHER APPLICABLE LAW. ANY USE OF THE WORK OTHER THAN AS AUTHORIZED UNDER THIS LICENSE OR COPYRIGHT LAW IS PROHIBITED. BY EXERCISING ANY RIGHTS TO THE WORK PROVIDED HERE, YOU ACCEPT AND AGREE TO BE BOUND BY THE TERMS OF THIS LICENSE. TO THE EXTENT THIS LICENSE MAY BE CONSIDERED TO BE A CONTRACT, THE LICENSOR GRANTS YOU THE RIGHTS CONTAINED HERE IN CONSIDERATION OF YOUR ACCEPTANCE OF SUCH TERMS AND CONDITIONS.
-
Definitions
"Adaptation" means a work based upon the Work, or upon the Work and other pre-existing works, such as a translation, adaptation, derivative work, arrangement of music or other alterations of a literary or artistic work, or phonogram or performance and includes cinematographic adaptations or any other form in which the Work may be recast, transformed, or adapted including in any form recognizably derived from the original, except that a work that constitutes a Collection will not be considered an Adaptation for the purpose of this License. For the avoidance of doubt, where the Work is a musical work, performance or phonogram, the synchronization of the Work in timed-relation with a moving image ("synching") will be considered an Adaptation for the purpose of this License.
"Collection" means a collection of literary or artistic works, such as encyclopedias and anthologies, or performances, phonograms or broadcasts, or other works or subject matter other than works listed in Section 1(f) below, which, by reason of the selection and arrangement of their contents, constitute intellectual creations, in which the Work is included in its entirety in unmodified form along with one or more other contributions, each constituting separate and independent works in themselves, which together are assembled into a collective whole. A work that constitutes a Collection will not be considered an Adaptation (as defined above) for the purposes of this License.
"Distribute" means to make available to the public the original and copies of the Work through sale or other transfer of ownership.
"Licensor" means the individual, individuals, entity or entities that offer(s) the Work under the terms of this License.
"Original Author" means, in the case of a literary or artistic work, the individual, individuals, entity or entities who created the Work or if no individual or entity can be identified, the publisher; and in addition (i) in the case of a performance the actors, singers, musicians, dancers, and other persons who act, sing, deliver, declaim, play in, interpret or otherwise perform literary or artistic works or expressions of folklore; (ii) in the case of a phonogram the producer being the person or legal entity who first fixes the sounds of a performance or other sounds; and, (iii) in the case of broadcasts, the organization that transmits the broadcast.
"Work" means the literary and/or artistic work offered under the terms of this License including without limitation any production in the literary, scientific and artistic domain, whatever may be the mode or form of its expression including digital form, such as a book, pamphlet and other writing; a lecture, address, sermon or other work of the same nature; a dramatic or dramatico-musical work; a choreographic work or entertainment in dumb show; a musical composition with or without words; a cinematographic work to which are assimilated works expressed by a process analogous to cinematography; a work of drawing, painting, architecture, sculpture, engraving or lithography; a photographic work to which are assimilated works expressed by a process analogous to photography; a work of applied art; an illustration, map, plan, sketch or three-dimensional work relative to geography, topography, architecture or science; a performance; a broadcast; a phonogram; a compilation of data to the extent it is protected as a copyrightable work; or a work performed by a variety or circus performer to the extent it is not otherwise considered a literary or artistic work.
"You" means an individual or entity exercising rights under this License who has not previously violated the terms of this License with respect to the Work, or who has received express permission from the Licensor to exercise rights under this License despite a previous violation.
"Publicly Perform" means to perform public recitations of the Work and to communicate to the public those public recitations, by any means or process, including by wire or wireless means or public digital performances; to make available to the public Works in such a way that members of the public may access these Works from a place and at a place individually chosen by them; to perform the Work to the public by any means or process and the communication to the public of the performances of the Work, including by public digital performance; to broadcast and rebroadcast the Work by any means including signs, sounds or images.
"Reproduce" means to make copies of the Work by any means including without limitation by sound or visual recordings and the right of fixation and reproducing fixations of the Work, including storage of a protected performance or phonogram in digital form or other electronic medium.
Fair Dealing Rights. Nothing in this License is intended to reduce, limit, or restrict any uses free from copyright or rights arising from limitations or exceptions that are provided for in connection with the copyright protection under copyright law or other applicable laws.
