| Megjegyzés |
|---|
|
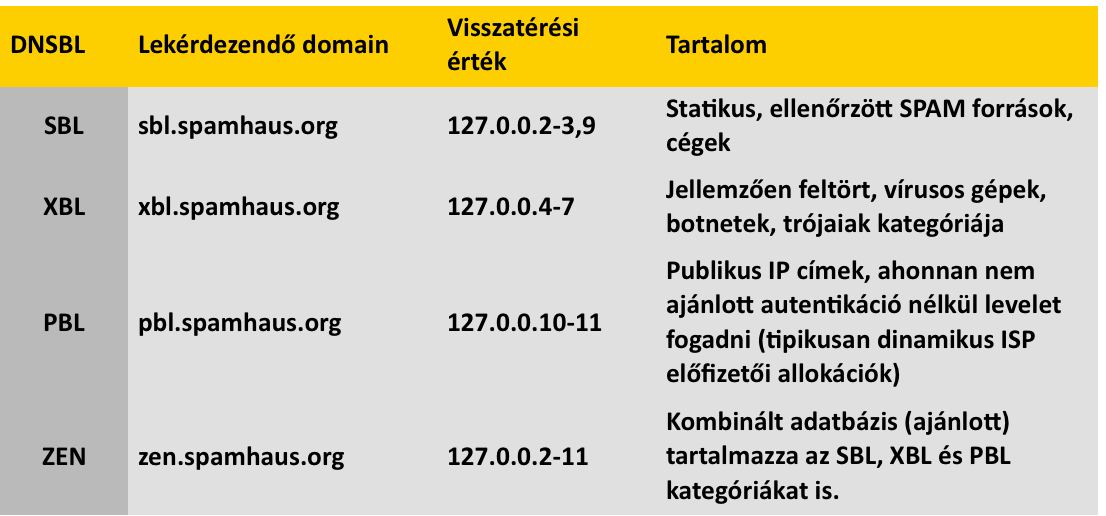
SBL: Spamhouse Block List XBL: Exploits Block List PBL: Policy Block List ZEN: Zen |
Számunkra az SBL és XBL osztályok az érdekesek. A biztosan SPAM küldőket letiltjuk.
Az erre használható Zorp-6-os proxy osztály:
class RBLSpamFilterSmtpProxy(SmtpProxy):
def config(self):
super(RBLSpamFilterSmtpProxy, self).config()
self.request["MAIL"] = (SMTP_REQ_POLICY, self.checkRBL)
def checkRBL(self, cmd, param):
proxyLog(self, CORE_POLICY, 5, "Starting RBL checking.")
l = string.split(self.session.client_address.ip_s, ".")
l.reverse()
lookup_host = string.join(l, ".") + "." + self.rbl_domain
proxyLog(self, CORE_POLICY, 5, "Looking up RBL; query_string='%s'", lookup_host)
try:
addr = socket.gethostbyname(lookup_host)
except socket.error:
addr = None
if addr:
if '127.0.0.2' in addr or '127.0.0.3' in addr or '127.0.0.9' in addr:
proxyLog(self, CORE_POLICY, 2, "Address in Direct RBL, rejecting; ip='%s', rbl='%s', response='%s'",
(self.session.client_address.ip_s, self.rbl_domain, addr))
return SMTP_REQ_ABORT
elif '127.0.0.4' in addr or '127.0.0.5' in addr or '127.0.0.6' in addr or '127.0.0.7' in addr:
proxyLog(self, CORE_POLICY, 2, "Address in XBL RBL, rejecting; ip='%s', rbl='%s', response='%s'",
(self.session.client_address.ip_s, self.rbl_domain, addr))
return SMTP_REQ_ABORT
else:
return SMTP_REQ_ACCEPT
"BlackList"""
MatcherPolicy(name="EmailBlackList", matcher=RegexpFileMatcher(match_fname="/etc/zorp/email-blacklist",
ignore_fname="/etc/zorp/email-blacklist.ignore"))
MatcherPolicy(name="InterSMTPRecipientMatcher", matcher=RegexpFileMatcher(match_fname="/etc/zorp/email-recipient",
ignore_fname="/etc/zorp/email-recipient.ignore"))
class InterSmtpProxy(RBLSpamFilterSmtpProxy):
def config(self):
RBLSpamFilterSmtpProxy.config(self)
self.request_stack["*"]=(SMTP_STK_MIME,
(Z_STACK_PROVIDER, "LocalZCV", "InterSMTPScanning"))
self.relay_domains=("saját domain helye.hu", )
self.sender_matcher="EmailBlackList"
self.recipient_matcher="InterSMTPRecipientMatcher"
self.rbl_domain="zen.spamhaus.org"
self.max_request_length=1024
self.unconnected_response_code=451
self.require_crlf=FALSE
self.relay_check=TRUE
self.error_soft=TRUE
A proxyt érdemes az SMTP autentikációt ellenőrző proxyval kombinálni, amennyiben a belső szerver ezt támogatja.
class AuthRelaySmtpProxy(SmtpProxy):
def config(self):
SmtpProxy.config(self)
self.response["AUTH", "235"] = (SMTP_RSP_POLICY, self.authsucc)
def authsucc(self, cmd, cmd_param, rsp, rsp_param):
self.relay_check = FALSE
log(None, CORE_POLICY, 3, "Relay-check disabled after successful auth;
rsp='%s'; rsp_param='%s'", (rsp,rsp_param,))
return SMTP_RSP_ACCEPTPublished on július 28, 2022
© BalaSys IT Ltd.
Küldje el nekünk észrevételeit: support@balasys.hu