-
License Grant. Subject to the terms and conditions of this License, Licensor hereby grants You a worldwide, royalty-free, non-exclusive, perpetual (for the duration of the applicable copyright) license to exercise the rights in the Work as stated below:
to Reproduce the Work, to incorporate the Work into one or more Collections, and to Reproduce the Work as incorporated in the Collections; and,
to Distribute and Publicly Perform the Work including as incorporated in Collections.
The above rights may be exercised in all media and formats whether now known or hereafter devised. The above rights include the right to make such modifications as are technically necessary to exercise the rights in other media and formats, but otherwise you have no rights to make Adaptations. Subject to 8(f), all rights not expressly granted by Licensor are hereby reserved, including but not limited to the rights set forth in Section 4(d).
-
Restrictions. The license granted in Section 3 above is expressly made subject to and limited by the following restrictions:
You may Distribute or Publicly Perform the Work only under the terms of this License. You must include a copy of, or the Uniform Resource Identifier (URI) for, this License with every copy of the Work You Distribute or Publicly Perform. You may not offer or impose any terms on the Work that restrict the terms of this License or the ability of the recipient of the Work to exercise the rights granted to that recipient under the terms of the License. You may not sublicense the Work. You must keep intact all notices that refer to this License and to the disclaimer of warranties with every copy of the Work You Distribute or Publicly Perform. When You Distribute or Publicly Perform the Work, You may not impose any effective technological measures on the Work that restrict the ability of a recipient of the Work from You to exercise the rights granted to that recipient under the terms of the License. This Section 4(a) applies to the Work as incorporated in a Collection, but this does not require the Collection apart from the Work itself to be made subject to the terms of this License. If You create a Collection, upon notice from any Licensor You must, to the extent practicable, remove from the Collection any credit as required by Section 4(c), as requested.
You may not exercise any of the rights granted to You in Section 3 above in any manner that is primarily intended for or directed toward commercial advantage or private monetary compensation. The exchange of the Work for other copyrighted works by means of digital file-sharing or otherwise shall not be considered to be intended for or directed toward commercial advantage or private monetary compensation, provided there is no payment of any monetary compensation in connection with the exchange of copyrighted works.
If You Distribute, or Publicly Perform the Work or Collections, You must, unless a request has been made pursuant to Section 4(a), keep intact all copyright notices for the Work and provide, reasonable to the medium or means You are utilizing: (i) the name of the Original Author (or pseudonym, if applicable) if supplied, and/or if the Original Author and/or Licensor designate another party or parties (for example a sponsor institute, publishing entity, journal) for attribution ("Attribution Parties") in Licensor's copyright notice, terms of service or by other reasonable means, the name of such party or parties; (ii) the title of the Work if supplied; (iii) to the extent reasonably practicable, the URI, if any, that Licensor specifies to be associated with the Work, unless such URI does not refer to the copyright notice or licensing information for the Work. The credit required by this Section 4(c) may be implemented in any reasonable manner; provided, however, that in the case of a Collection, at a minimum such credit will appear, if a credit for all contributing authors of Collection appears, then as part of these credits and in a manner at least as prominent as the credits for the other contributing authors. For the avoidance of doubt, You may only use the credit required by this Section for the purpose of attribution in the manner set out above and, by exercising Your rights under this License, You may not implicitly or explicitly assert or imply any connection with, sponsorship or endorsement by the Original Author, Licensor and/or Attribution Parties, as appropriate, of You or Your use of the Work, without the separate, express prior written permission of the Original Author, Licensor and/or Attribution Parties.
-
For the avoidance of doubt:
Non-waivable Compulsory License Schemes. In those jurisdictions in which the right to collect royalties through any statutory or compulsory licensing scheme cannot be waived, the Licensor reserves the exclusive right to collect such royalties for any exercise by You of the rights granted under this License;
Waivable Compulsory License Schemes. In those jurisdictions in which the right to collect royalties through any statutory or compulsory licensing scheme can be waived, the Licensor reserves the exclusive right to collect such royalties for any exercise by You of the rights granted under this License if Your exercise of such rights is for a purpose or use which is otherwise than noncommercial as permitted under Section 4(b) and otherwise waives the right to collect royalties through any statutory or compulsory licensing scheme; and,
Voluntary License Schemes. The Licensor reserves the right to collect royalties, whether individually or, in the event that the Licensor is a member of a collecting society that administers voluntary licensing schemes, via that society, from any exercise by You of the rights granted under this License that is for a purpose or use which is otherwise than noncommercial as permitted under Section 4(b).
Except as otherwise agreed in writing by the Licensor or as may be otherwise permitted by applicable law, if You Reproduce, Distribute or Publicly Perform the Work either by itself or as part of any Collections, You must not distort, mutilate, modify or take other derogatory action in relation to the Work which would be prejudicial to the Original Author's honor or reputation.
Representations, Warranties and Disclaimer UNLESS OTHERWISE MUTUALLY AGREED BY THE PARTIES IN WRITING, LICENSOR OFFERS THE WORK AS-IS AND MAKES NO REPRESENTATIONS OR WARRANTIES OF ANY KIND CONCERNING THE WORK, EXPRESS, IMPLIED, STATUTORY OR OTHERWISE, INCLUDING, WITHOUT LIMITATION, WARRANTIES OF TITLE, MERCHANTIBILITY, FITNESS FOR A PARTICULAR PURPOSE, NONINFRINGEMENT, OR THE ABSENCE OF LATENT OR OTHER DEFECTS, ACCURACY, OR THE PRESENCE OF ABSENCE OF ERRORS, WHETHER OR NOT DISCOVERABLE. SOME JURISDICTIONS DO NOT ALLOW THE EXCLUSION OF IMPLIED WARRANTIES, SO SUCH EXCLUSION MAY NOT APPLY TO YOU.
Limitation on Liability. EXCEPT TO THE EXTENT REQUIRED BY APPLICABLE LAW, IN NO EVENT WILL LICENSOR BE LIABLE TO YOU ON ANY LEGAL THEORY FOR ANY SPECIAL, INCIDENTAL, CONSEQUENTIAL, PUNITIVE OR EXEMPLARY DAMAGES ARISING OUT OF THIS LICENSE OR THE USE OF THE WORK, EVEN IF LICENSOR HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
-
Termination
This License and the rights granted hereunder will terminate automatically upon any breach by You of the terms of this License. Individuals or entities who have received Collections from You under this License, however, will not have their licenses terminated provided such individuals or entities remain in full compliance with those licenses. Sections 1, 2, 5, 6, 7, and 8 will survive any termination of this License.
Subject to the above terms and conditions, the license granted here is perpetual (for the duration of the applicable copyright in the Work). Notwithstanding the above, Licensor reserves the right to release the Work under different license terms or to stop distributing the Work at any time; provided, however that any such election will not serve to withdraw this License (or any other license that has been, or is required to be, granted under the terms of this License), and this License will continue in full force and effect unless terminated as stated above.
-
Miscellaneous
Each time You Distribute or Publicly Perform the Work or a Collection, the Licensor offers to the recipient a license to the Work on the same terms and conditions as the license granted to You under this License.
If any provision of this License is invalid or unenforceable under applicable law, it shall not affect the validity or enforceability of the remainder of the terms of this License, and without further action by the parties to this agreement, such provision shall be reformed to the minimum extent necessary to make such provision valid and enforceable.
No term or provision of this License shall be deemed waived and no breach consented to unless such waiver or consent shall be in writing and signed by the party to be charged with such waiver or consent.
This License constitutes the entire agreement between the parties with respect to the Work licensed here. There are no understandings, agreements or representations with respect to the Work not specified here. Licensor shall not be bound by any additional provisions that may appear in any communication from You. This License may not be modified without the mutual written agreement of the Licensor and You.
The rights granted under, and the subject matter referenced, in this License were drafted utilizing the terminology of the Berne Convention for the Protection of Literary and Artistic Works (as amended on September 28, 1979), the Rome Convention of 1961, the WIPO Copyright Treaty of 1996, the WIPO Performances and Phonograms Treaty of 1996 and the Universal Copyright Convention (as revised on July 24, 1971). These rights and subject matter take effect in the relevant jurisdiction in which the License terms are sought to be enforced according to the corresponding provisions of the implementation of those treaty provisions in the applicable national law. If the standard suite of rights granted under applicable copyright law includes additional rights not granted under this License, such additional rights are deemed to be included in the License; this License is not intended to restrict the license of any rights under applicable law.